OverTheWire Krypton Level 4 → 5 tutorial!!
Login
Log in as krypton4 using the password from Level 3 → 4.
ssh krypton4@krypton.labs.overthewire.org -p 2231
# password: BRUTE
Why? Each level is a separate UNIX user. To solve 4 → 5, you must be
krypton4.
Task
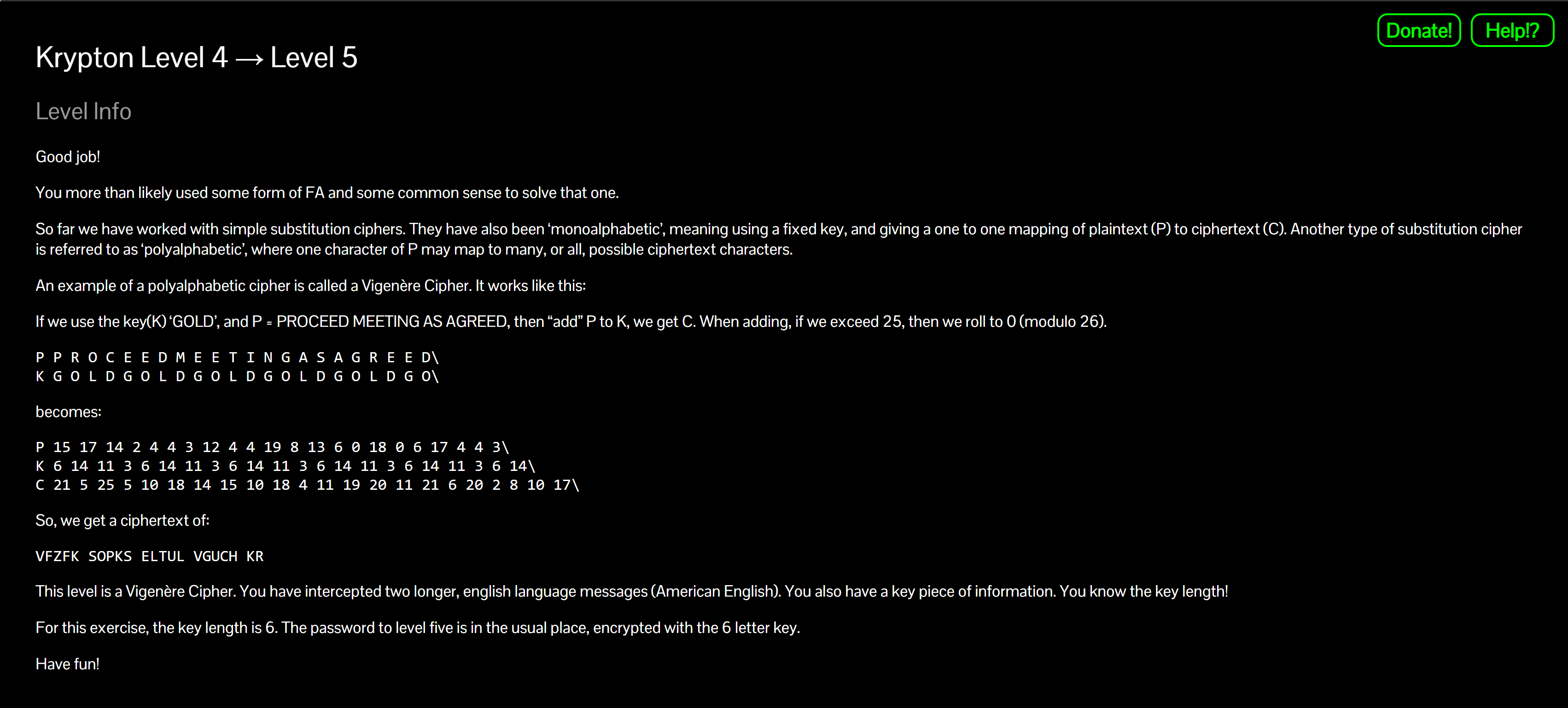
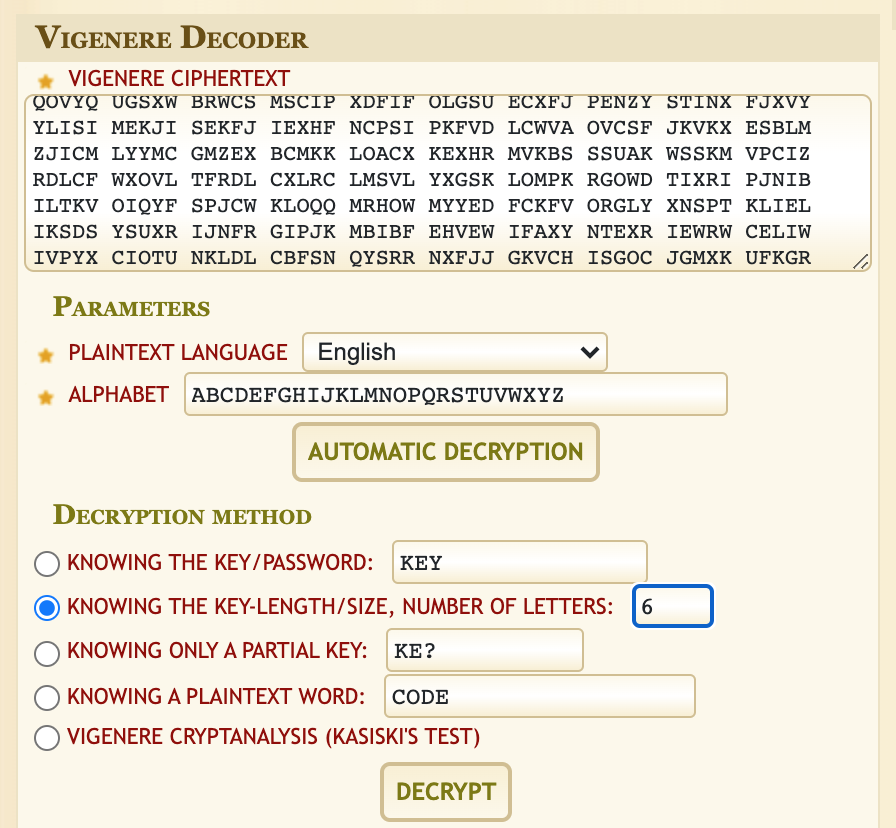
This level uses a Vigenère cipher. You have two longer English ciphertexts and you know the key length is 6.
The password for level 5 is stored in krypton5, encrypted with the same 6-letter key.
A little bit of Theory
