OverTheWire Bandit Level 28 → 29 tutorial!!
Login
Log in as bandit28 using the password you obtained from Level 27 → 28.
ssh bandit28@bandit.labs.overthewire.org -p 2220
# password: Yz9IpL0sBcCeuG7m9uQFt8ZNpS4HZRcN
Why? Each Bandit level is a separate UNIX user. To solve 28 → 29, you must be the
bandit28user.
Task
There is a git repository at:
ssh://bandit28-git@localhost:2220/home/bandit28-git/repo
The password for bandit28-git is the same as for bandit28. Clone the repo and find the password for bandit29.
A little bit of Theory
- Git keeps full history; removing a secret in a later commit doesn’t erase it from older commits.
git logshows commit history;git show <commit>displays the changes/content for that commit.- Look for a commit message like “fix info leak”—that’s a classic hint the password was present before.
Further reading:
Solution
-
Clone the repository to a writable temp folder
WORKDIR=$(mktemp -d) cd "$WORKDIR" git clone ssh://bandit28-git@localhost:2220/home/bandit28-git/repo "repo-$RANDOM" cd repo-*Why?
/tmpis writable for us, and the remote userbandit28-gitauthenticates with your bandit28 password.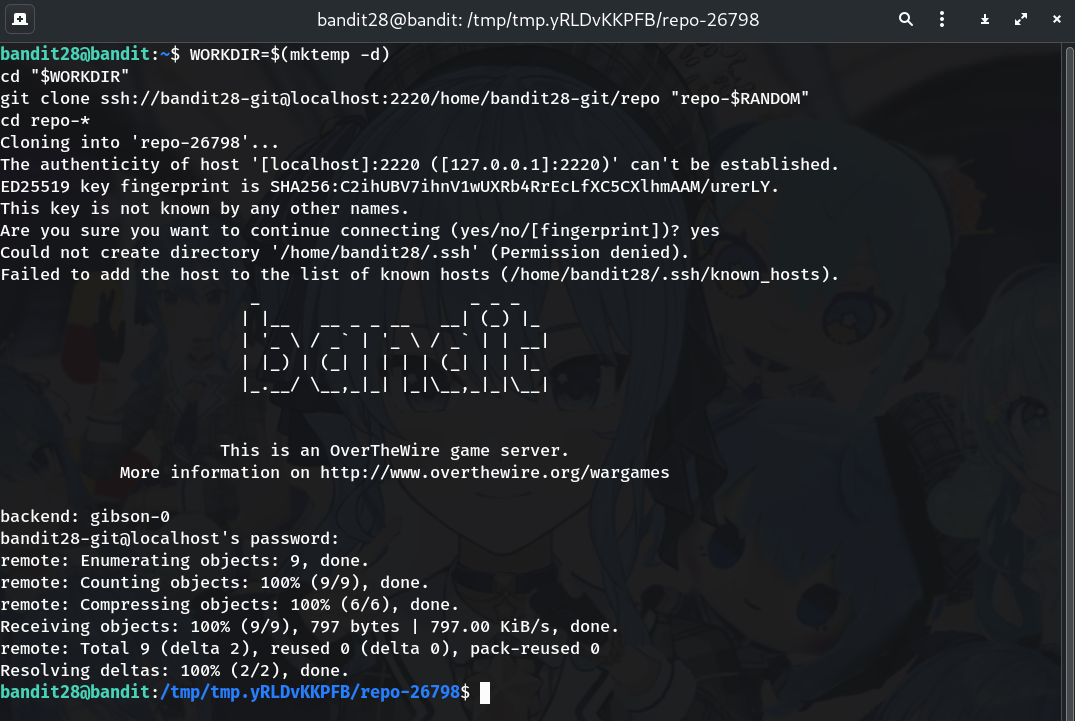
-
Open the README to see what’s currently shown
ls -la cat README.mdWhy? The README usually mentions credentials but hides the password (often as
