OverTheWire Krypton Level 2 → 3 tutorial!!
Login
Log in as krypton2 using the password from Level 1 → 2.
ssh krypton2@krypton.labs.overthewire.org -p 2231
# password: ROTTEN
Why? Each level is a different UNIX user. To solve 2 → 3, you must be
krypton2.
Task
This level uses a classic Caesar cipher. The setuid helper encrypt (owned by krypton3) looks for a keyfile in your current working directory. Create a workspace in /tmp, link the keyfile there, and make sure krypton3 can access your directory.
A little bit of Theory
- A Caesar (shift) cipher rotates letters by a fixed key
k(A→B whenk=1, etc.). - If you discover one plaintext–ciphertext pair, you can compute
k. - To decrypt when the encryption key is
k, use26 - k(mod 26).
Further reading:
Solution
-
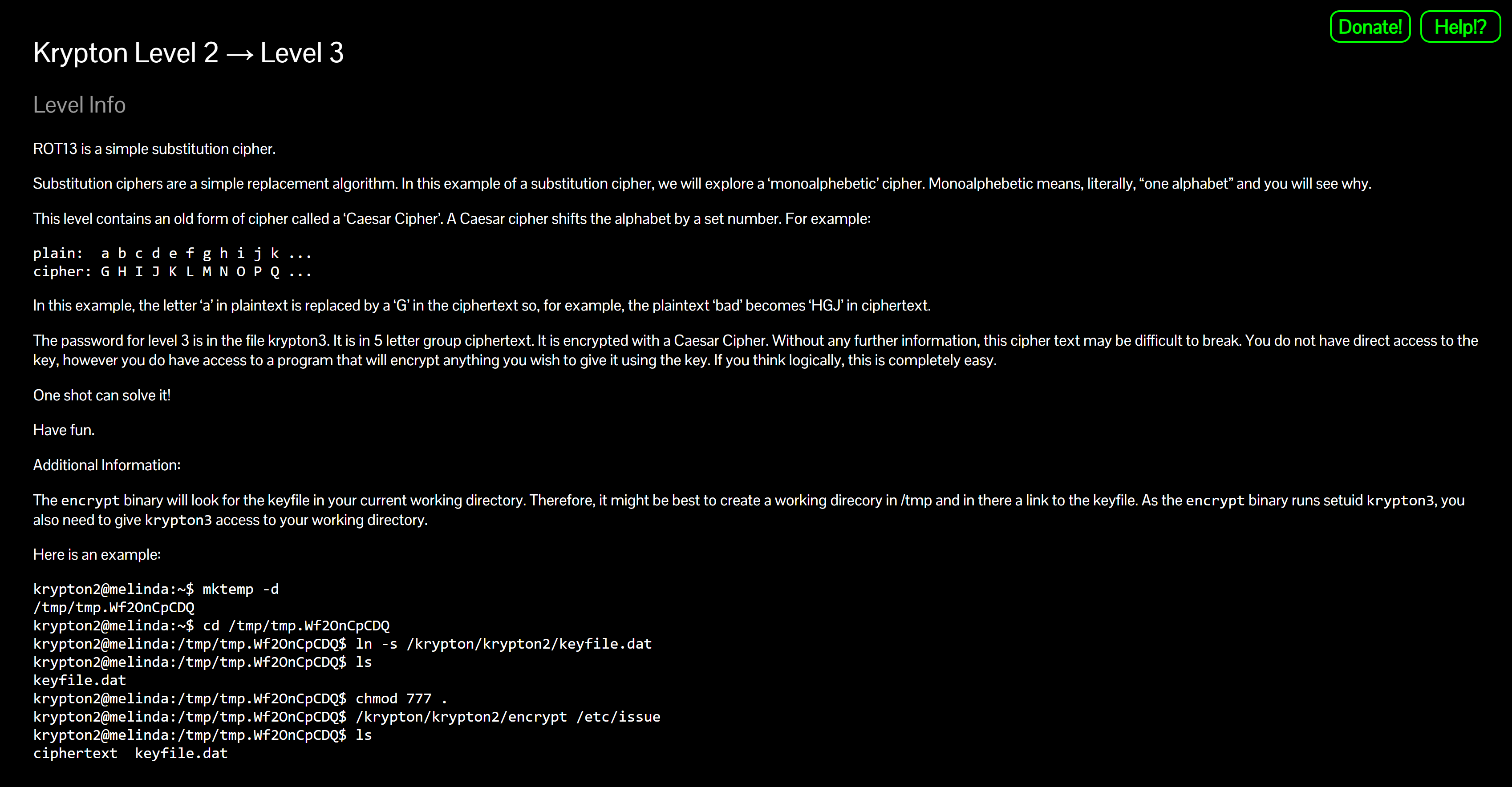
Explore the level directory
cd /krypton/krypton2 ls -laWhy? Verify the presence of the setuid
encryptbinary, the keyfile, and the sample ciphertext file.You should see something like:
-rwsr-x--- 1 krypton3 krypton2 9032 encrypt -rw-r----- 1 krypton3 krypton3 27 keyfile.dat -rw-r----- 1 krypton2 krypton2 13 krypton3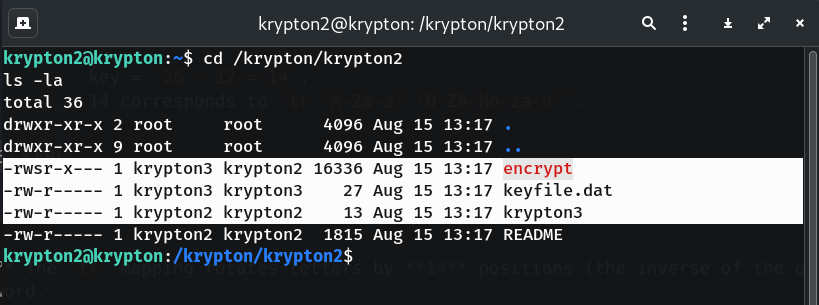
-
Prepare a writable, world-accessible working directory under
/tmpTMPDIR=$(mktemp -d) cd "$TMPDIR" ln -s /krypton/krypton2/keyfile.dat chmod 777 .Why?
