OverTheWire Bandit Level 32 → 33 tutorial!!
Login
Log in as bandit32 using the password you obtained from Level 31 → 32.
ssh bandit32@bandit.labs.overthewire.org -p 2220
# password: 3O9RfhqyAlVBEZpVb6LYStshZoqoSx5K
Why? Each Bandit level is a separate UNIX user. To solve 32 → 33, you must be the
bandit32user.
Task

When you log in, you’re dropped into an UPPERCASE SHELL that uppercases whatever you type (so ls becomes LS, which doesn’t exist).
Goal: break out to a real shell and read the password for bandit33.
A little bit of Theory
- The custom “uppershell” takes your input and converts letters → UPPERCASE before executing it.
- In POSIX shells,
$0expands to the current shell’s path/name (e.g.,/bin/sh). Because$and digits aren’t letters, they aren’t uppercased, so$0expands correctly and launches a normal shell. - Once in a normal shell, you can read
/etc/bandit_pass/bandit33.
Further reading:
Solution
-
Spawn a real shell using a variable expansion
$0Why?
$0expands to the current shell’s executable (e.g.,/bin/sh) after the uppercase filter, giving you a normal shell prompt. -
Verify who you are (optional)
whoami # bandit32Why? Sanity-check that you’re still the right user, now in a proper shell.
-
Read the next password
cat /etc/bandit_pass/bandit33Why? Each password lives in
/etc/bandit_pass/<user>and is readable by the matching previous level.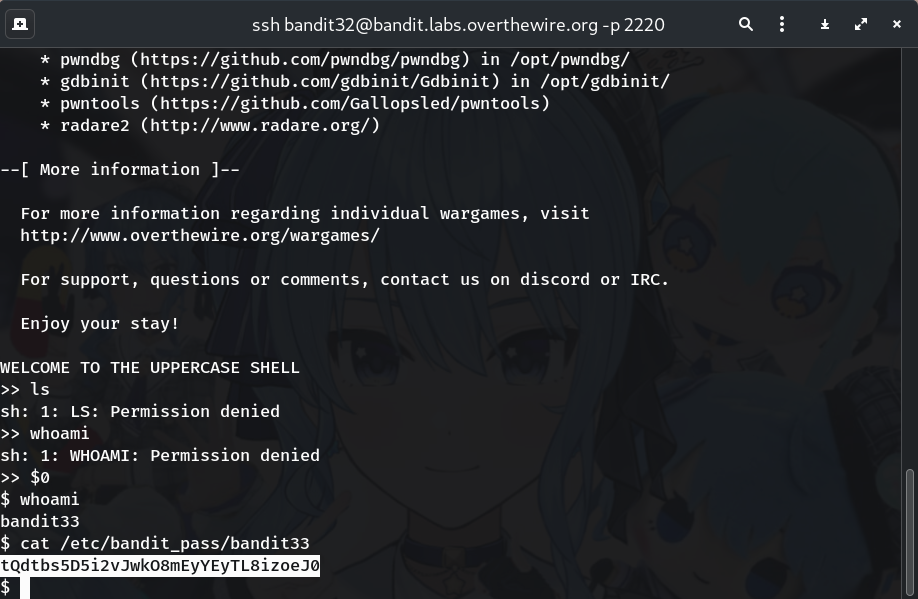
Password
Paste here the exact line your terminal printed:
tQdtbs5D5i2vJwkO8mEyYEyTL8izoeJ0
Troubleshooting
$0: command not found→ Tryecho "$0"to see what it expands to. If empty, try$SHELL(if set):"$SHELL". You can also try${0}.- Still uppercased? → Make sure you typed
$0exactly (dollar-zero, no spaces). - Permission issues → You must be logged in as bandit32 to read
bandit33’s password.
Congrats 🎉 You bypassed the uppercasing shell using variable expansion and grabbed the next credentials. On to bandit33!
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


