OverTheWire Leviathan Level 6 → 7 tutorial!!
Login
Log in as leviathan6 using the password from Level 5 → 6.
ssh leviathan6@leviathan.labs.overthewire.org -p 2223
# password: szo7HDB88w
Why? Each Leviathan level is a different UNIX user. To solve 6 → 7, you must be
leviathan6.
Task
There is a SUID binary in the home directory that expects a 4-digit code. Find the correct code and read the password for leviathan7.
A little bit of Theory
- SUID: the program runs with the owner’s privileges (here:
leviathan7) once it accepts the correct code. - Disassembly: looking at the program’s instructions lets you see what it compares your input against.
-
GDB basics you’ll use:
gdb --args ./prog arg1— start with argumentsdisassemble main— view assembly ofmainbreak *0xADDR— set a breakpoint at an addressrun, theninfo registers— run to BP, view registersx 0xADDR/x/wx 0xADDR— examine memory at addressprint/d 0xHEX— print a hex value in decimal
Further reading:
Solution
-
List the directory
ls -laWhy? Confirm there’s a SUID binary and who owns it.
Example:
-r-sr-x--- 1 leviathan7 leviathan6 7452 Aug 26 2019 leviathan6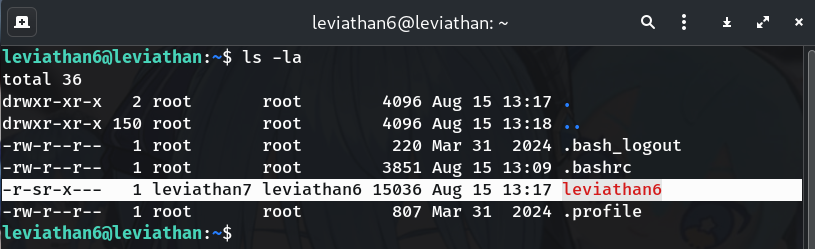
-
Try the binary with a dummy code
./leviathan6 # usage: ./leviathan6 <4 digit code> ./leviathan6 0000 # WrongWhy? Establish baseline behavior and argument format.
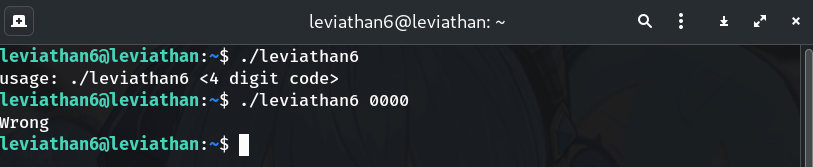
-
Launch GDB with arguments
gdb --args ./leviathan6 0000Why? We’ll run under the debugger so we can pause at the comparison.
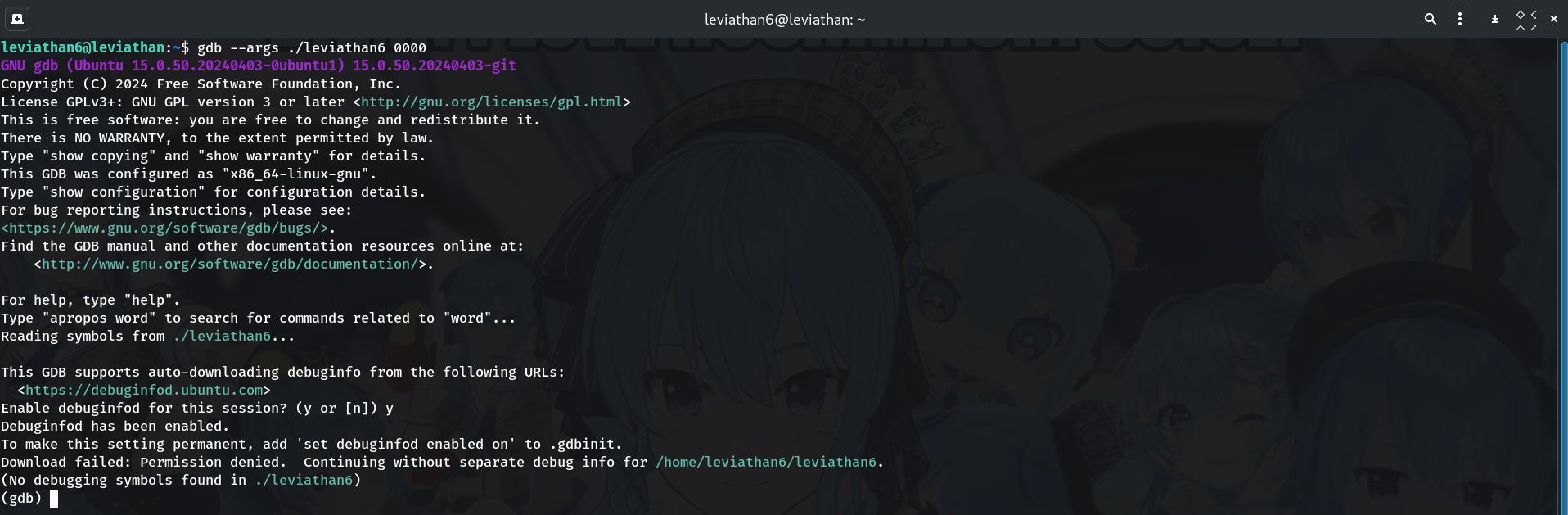
-
Disassemble
mainto find the compareIn GDB:
(gdb) disassemble mainLook for the sequence that parses your arg (often
atoi@plt) and then acmpagainst a constant on the stack (e.g.,cmp %eax,-0xc(%ebp)), followed by a conditional jump.Why? The constant it compares to is the correct code.
