OverTheWire Leviathan Level 3 → 4 tutorial!!
Login
Log in as leviathan3 using the password from Level 2 → 3.
ssh leviathan3@leviathan.labs.overthewire.org -p 2223
# password: f0n8h2iWLP
Why? Each Leviathan level is a different UNIX user. To solve 3 → 4, you must be
leviathan3.
Task
There’s a SUID binary named level3 in the home directory. Find the password for leviathan4.
A little bit of Theory
- SUID binaries run with the owner’s privileges (here:
leviathan4). ltraceshows library calls and their arguments (e.g.,strcmp), which often leaks the expected password.- Many “password checkers” simply do
strcmp(user_input, "secret").
Further reading:
Solution
-
List files and spot SUID binary
ls -laWhy? We confirm
level3is owned byleviathan4and has the SUID bit.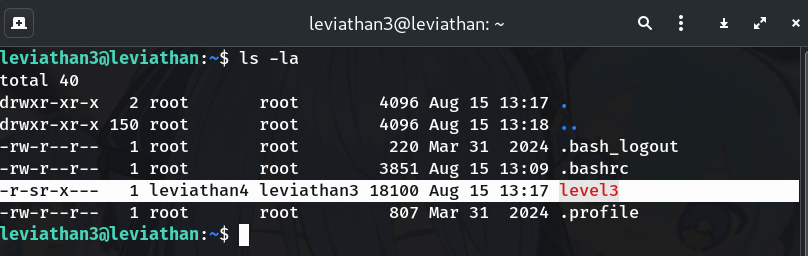
-
Run it once to see behavior
./level3 # Enter anything, e.g. Ahdiemoo1jWhy? Baseline: it prompts for a password and prints “WRONG”.
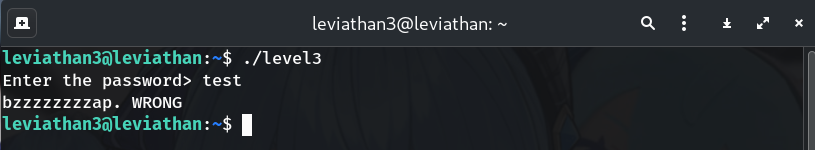
-
Trace with
ltraceto leak the real stringltrace ./level3 # when prompted, type: testWhy? The trace shows
strcmp("test\n", "snlprintf\n")→ expected password is snlprintf.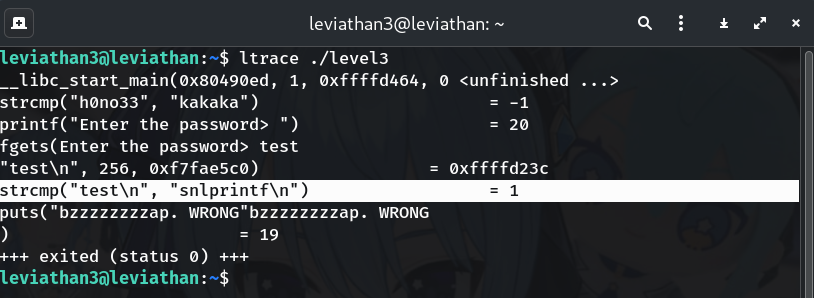
-
Use the discovered password to get a subshell
./level3 Enter the password> snlprintf $ whoami leviathan4Why? SUID program spawns a shell running as leviathan4.
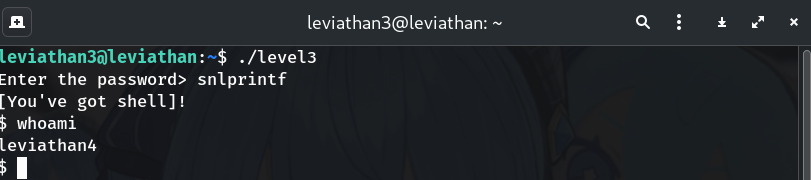
-
Read the real password from
/etc/leviathan_passcat /etc/leviathan_pass/leviathan4Why? All level credentials live here.
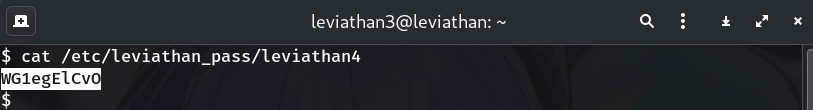
Password
WG1egElCvO
Troubleshooting
ltraceshows nostrcmp? Make sure you’re tracing./level3(not through a shell wrapper).- Typed
snlprintfbut still “WRONG”? Rememberfgetsincludes the newline automatically when you press Enter — you just typesnlprintfthen hit Enter. - No subshell prompt (
$) after success? Trywhoamianyway; some shells don’t change the prompt string.
Copy-paste quick run
ssh leviathan3@leviathan.labs.overthewire.org -p 2223
# password: f0n8h2iWLP
ls -la # see SUID ./level3
ltrace ./level3 # strcmp(..., "snlprintf\n")
./level3 # enter: snlprintf
whoami # → leviathan4
cat /etc/leviathan_pass/leviathan4
# → WG1egElCvO
Congrats 🎉 You used ltrace to catch a lazy strcmp password check and escalated via SUID. On to leviathan4!
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