xxxxxxxxxx). That’s your hint to check history.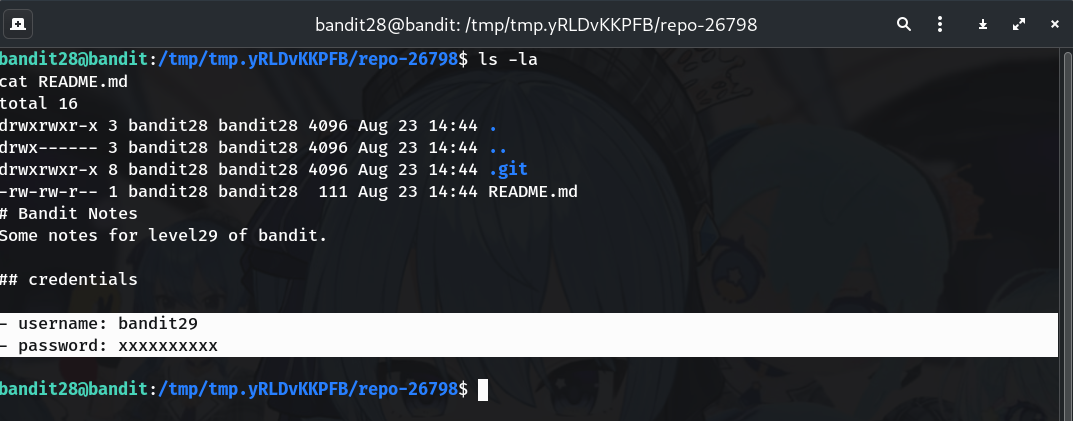
-
List commit history and spot the suspicious one
git log --oneline --decorateWhy? You’ll typically see something like:
fix info leak,add missing data,initial commit. The “fix info leak” commit suggests a secret was removed.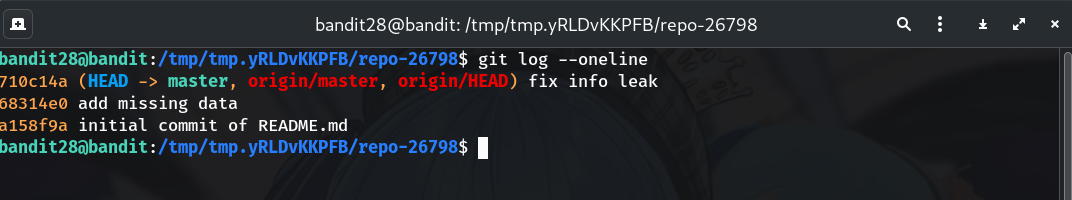
-
Show the diff of the leaking commit
# replace <hash> with the commit ID of "fix info leak" git show <hash>Why? The diff reveals that the README used to contain the actual password before it was redacted to
xxxxxxxxxx.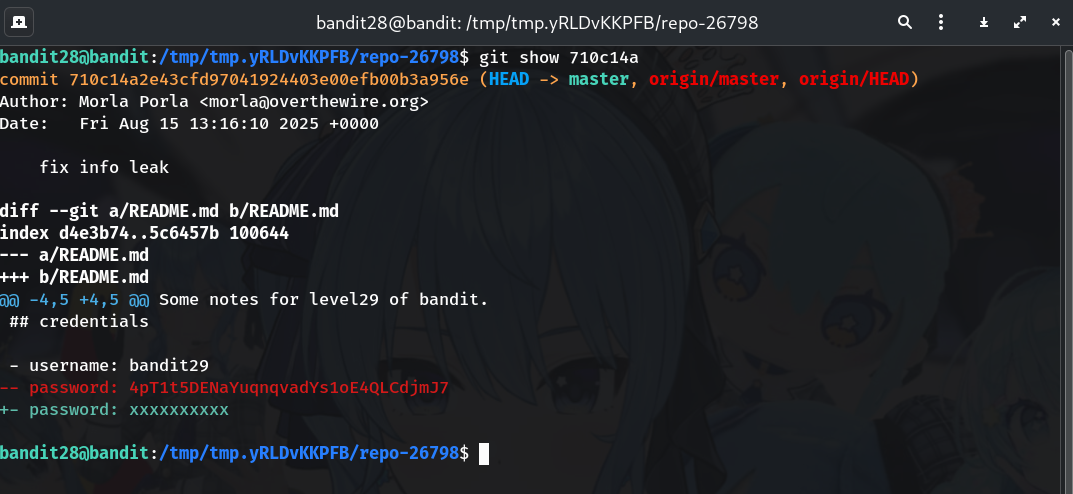
Password
This is the password revealed by the leaking commit on my run:
4pT1t5DENaYuqnqvadYs1oE4QLCdjmJ7
Troubleshooting
- Permission denied (publickey) → You’ll be prompted for bandit28’s password when cloning as
bandit28-git@localhoston port 2220. - “not a git repository” →
cdinto the cloned directory (e.g.,cd repo-*) before runninggit log/git show. - Commit not found → Use
git log --onelineto copy the exact hash of the “fix info leak” commit. - Nothing in README → That’s expected in the latest commit; the secret lives in the older revision’s diff.
Congrats 🎉 You performed git history forensics to recover a removed secret and unlocked bandit29!
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