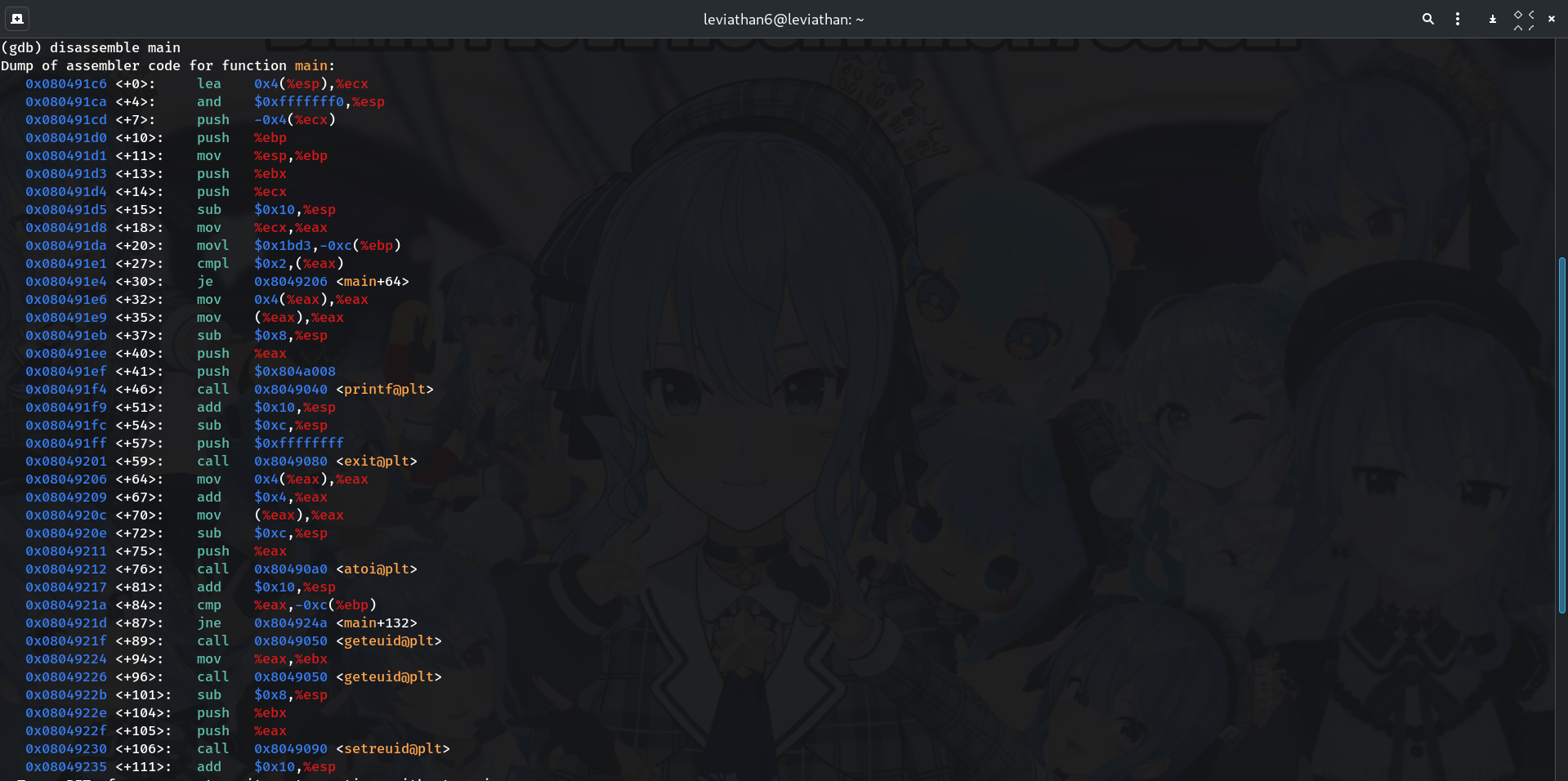

-
Break at the
cmpand run(gdb) break *0x0804922a # address of the cmp (from your disassembly) (gdb) runWhy? Stop exactly before the decision is made.
