OverTheWire Leviathan Level 0 → 1 tutorial!!
Login
ssh leviathan0@leviathan.labs.overthewire.org -p 2223
# password: leviathan0
Each level is a separate UNIX account. The goal is always to find the password for the next level user.
Task
OTW description:
“Your first job is to find the password for leviathan1 somewhere on the system.”
So this is a recon challenge: explore files, look for backups, and dig into hidden directories.
A little bit of Theory
- Backups are often overlooked: if misconfigured, they may leak sensitive info.
-
Recon basics:
ls -la→ list files, including hidden ones.head file→ peek at large files without scrolling.grep pattern file→ search for useful keywords in big files.
Further reading:
Solution
-
List your home directory
ls -laWhy? The
.backupfolder is owned byleviathan1but group-readable byleviathan0. That’s our entry point.Output (excerpt):
drwxr-x--- 2 leviathan1 leviathan0 4096 Aug 15 13:17 .backup ...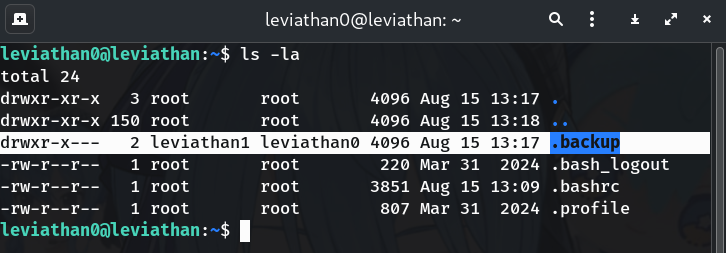
→ Found a hidden folder:
.backup.
-
Inspect
.backupcd .backup ls -laWhy? We find a big
bookmarks.html. Manually reading ~130k lines isn’t smart.Output:
-rw-r----- 1 leviathan1 leviathan0 133259 Aug 15 13:17 bookmarks.html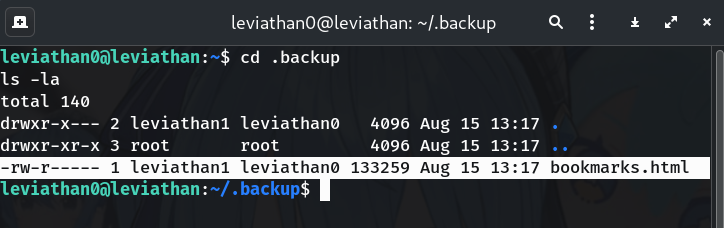
-
Peek inside
Shows Netscape bookmark format. So this is just a long list of saved URLs.
head bookmarks.htmlWhy? Understanding file type helps decide search strategy.
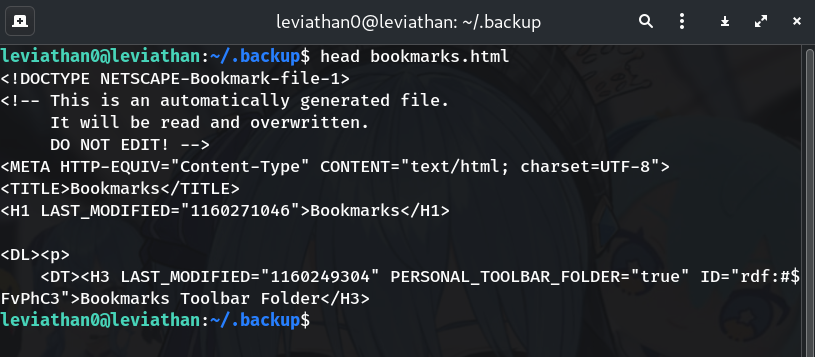
-
Search for “leviathan”
grep leviathan bookmarks.htmlWhy? Searching for “leviathan” in bookmarks is logical — the file likely references the wargame and may leak a password.
Output:
<DT><A HREF="http://leviathan.labs.overthewire.org/passwordus.html | This will be fixed later, the password for leviathan1 is 3QJ3TgzHDq" ...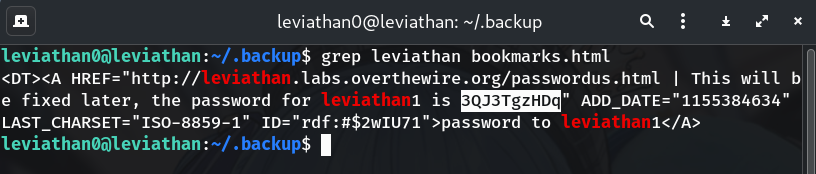
Boom 💥 Found the line with the password for leviathan1!
Password
3QJ3TgzHDq
Troubleshooting
- Didn’t find
.backup? → Ensure you ranls -la(plainlswon’t show hidden dirs). - File too big to read manually? → Use
head,tail,grep. grepreturns nothing? → Try broader keywords likepass,password, orleviathan.
Copy-paste quick run
ssh leviathan0@leviathan.labs.overthewire.org -p 2223
# password: leviathan0
ls -la
cd .backup
grep leviathan bookmarks.html
# → password: 3QJ3TgzHDq
ssh leviathan1@leviathan.labs.overthewire.org -p 2223
# password: 3QJ3TgzHDq
🎉 Congrats — you completed Leviathan Level 0 → 1. Lesson: hidden backups = easy loot if permissions are misconfigured.
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