encryptruns as krypton3 and must be able to cd into your working dir and read the keyfile via the symlink. -
Derive the shift key using a known plaintext
echo "AAAAA" > encrypt.txt /krypton/krypton2/encrypt encrypt.txt ls -la cat ciphertext # → MMMMMWhy? Encrypting
'AAAAA'lets you measure the shift directly: A → M means the encryption key is 12 (A=1 → M=13 ⇒ +12).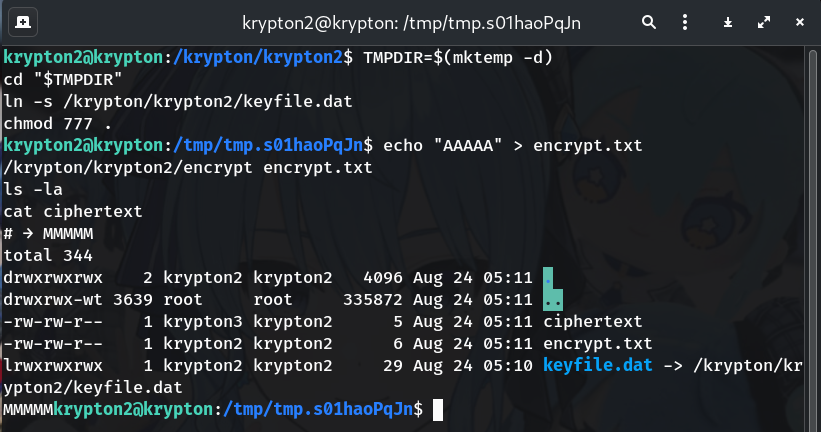
-
Compute the decryption key and decode the target file
- Decryption key =
26 - 12 = 14. - A shift of 14 corresponds to
tr 'A-Za-z' 'O-ZA-No-za-n'.
cd /krypton/krypton2 cat krypton3 | tr 'A-Za-z' 'O-ZA-No-za-n'Why? The
trmapping rotates letters by 14 positions (the inverse of the encryption key), yielding the plaintext password.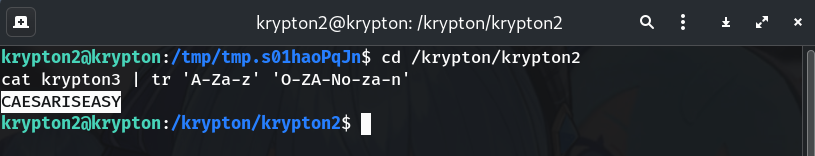
- Decryption key =
-
Log into the next level
ssh krypton3@krypton.labs.overthewire.org -p 2231 # password: CAESARISEASY
Password
CAESARISEASY
Troubleshooting
Permission denied/No such file→ Ensure you ranchmod 777 .in/tmp/...and created the symlinkkeyfile.datin the same working directory where you runencrypt.- Empty / wrong
ciphertext→ Re-runencryptfrom the directory containing bothencrypt.txtand the symlinkedkeyfile.dat. - Wrong plaintext → Double‑check the
trmapping uses O-ZA-N (shift 14), not ROT13. - Directory cleaned →
/tmpmay be wiped; just re‑create withmktemp -d.
Copy-paste quick run
ssh krypton2@krypton.labs.overthewire.org -p 2231
# password: ROTTEN
cd /krypton/krypton2
TMPDIR=$(mktemp -d); cd "$TMPDIR"
ln -s /krypton/krypton2/keyfile.dat
chmod 777 .
echo AAAAA > encrypt.txt
/krypton/krypton2/encrypt encrypt.txt
cat ciphertext # expect MMMMM → encryption key = 12
cd /krypton/krypton2
cat krypton3 | tr 'A-Za-z' 'O-ZA-No-za-n' # decrypt with shift 14
# copy the output (password)
ssh krypton3@krypton.labs.overthewire.org -p 2231
# paste password
Congrats 🎉 You reversed a setuid Caesar workflow and recovered the password — welcome to krypton3!
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


