OverTheWire Bandit Level 5 → 6 tutorial!!
Login
Log in as bandit5 using the password you just obtained from Level 4 → 5.
ssh bandit5@bandit.labs.overthewire.org -p 2220
# password: 4oQYVPkxZOOEOO5pTW81FB8j8lxXGUQw
Why? Each Bandit level is a separate UNIX user. To solve 5 → 6, you must be the
bandit5user.
Task
The password for the next level is stored somewhere under the directory inhere and the file has all of these properties:
- human-readable
- 1033 bytes in size
- not executable
A little bit of Theory
-
Use
findto search recursively by properties:- Regular file:
-type f - Size in bytes:
-size 1033c(thecmeans bytes) - Readable:
-readable - Not executable:
! -executable
- Regular file:
-
Chain the tests and print the match:
find inhere -type f -size 1033c -readable ! -executable -print - Sometimes
filemay say “ASCII text, with very long lines (1000)” — that’s still human-readable. - Once you have the path,
cat <path>to reveal the password.
Further reading:
Solution
-
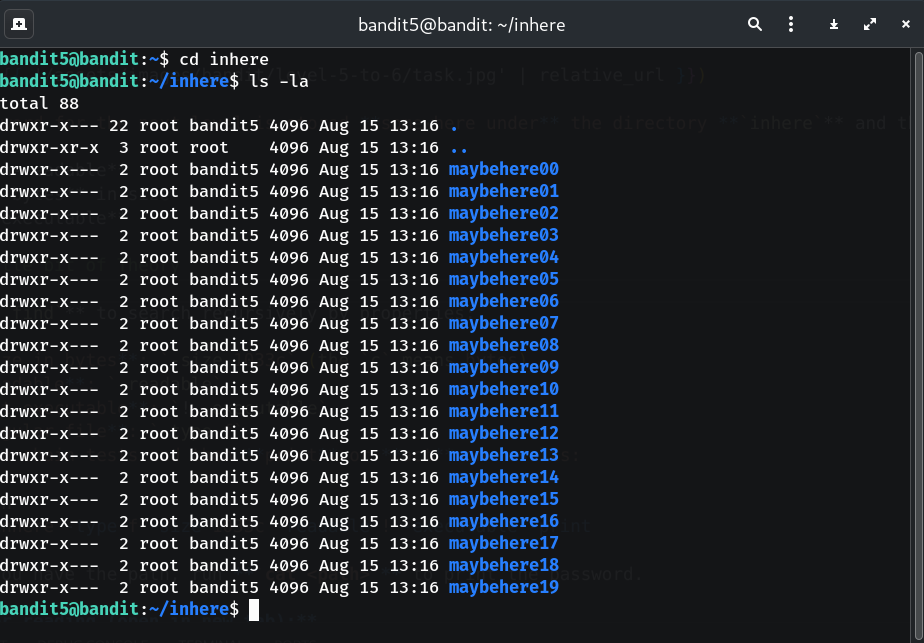
Inspect the
inheretreecd inhere && ls -laWhy? Quick overview of the directory layout before searching.
-
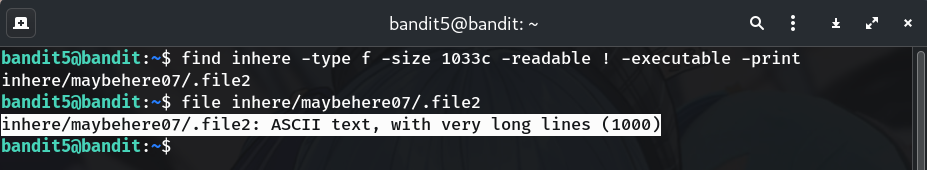
Search for the file matching all constraints
find .. -path '*/inhere/*' -type f -size 1033c -readable ! -executable -print # or, when already inside inhere: find . -type f -size 1033c -readable ! -executable -printWhy? Returns the single file that meets all three conditions.
Example result (from my run):
inhere/maybehere07/.file2 -
(Optional) Verify the type
file inhere/maybehere07/.file2Why? Confirms it’s human-readable (e.g.,
ASCII text, with very long lines (1000)).
-
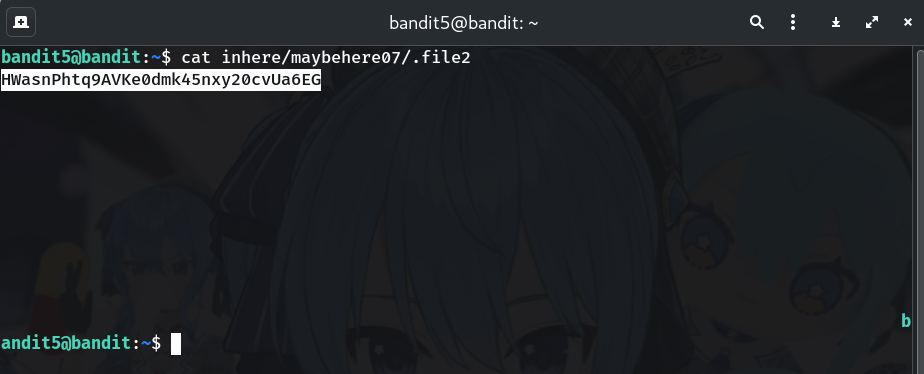
Print the password
cat inhere/maybehere07/.file2Why? Outputs the content — the password for the next level.
-
Copy the password (no extra spaces/newlines).
-
Log into the next level (bandit6)
exit ssh bandit6@bandit.labs.overthewire.org -p 2220 # paste the password you just found when prompted
Password
This is the password shown in my run; if yours differs, copy the one from your own terminal output.
HWasnPhtq9AVKe0dmk45nxy20cvUa6EG
Troubleshooting
- No results from
find? → Ensure thecafter1033(bytes), and include! -executable. - Unsure which one is text? →
file <path>should sayASCII text(possibly with extra notes about long lines). - Permission issues → Make sure you’re the right user (
bandit5) and searching underinhere.
Congrats 🎉 You found the uniquely matching file and can now play as bandit6.
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


