OverTheWire Leviathan Level 1 → 2 tutorial!!
Login
Log in as leviathan1 using the password from Level 0 → 1.
ssh leviathan1@leviathan.labs.overthewire.org -p 2223
# password: 3QJ3TgzHDq
Why? Each Leviathan level is a different UNIX user. To solve 1 → 2, you must be
leviathan1.
Task
OTW says there is a SUID binary in the home directory of leviathan1.
Your goal: use it to obtain the password for leviathan2.
A little bit of Theory
- SUID: when an executable has the setuid bit, it runs with the owner’s privileges (here,
leviathan2). strings: prints printable strings inside binaries—sometimes reveals clues.ltrace: traces library calls (likestrcmp) and shows the arguments the program uses—often enough to leak the expected password.
Further reading:
Solution
-
Explore the directory
ls -laWhy?
r-son the owner means SUID; executingcheckwill run as leviathan2.Look for a SUID binary:
-r-sr-x--- 1 leviathan2 leviathan1 15084 Aug 15 13:17 check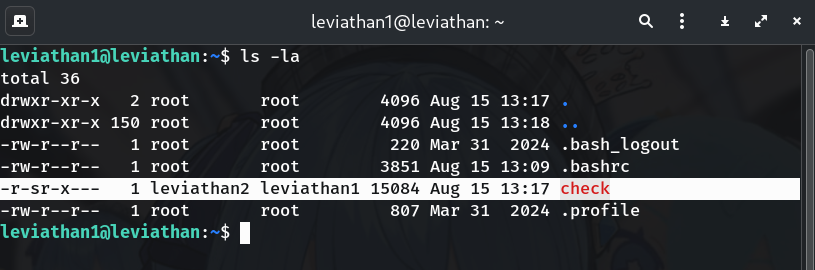
-
Run the binary once
./check password: test Wrong password, Good Bye ...Why? Confirms it asks for a password and exits on failure.
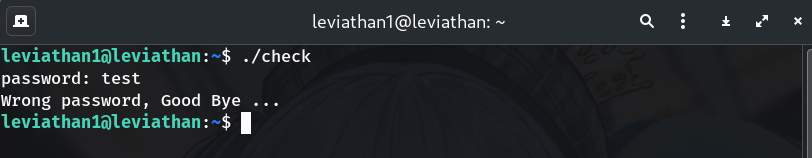
-
Try
stringsfor quick winsstrings checkWhy? Not all binaries keep secrets as plaintext—so we escalate to tracing.
You’ll see things like
password:,Wrong password, Good Bye ...,strcmp, etc., but no plaintext secret.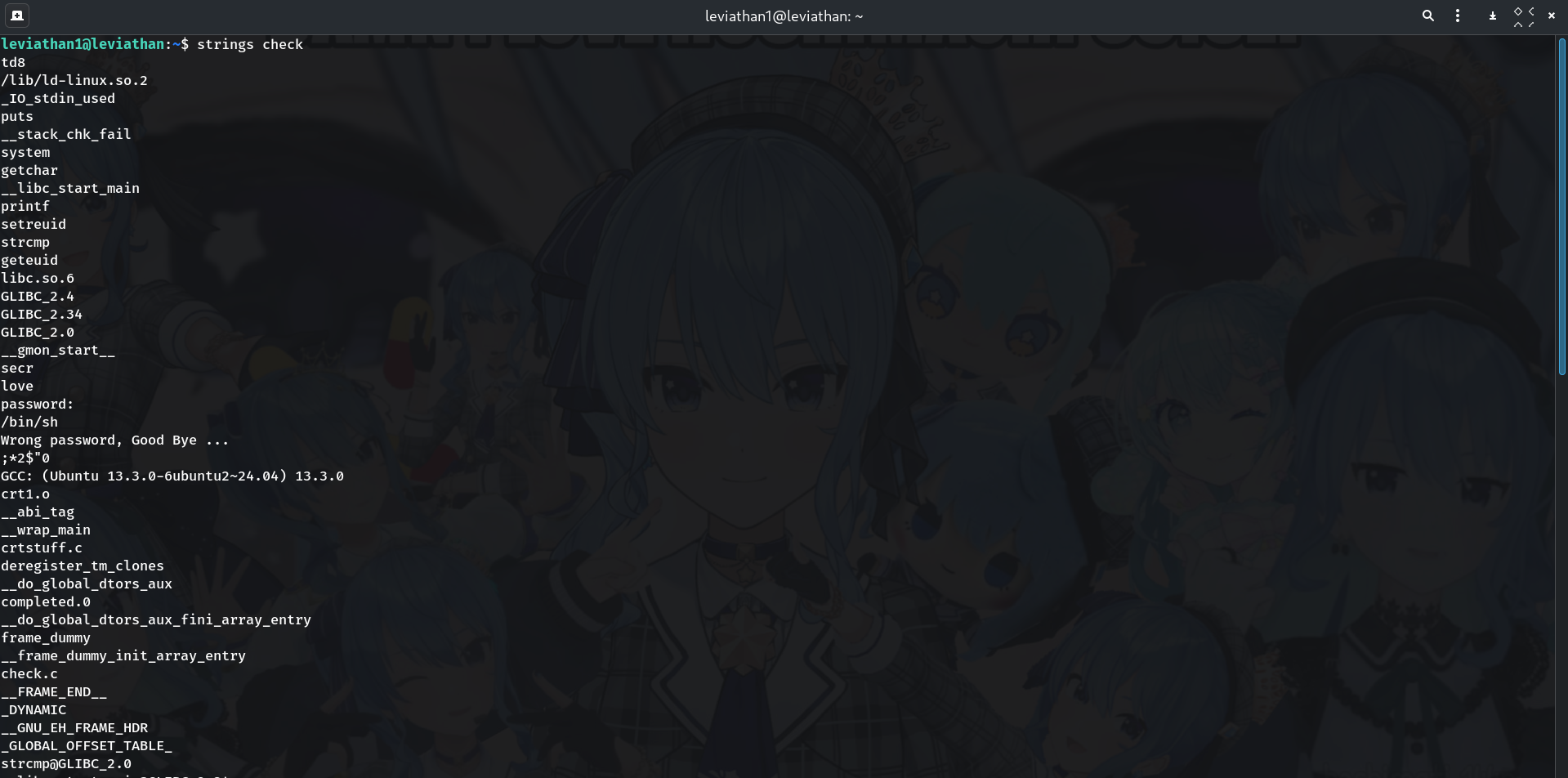
-
Trace with
ltraceto catchstrcmpltrace ./checkType any guess (e.g.,
