OverTheWire Narnia — Complete Walkthrough Index
OverTheWire Narnia — Complete Walkthrough Index
Halloo SuiiKawaii dessu!! Welcome back. This page is the master index for my Narnia walkthroughs — today we’re diving into classic binary exploitation on Linux: overflows, format strings, env tricks, and SUID shells 🗣️🔥🔥🔥!!

Introduction
If you’re aiming at pwn / binary exploitation, OverTheWire (open in new tab) has a timeless mini‑course called Narnia.
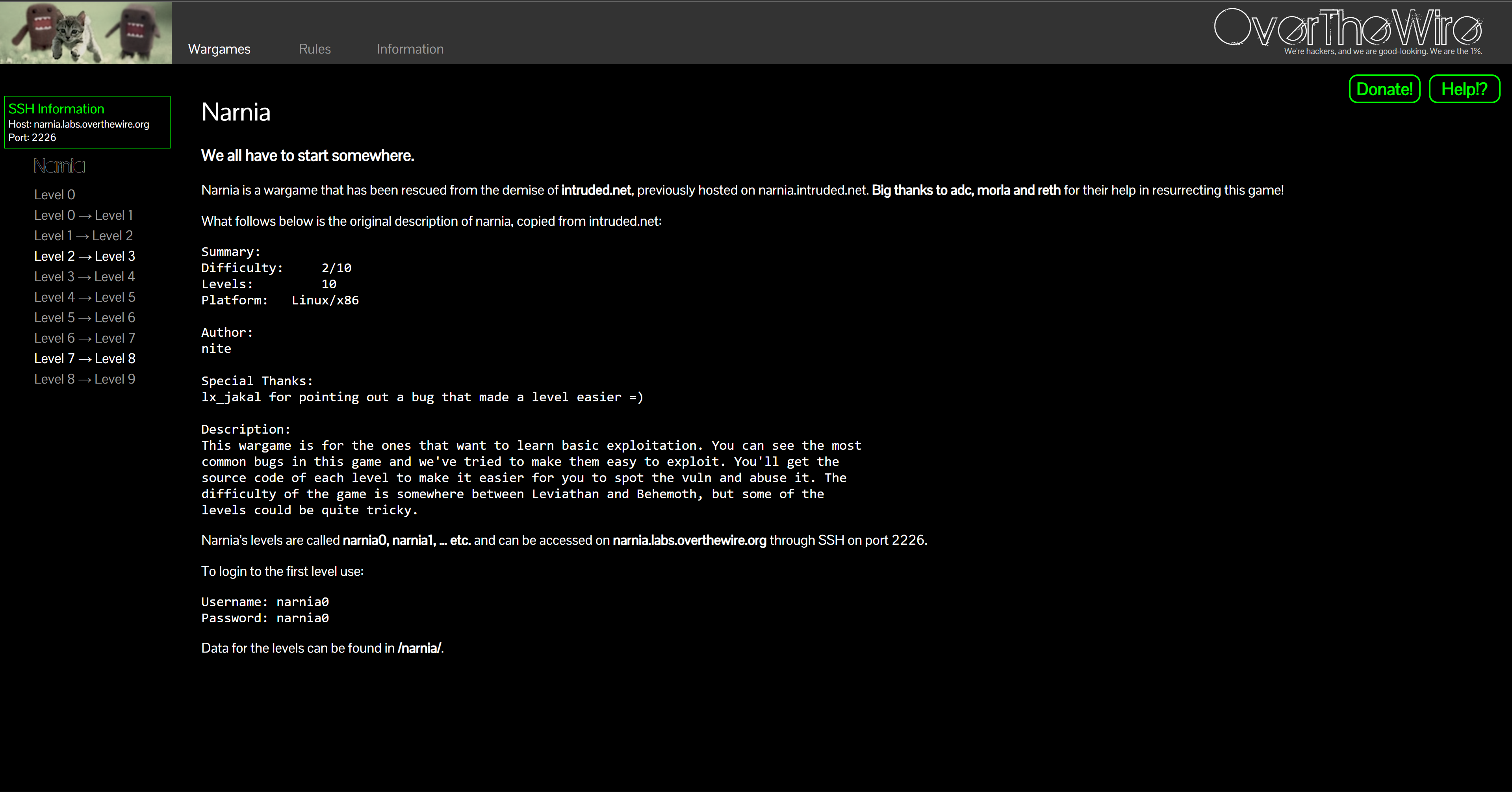
Narnia introduces core exploitation ideas in small, digestible levels:
- Stack overflows & endianness
- Shellcode via environment variables
- Format string bugs (read/write memory)
- SUID privilege escalation patterns
By the end, you’ll be comfortable reading C sources, spotting bug patterns, and turning them into shells.
About This Series
Each level has its own post with:
- Login / Setup — how to connect and where binaries live
- Task — the original OTW prompt
- Source Review — highlight the exact lines that matter
- Exploit — step‑by‑step with copy‑paste commands
My goal isn’t to dump passwords; it’s to teach you to think like a debugger: reproduce → inspect → exploit → verify.
How to Play Narnia (and actually learn)
- Read the C source carefully; mark dangerous calls (
gets,strcpy,scanf,printfwith user input). - Rebuild mentally: where does data go? how big are buffers? what’s next on the stack?
- Use tooling:
strings,objdump -d,file,ltrace,strace,gdb(pwndbg/peda),readelf -a. - Remember endianness and alignment.
- Keep a lab notebook: offsets, payloads, crash notes, and successful runs.
Pro tip: keep stdin open after spawning shells (e.g., ...; cat) so your SUID shell stays interactive.
Levels Index (0 → 9)
Each link opens in a new tab. The one‑liner tells you the main idea.
-
🐣 Level 0 — Setup & Tour
Read post → — SSH in, find/narnia/binaries & sources. -
💥 Level 0 → 1 — Tiny Stack Overflow
Read post → — Overflow a small buffer and flip a sentinel value to win a shell. -
🥚 Level 1 → 2 — Env Var + Shellcode
Read post → — Put shellcode inEGGand jump to it from a SUID binary. -
🧱 Level 2 → 3 — Safer‑looking, Still Overflow
Read post → — Classic overflow with “harmless” functions; control execution reliably. -
🧾 Level 3 → 4 — Format String (Intro)
Read post → — Leak addresses / memory with%x/%s. -
🪄 Level 4 → 5 — Format String (Write Primitive)
Read post → — Use%nto write and redirect control flow. -
🧗 Level 5 → 6 — ret2libc Basics
Read post → — Callsystem("/bin/sh")with libc gadgets. -
🧰 Level 6 → 7 — Off‑by‑One & Stack Layout
Read post → — A single byte can shift control; mind saved registers. -
🗝️ Level 7 → 8 — PATH / Command Injection Quirk
Read post → — Abuse insecuresystem()/ PATH resolution for SUID escalation. -
🛡️ Level 8 → 9 — ASLR Dance & Final Shell
Read post → — Combine leaks + calculated addresses to pop the last shell.
Conclusion
There are tons of Narnia guides online, but this series is my workflow: minimal theory, maximum reproducibility, and just enough tooling to build intuition.
Finishing Narnia levels gives you a real pwn foundation:
- You can read C sources and predict bugs.
- You know how to prove a bug with small, surgical payloads.
- SUID + shellcode + format strings stop being scary — they’re just puzzles.
Next adventures:
- Leviathan (Linux privilege tricks)
- Krypton (crypto)
- Platforms: pwn.college / TryHackMe / Hack The Box
Keep tinkering, keep notes, and keep it legal. You got this 💪
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


