OverTheWire Natas Level 1 → 2 tutorial!!
Login
URL: http://natas2.natas.labs.overthewire.org
Credentials: natas2:TguMNxKo1DSa1tujBLuZJnDUlCcUAPlI
💡 Tip: you could also log in with
curl -u natas2:<password> <URL>, but browser navigation is easier here.
Task
The page looks almost empty, but the HTML source reveals an image reference:
<img src="files/pixel.png">
If there’s an image under /files/, maybe there are more files there. Let’s check the directory.
A little bit of Theory
- Relative URLs like
files/pixel.pngpoint to a subdirectory of the site. Removing the filename often exposes a folder path. - Some servers allow directory listing, which lets you browse everything inside.
- Plain text files (like
users.txt) can be opened directly in the browser.
Further reading:
Solution
-
Open the page source (Ctrl+U / ⌥+⌘+U) and notice
files/pixel.png. -
Remove the filename and visit: http://natas2.natas.labs.overthewire.org/files/
You’ll see a directory listing with
pixel.pngandusers.txt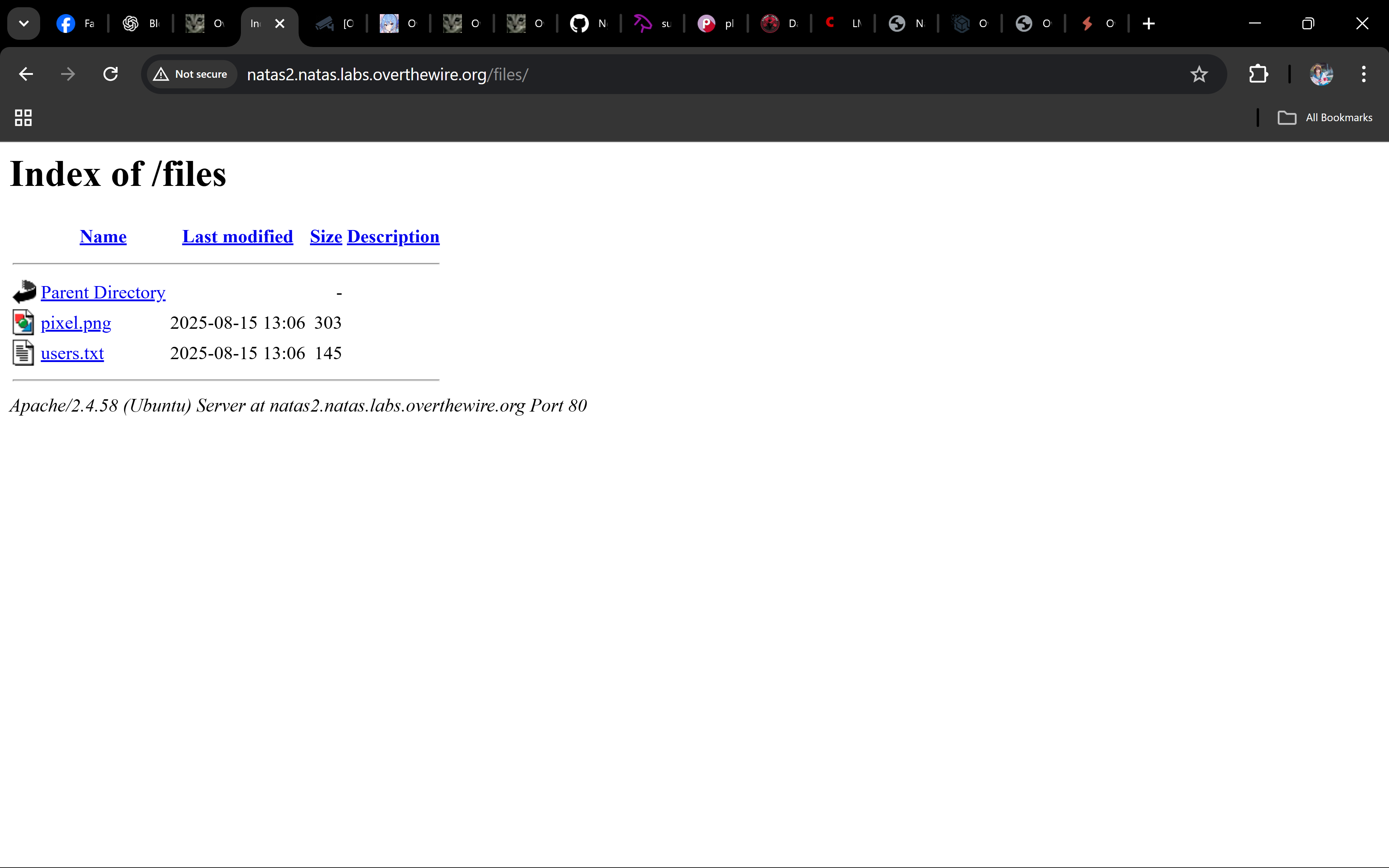
-
Click
users.txtand read its contents: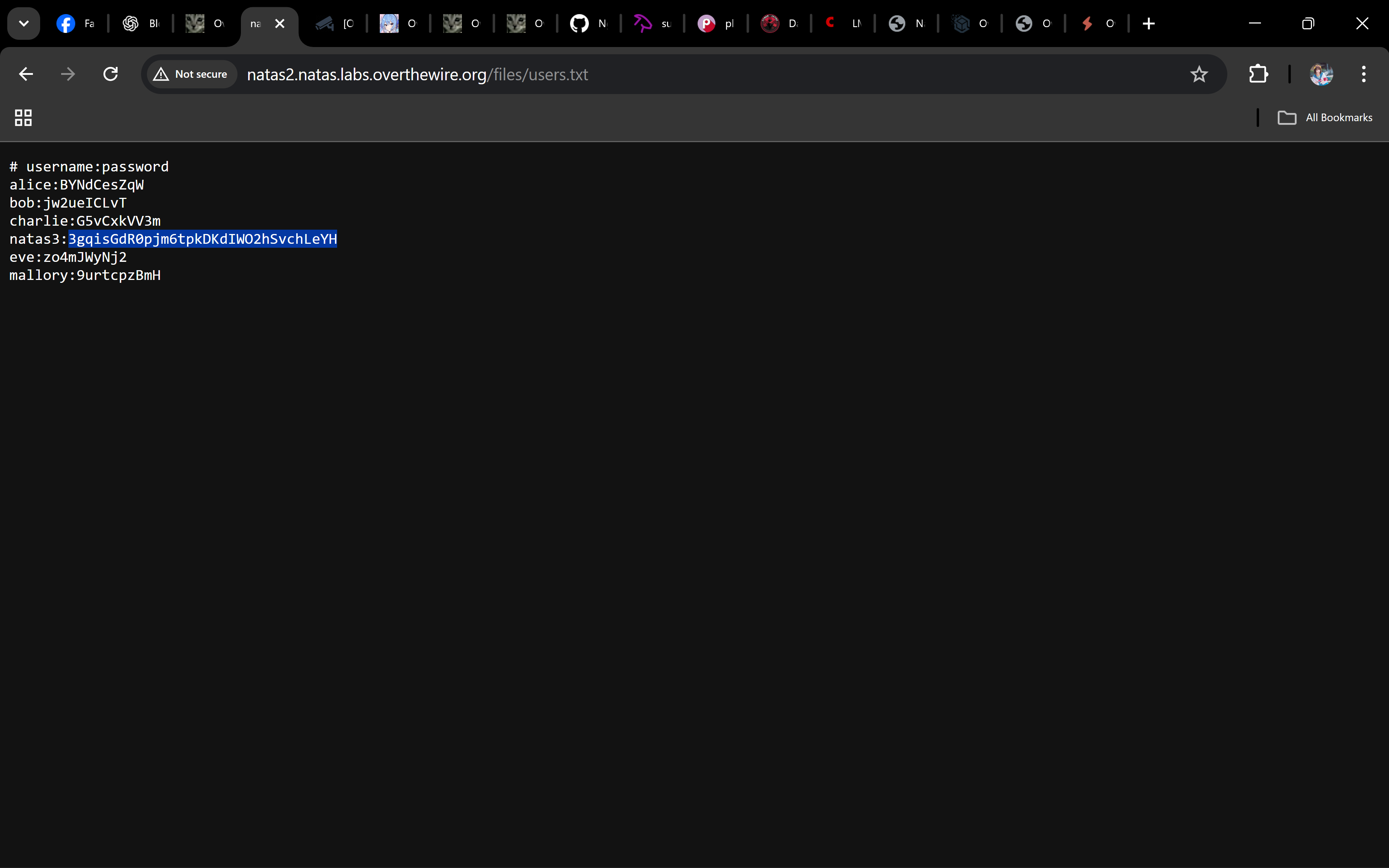
Inside, one of the lines reveals the password for natas3.
-
Use that password to log in to Level 3:
- URL: http://natas3.natas.labs.overthewire.org
- Username:
natas3 - Password: (the one you just found)
Password
3gqisGdR0pjm6tpkDKdIWO2hSvchLeYH
Troubleshooting
- Getting
403/404? → Ensure the path ends with/files/. - Can’t see the listing? → Some browsers render differently; try Chrome/Firefox.
- Password not obvious? → Look for the line beginning with
natas3:.
Nice! 🎉 You followed a hidden relative path, explored a directory, and grabbed the password for natas3.
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