- Vigenère = repeating-key Caesar: each position is shifted by the corresponding letter of the key.
- Knowing the key length lets you segment the text into 6 columns; each column behaves like a Caesar shift and can be cracked with frequency analysis (Kasiski / Friedman ideas).
- Once the key is known, decryption is straightforward.
Further reading:
Solution
-
Inspect the level directory
cd /krypton/krypton4 ls -laYou’ll see:
-rw-r----- 1 krypton4 krypton4 1740 found1 -rw-r----- 1 krypton4 krypton4 2943 found2 -rw-r----- 1 krypton4 krypton4 287 HINT -rw-r----- 1 krypton4 krypton4 10 krypton5 -rw-r----- 1 krypton4 krypton4 1385 README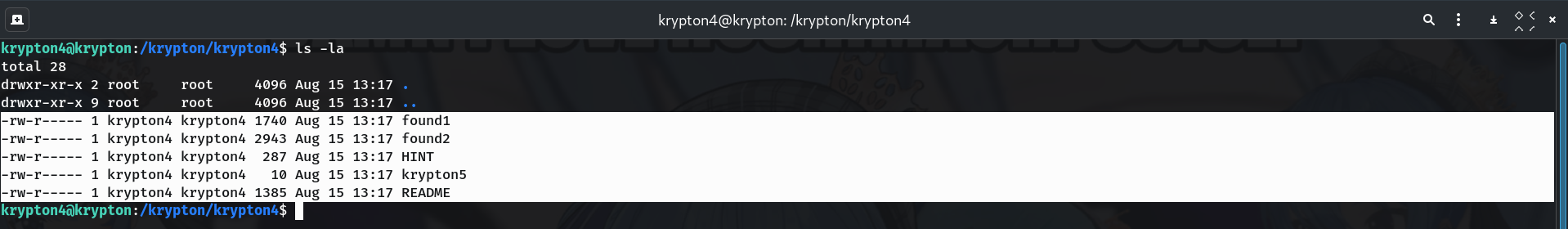
-
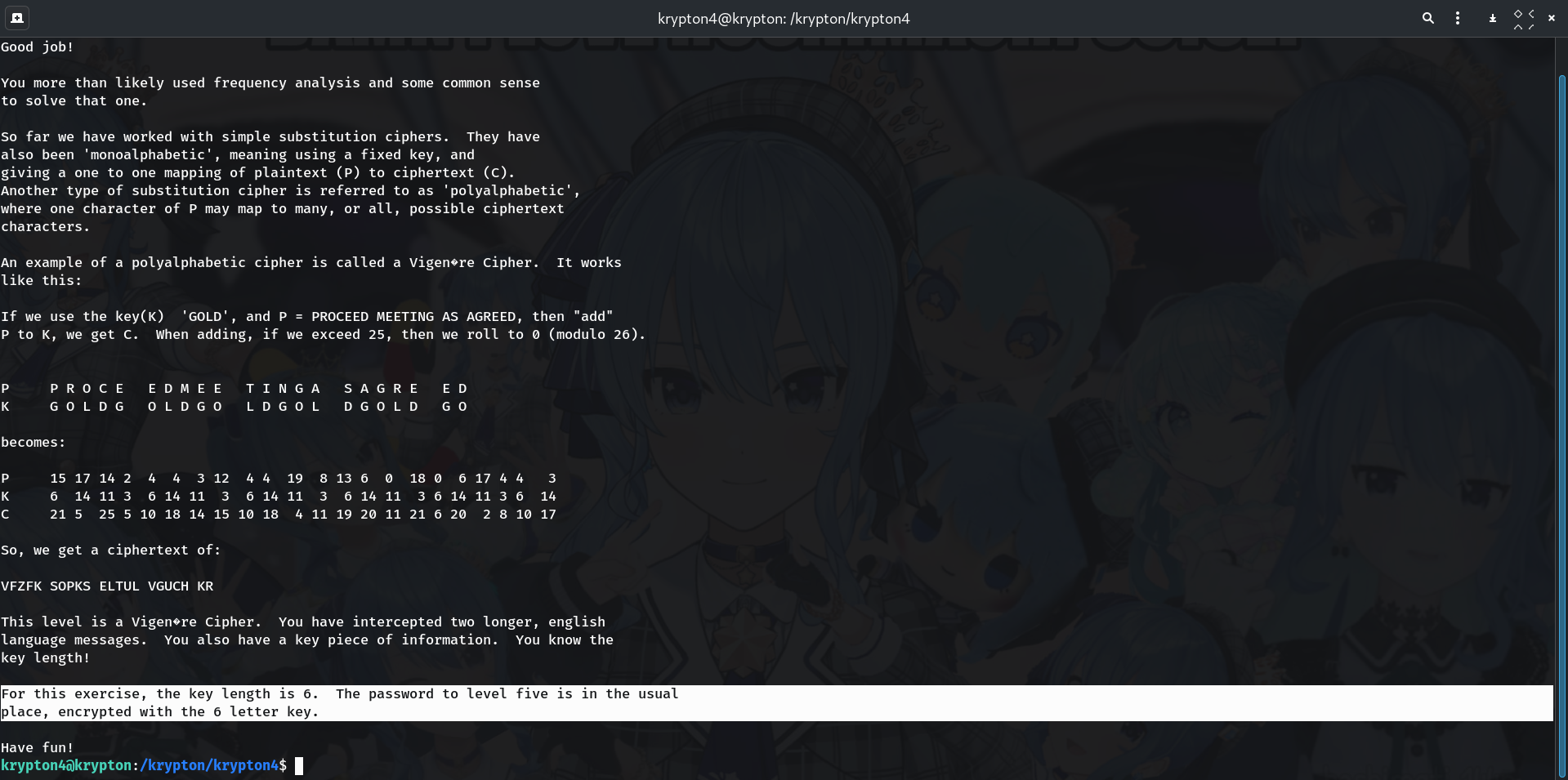
Read the README
cat READMEOutput (truncated):
This level is a Vigenère Cipher. You have intercepted two longer, english language messages. You also have a key piece of information. You know the key length! For this exercise, the key length is 6. The password to level five is in the usual place...Why? The README explicitly states the key length = 6. That’s the crucial clue.