1341232) and watch the trace:printf("password: ") = 10 getchar(... ) = '1' getchar(... ) = '3' getchar(... ) = '4' strcmp("134", "sex") = -1 puts("Wrong password, Good Bye ...") = 29 +++ exited (status 0) +++Why?
ltracereveals the exact argument passed tostrcmp, which is the expected password.→ The program compares our input to “sex”.
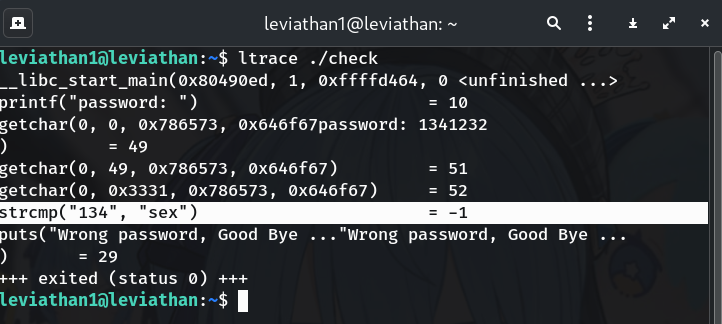
-
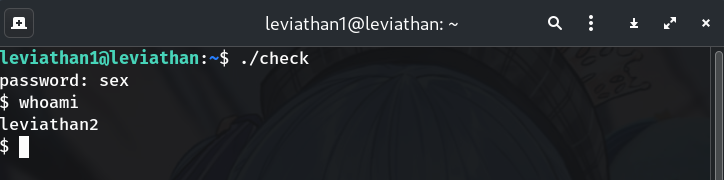
Use the discovered password
./check password: sex $ whoami leviathan2Why? The SUID binary spawned a subshell running as leviathan2.
-
Read the actual level password
All level passwords live in
/etc/leviathan_pass/.cat /etc/leviathan_pass/leviathan2Why? On Leviathan, the definitive credential is in this path; the SUID shell gives you permission to read it.
Output:
NsN1HwFoyN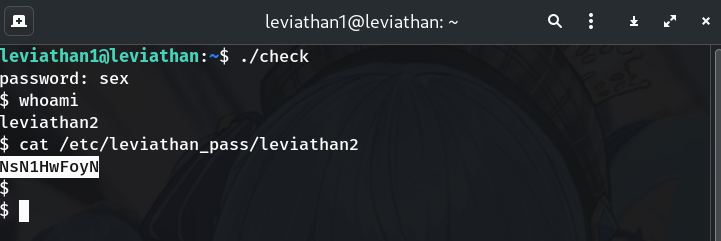
Password
NsN1HwFoyN
Troubleshooting
ltraceshows nothing? Make sure you’re tracing./checkdirectly, not via a shell wrapper.- Only gibberish from
strings? That’s normal;ltraceis the key here. - Didn’t get a subshell? You must type the exact string
sexwhen./checkprompts.
Copy-paste quick run
ssh leviathan1@leviathan.labs.overthewire.org -p 2223
# password: 3QJ3TgzHDq
ls -la # spot SUID ./check
ltrace ./check # reveals strcmp(..., "sex")
./check
password: sex # get subshell as leviathan2
whoami # → leviathan2
cat /etc/leviathan_pass/leviathan2
# → NsN1HwFoyN
Congrats 🎉 You used ltrace to leak a hard-coded comparison and escalated via a SUID binary. On to leviathan2!
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


