OverTheWire Bandit Level 27 → 28 tutorial!!
Login
Log in as bandit27 using the password you obtained from Level 26 → 27.
ssh bandit27@bandit.labs.overthewire.org -p 2220
# password: upsNCc7vzaRDx6oZC6GiR6ERwe1MowGB
Why? Each Bandit level is a separate UNIX user. To solve 27 → 28, you must be the
bandit27user.
Task
The home directory contains a git repository (served over SSH). Your task: clone it, explore the history, and recover the password for bandit28.
A little bit of Theory
- Git history lives in
.git/; earlier commits can still expose removed secrets. git logshows commits;git show <hash>displays the changes (or file contents at that commit).- If HEAD looks clean, the password is probably hidden in an older commit.
Further reading:
Solution
-
Clone the repository to a writable temp folder
WORKDIR=$(mktemp -d) cd "$WORKDIR" git clone ssh://bandit27-git@localhost:2220/home/bandit27-git/repo "repo-$RANDOM" cd repo-*Why?
/tmpis writable by you; cloning here avoids permission issues. When prompted for a password forbandit27-git, enter the bandit27 password.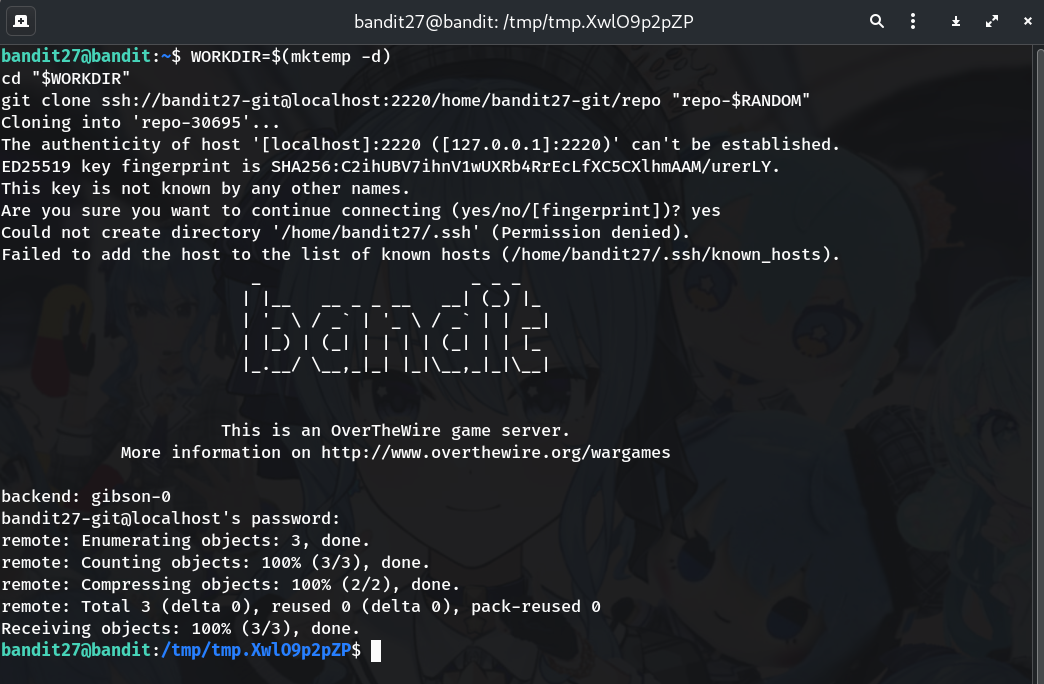
-
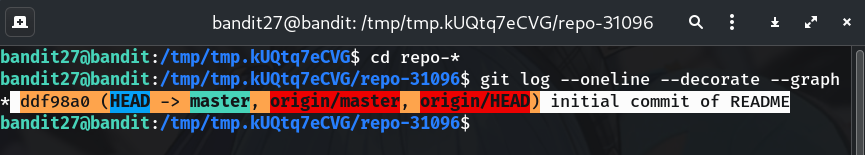
List the history
git log --oneline --decorate --graphWhy? A quick, readable view to spot the commit(s) that likely introduced/removed a secret.
-
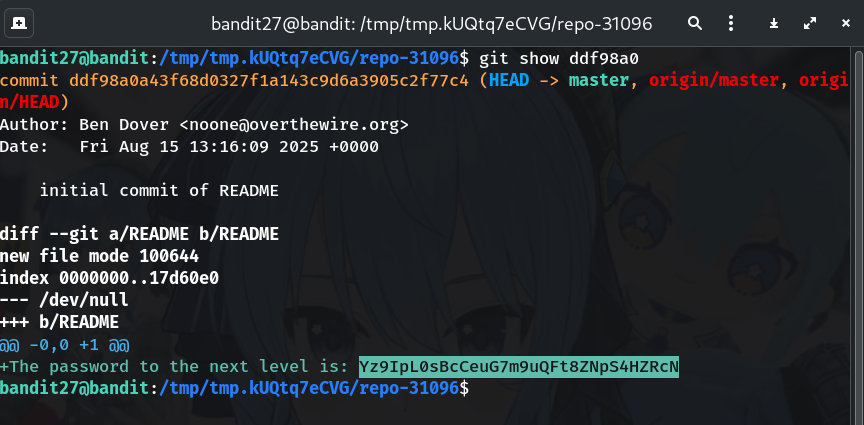
Show the commit content
git show <commit-id>Why? Inspect the README change; the password is typically added in the initial commit or an early one.
-
Extract the password
Copy the password string you find in the relevant commit.
Password
The password revealed in the commit on my run:
Yz9IpL0sBcCeuG7m9uQFt8ZNpS4HZRcN
Troubleshooting
- Permission denied (publickey) → The remote is
bandit27-git@localhoston port 2220; it prompts for your bandit27 password. - “not a git repository” → Make sure you
cd repobefore usinggit log/git show. - No secret in HEAD → Use
git logto step back through commits andgit show <hash>each one until you see it.
Congrats 🎉 You used git history forensics to recover a removed secret. On to bandit28!
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