-
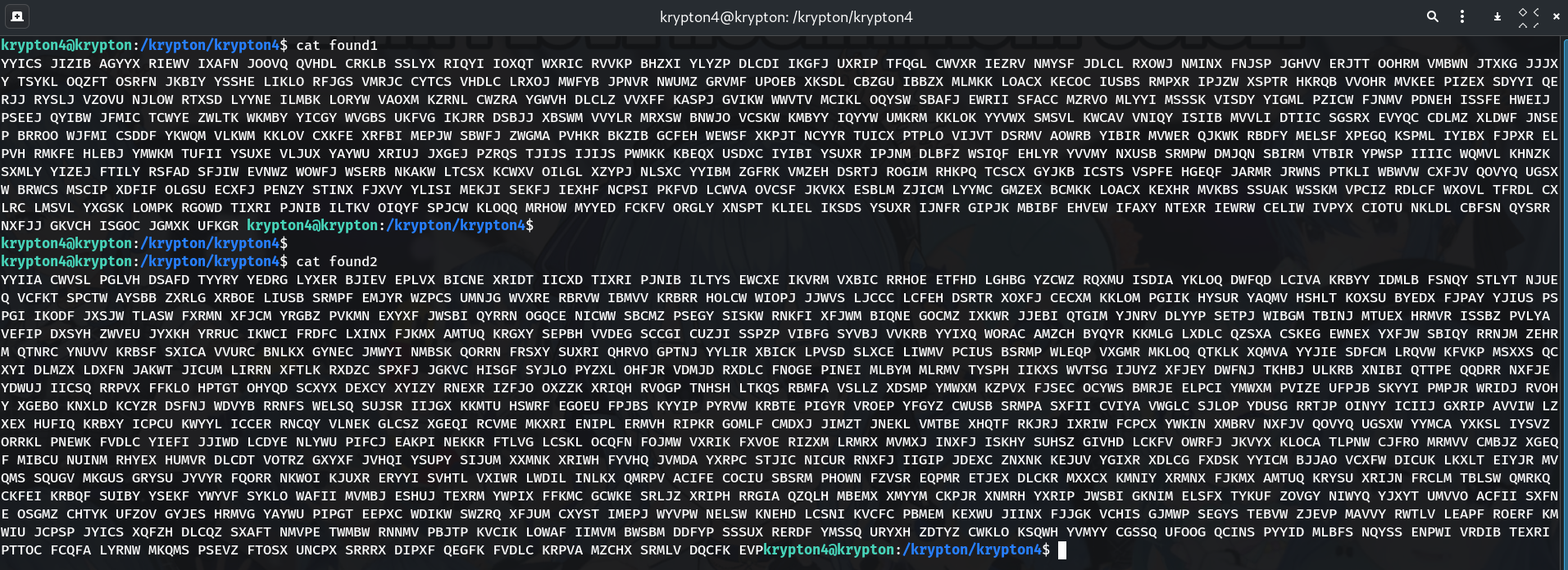
Preview one of the ciphertexts
cat found1 | headYYTCS JZIB AGY...These are long ciphertexts used to deduce the key.
-
Recover the key (length = 6) from a long ciphertext
Use an online Vigenère breaker (for convenience):
- Open dCode – Vigenère cipher.
- Paste the content of
found1(orfound2) into VIGENERE CIPHERTEXT. - Choose “KNOWING THE KEY-LENGTH/SIZE” and set it to 6.
- Click Decrypt and note the proposed key.
Example result:
Key: FREKEYWhy? Longer texts give robust frequency statistics per column → the solver can infer the 6 Caesar shifts (i.e., the key).
