OverTheWire Leviathan Level 4 → 5 tutorial!!
Login
Log in as leviathan4 using the password from Level 3 → 4.
ssh leviathan4@leviathan.labs.overthewire.org -p 2223
# password: WG1egElCvO
Why? Each Leviathan level is a different UNIX user. To solve 4 → 5, you must be
leviathan4.
Task
There’s something interesting in your home directory — find it and extract the password for leviathan5.
A little bit of Theory
- Sometimes binaries don’t hide a password — they output encoded data you must transform.
-
If you see a long string of
0/1, think binary → ASCII. Common quick decoders:perl -0777 -pe 's/\s+//g; $_ = pack("B*", $_)'xxd -r -b(expects groups of 8 bits)
Further reading:
Solution
-
Explore the directory
ls -la find . -maxdepth 2 -type f -o -type dWhy? Quick recon often reveals hidden folders. You should see
.trash/with an executablebininside.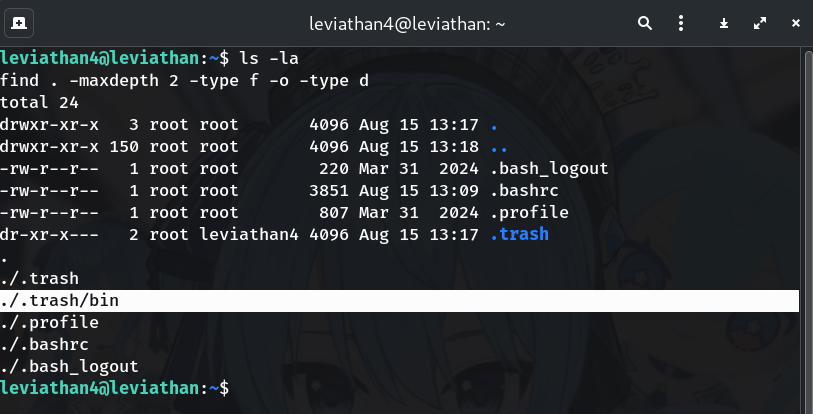
-
Identify and run the binary
file .trash/bin ./.trash/binWhy?
fileconfirms it’s an ELF; running it prints a long line of 0/1 bits.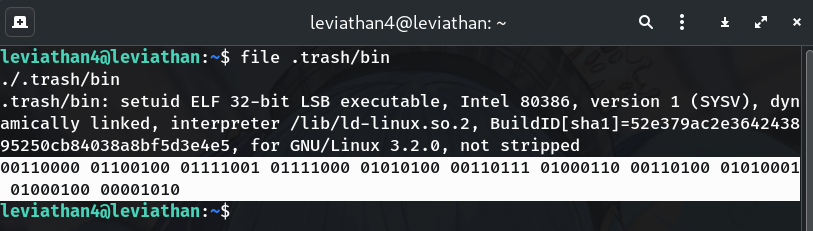
-
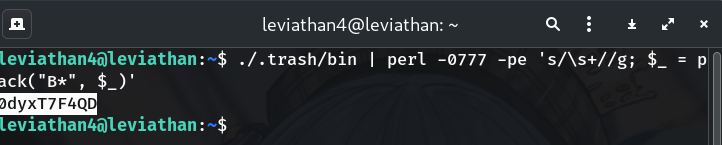
Decode binary → ASCII (Method A: Perl, recommended)
./.trash/bin | perl -0777 -pe 's/\s+//g; $_ = pack("B*", $_)'Why?
-0777slurps the entire stream,s/\s+//gstrips whitespace/newlines, andpack("B*", ...)converts the bitstring directly to bytes → clean ASCII. -
Alternative: Decode with
xxd(Method B)./.trash/bin | tr -cd '01' | sed 's/.\{8\}/& /g' | xxd -r -bWhy?
xxd -r -bneeds octets separated by spaces/newlines.trfilters to0/1,sedinserts a space every 8 bits. This avoids “cannot seek backwards” errors. -
Grab the password
The decoded output is plain text:
leviathan5: 0dyxT7F4QDWhy? The program emits the next username and password encoded as bits; once decoded, it’s readable ASCII.
Password
0dyxT7F4QD
Troubleshooting
- No output? Run
./.trash/binfrom the leviathan4 home directory. xxdcomplains? Make sure bits are grouped into 8s (sed 's/.\{8\}/& /g') or use the Perl one-liner.- Weird leading characters? Use the Perl command that strips whitespace before
pack.
Copy-paste quick run
ssh leviathan4@leviathan.labs.overthewire.org -p 2223
# password: WG1egElCvO
cd ~
file .trash/bin
# Method A (Perl — recommended)
./.trash/bin | perl -0777 -pe 's/\s+//g; $_=pack("B*", $_)'
# → leviathan5: 0dyxT7F4QD
# Method B (xxd)
./.trash/bin | tr -cd '01' | sed 's/.\{8\}/& /g' | xxd -r -b
# → leviathan5: 0dyxT7F4QD
ssh leviathan5@leviathan.labs.overthewire.org -p 2223
# password: 0dyxT7F4QD
Congrats 🎉 You recognized a binary-to-ASCII trick and extracted the next password. Onward to leviathan5!
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


