OverTheWire Krypton Level 3 → 4 tutorial!!
Login
Log in as krypton3 using the password from Level 2 → 3.
ssh krypton3@krypton.labs.overthewire.org -p 2231
# password: CAESARISEASY
Why? Each Krypton level is a separate UNIX user. To solve 3 → 4, you must be
krypton3.
Task
The password for level 4 is stored in the file krypton4.
You also have three ciphertext files (found1, found2, found3) encrypted with the same substitution key.
This allows you to perform frequency analysis.
A little bit of Theory
- Substitution cipher replaces each plaintext letter with another letter consistently.
- When the same key is reused across large texts, patterns emerge.
- In English, the most frequent letter is usually E, followed by T, A, O, I, N…
- By comparing ciphertext frequency with expected English frequency, you can build a mapping.
Further reading:
Solution
-
Explore the directory
cd /krypton/krypton3 ls -laWhy? Confirm the presence of
found1,found2,found3,krypton4, and hints.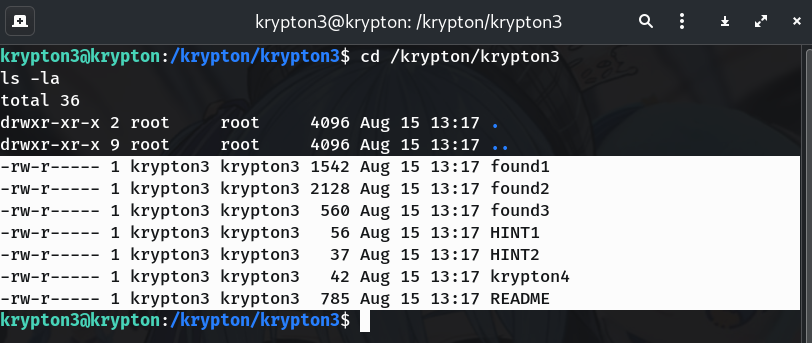
-
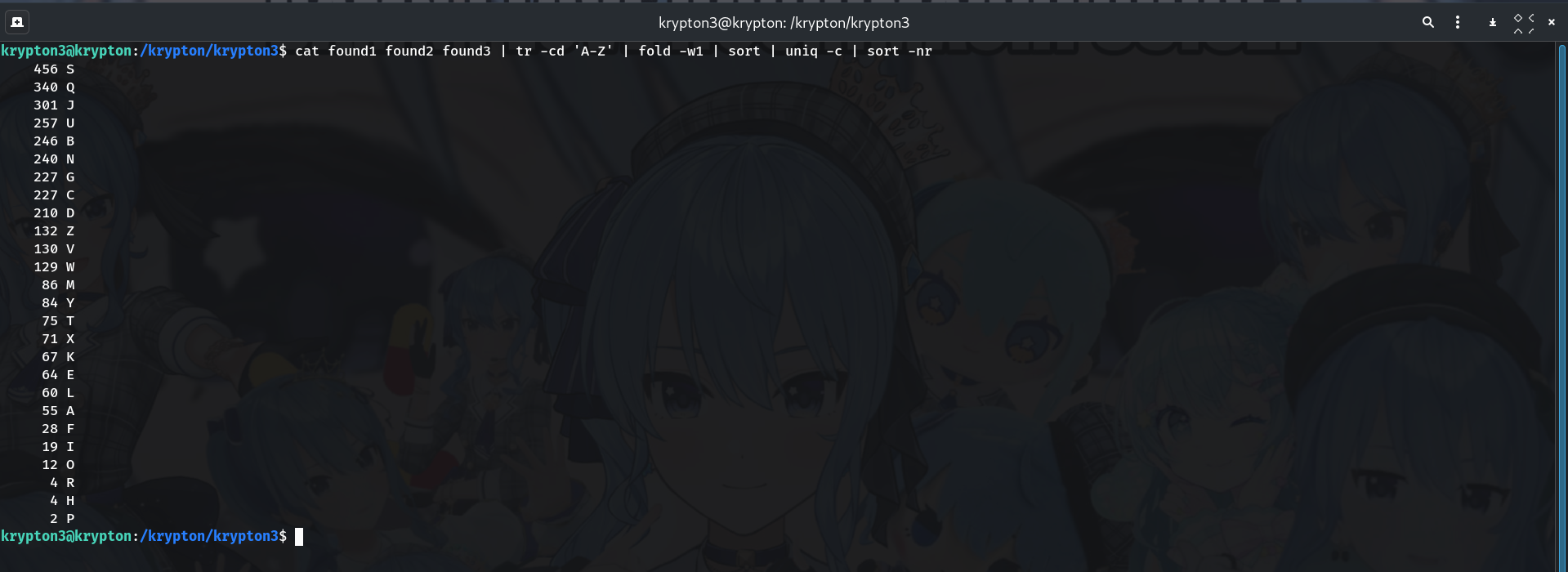
Count character frequencies
Method A (simple + stable):
cat found1 found2 found3 | tr -cd 'A-Z' | fold -w1 | sort | uniq -c | sort -nrMethod B (loop style):
for i in {A..Z}; do cnt=$(cat found1 found2 found3 | tr -cd "$i" | wc -c) printf "%5d %s\n" "$cnt" "$i" done | sort -nrWhy? This reveals the distribution of letters. The most frequent ciphertext letter is a candidate for mapping to E.
-
Build a substitution mapping
Example output:
456 S 340 Q 301 J 257 U ...→ Guess
S ≈ E,Q ≈ T,J ≈ A, … and adjust based on context. Use English frequency order: ETAOINSRHDLU… -
Test mapping against
krypton4cat krypton4 | tr 'SQJUBNGCDZVWMYTXKELAFIORHP' 'EATSORNIHCLDUPYFWGMBKVXQJZ'Output:
WELL DONE THE LEVEL FOUR PASSWORD IS BRUTE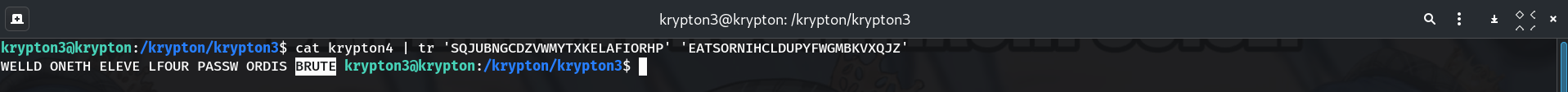
-
Log into the next level
ssh krypton4@krypton.labs.overthewire.org -p 2231 # password: BRUTE
Password
BRUTE
Troubleshooting
- If the output is garbled → tweak the frequency mapping order.
- Make sure to include all 26 letters in the
trmapping. /tmpcleanup issues do not apply here — all files are in/krypton/krypton3.
Copy-paste quick run
ssh krypton3@krypton.labs.overthewire.org -p 2231
# password: CAESARISEASY
cd /krypton/krypton3
cat found1 found2 found3 | tr -cd 'A-Z' | fold -w1 | sort | uniq -c | sort -nr
# build mapping from frequency
cat krypton4 | tr 'SQJUBNGCDZVWMYTXKELAFIORHP' 'EATSORNIHCLDUPYFWGMBKVXQJZ'
# → WELL DONE THE LEVEL FOUR PASSWORD IS BRUTE
ssh krypton4@krypton.labs.overthewire.org -p 2231
# password: BRUTE
Congrats 🎉 You broke a monoalphabetic substitution with frequency analysis — welcome to krypton4!
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