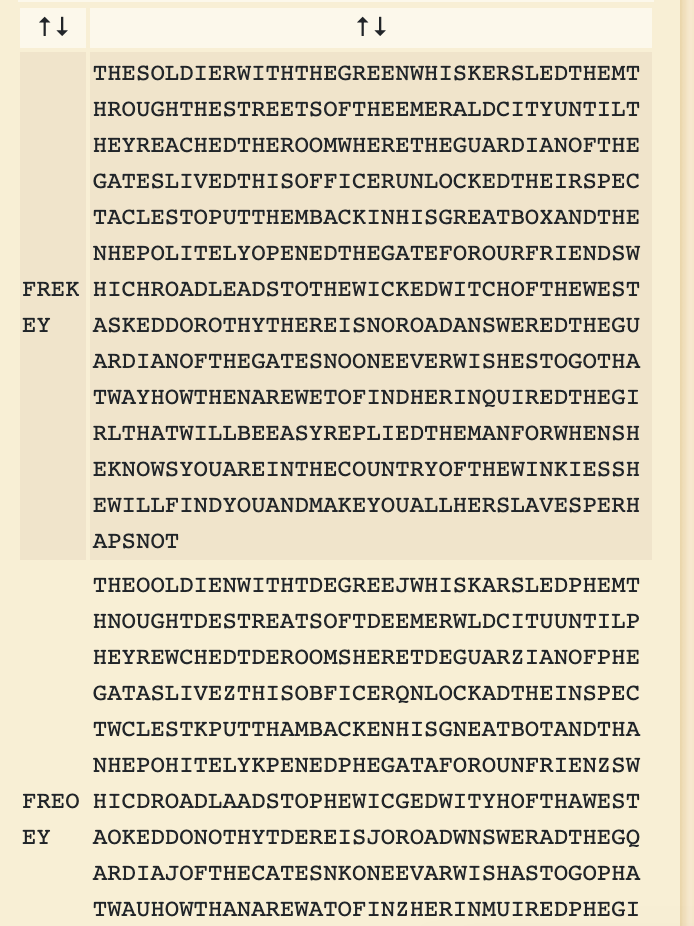
-
Decrypt
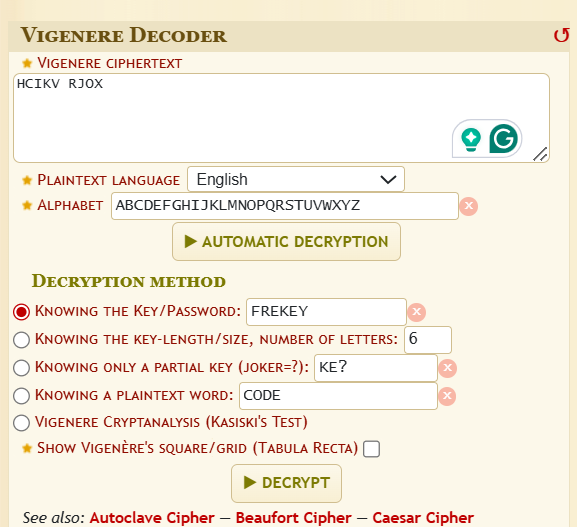
krypton5with the recovered keycat krypton5 # HCIKV RJ0X- Still on dCode, paste the content of
krypton5. - Choose “KNOWING THE KEY/PASSWORD” and enter the recovered key:
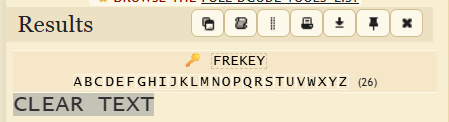
FREKEY. - Decrypt → Result:
CLEARTEXTWhy?
krypton5is encrypted with the same key. Once the key is known, the short ciphertext decrypts immediately.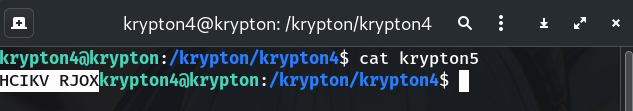
- Still on dCode, paste the content of
-
Log into the next level
ssh krypton5@krypton.labs.overthewire.org -p 2231 # password: CLEARTEXT
Password
CLEARTEXT
Troubleshooting
- Key looks wrong / gibberish output → Try the other long ciphertext (
found2) or ensure you set key length = 6 when cracking. - Multiple keys suggested → Prefer the one that makes clean English for both
found1andfound2. - Manual route (no web) → Segment the ciphertext into 6 columns and run frequency analysis per column to derive 6 Caesar shifts, then assemble the key.
Copy-paste quick run
ssh krypton4@krypton.labs.overthewire.org -p 2231
# password: BRUTE
cd /krypton/krypton4
cat README
cat found1 | head
# → copy text into dCode, set key length = 6 → get FREKEY
# Decrypt krypton5 with FREKEY → CLEARTEXT
ssh krypton5@krypton.labs.overthewire.org -p 2231
# password: CLEARTEXT
Congrats 🎉 You used the known key length to break a Vigenère cipher and recover the next password — welcome to krypton5!
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