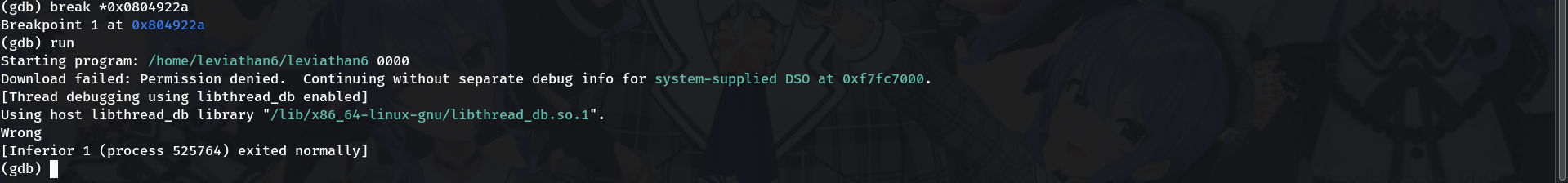
-
Inspect registers and the compared value
(gdb) info registers # note EAX (your input after atoi) (gdb) print $ebp-0xc $1 = (void *) 0xffffd4cc (gdb) x/wx 0xffffd4cc 0xffffd4cc: 0x00001bd3 (gdb) print/d 0x00001bd3 $2 = 7123Why? The constant stored at
-0xc(%ebp)is0x1bd3= 7123 in decimal — that’s the unlock code.
-
Use the code to get a SUID subshell
./leviathan6 7123 $ whoami leviathan7Why? Success — you’re now running with
leviathan7’s privileges.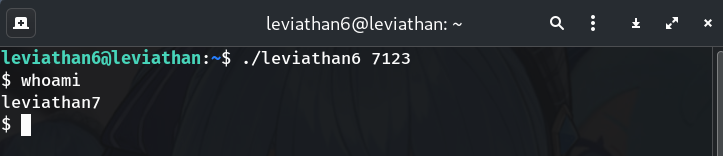
-
Read the next password
cat /etc/leviathan_pass/leviathan7Output:
qEs5Io5yM8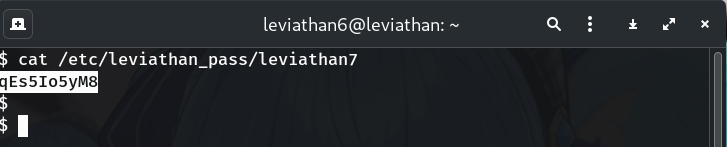
Password
qEs5Io5yM8
Troubleshooting
- Your addresses differ — That’s normal; use the addresses from your
disassemble mainoutput when setting the breakpoint. disassemble mainis paged — Pressc(continue without paging) orqthen re-rundisassemble main.- ASLR confusion — The binary is SUID; you’re inspecting code addresses within the process. Always break at the exact address shown in your current session.
gdbnot found? — It should be present on OTW boxes. If not, trygdb -qorgdbserveralternatives, but typicallygdbworks.
Copy-paste quick run
ssh leviathan6@leviathan.labs.overthewire.org -p 2223
# password: UgaoFee4li
cd ~
./leviathan6 0000 # → Wrong
gdb --args ./leviathan6 0000
(gdb) disassemble main
# find the cmp %eax,-0xc(%ebp) (addresses vary)
(gdb) break *0x0804922a
(gdb) run
(gdb) info registers
(gdb) print $ebp-0xc
(gdb) x/wx 0xADDRESS # value like 0x00001bd3
(gdb) print/d 0x00001bd3
# → 7123
(gdb) quit
./leviathan6 7123
whoami # → leviathan7
cat /etc/leviathan_pass/leviathan7
# → qEs5Io5yM8
Congrats 🎉 You reversed a SUID binary with GDB, extracted the hidden compare value, and finished Leviathan. GG!
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


