OverTheWire Bandit Level 26 → 27 tutorial!!
Login
Log in as bandit26 (use the key from Level 25 → 26, or the password if you have it).
ssh -i bandit26.sshkey -p 2220 bandit26@localhost
# or
ssh bandit26@bandit.labs.overthewire.org -p 2220
# password: s0773xxkk0MXfdqOfPRVr9L3jJBUOgCZ
Why? Each Bandit level is a separate UNIX user. To solve 26 → 27, you must be the
bandit26user first.
Task

“Good job getting a shell! Now hurry and grab the password for bandit27.” You’ll find a helper binary in bandit26’s home that can run commands as bandit27.
A little bit of Theory
- In Level 25 → 26, we escaped the restricted shell (
/usr/bin/showtext) viamore → v → vim → :set shell=/bin/bash → :shellto get a real shell. - In this level, the file
bandit27-doin bandit26’s home is a setuid-style helper that runs any command asbandit27. - So we can simply use it to read
/etc/bandit_pass/bandit27.
Further reading:
Solution
-
Ensure you really have an interactive shell as bandit26
If you get kicked out right away (because of
showtext), shrink your terminal somoreshows--More--, pressvto open Vim, then::set shell=/bin/bash :shellWhy? This is the same escape from Level 25 → 26 to obtain a usable shell.
-
List the home directory and discover the helper
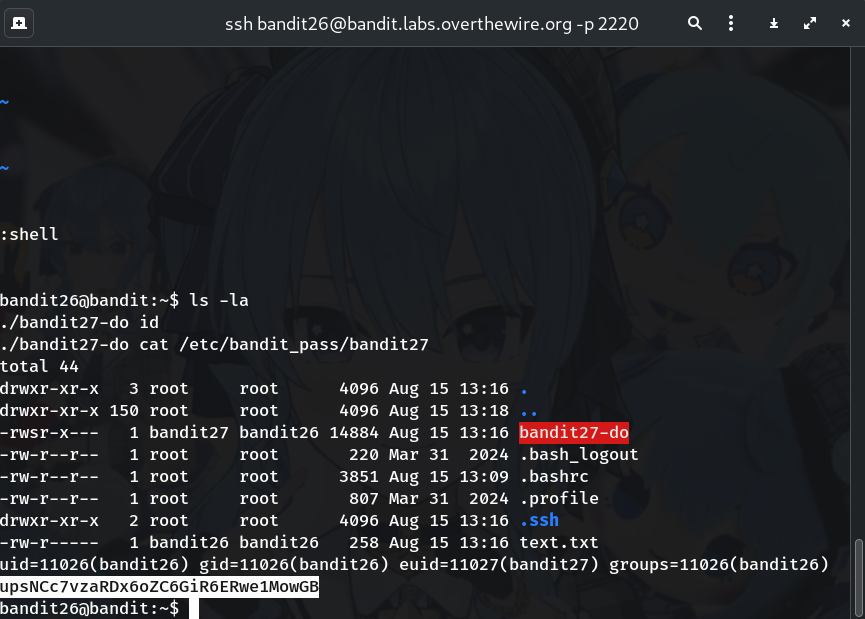
ls -laYou should see
bandit27-doandtext.txt.Why? The filename hints it runs commands as bandit27.
-
Check what the helper does
./bandit27-do # or: strings ./bandit27-doYou’ll see usage like:
Run a command as another user. Example: ./bandit27-do idWhy? Confirms it runs arbitrary commands with bandit27’s privileges.
-
Verify effective user
./bandit27-do idWhy? Sanity-check that commands run as bandit27.
-
Read the password for bandit27 using the helper
./bandit27-do cat /etc/bandit_pass/bandit27Why? This prints the next level’s password with bandit27’s permissions.
Password
Paste here the exact line printed by the helper (of course from your own run).
upsNCc7vzaRDx6oZC6GiR6ERwe1MowGB
Troubleshooting
- Still stuck in
showtext? → Make the terminal short, pressvto open Vim, then:set shell=/bin/bashand:shell. Permission deniedexecuting./bandit27-do→ Ensure you’re in/home/bandit26and the file is executable. If needed, run it with the absolute path:/home/bandit26/bandit27-do cat /etc/bandit_pass/bandit27- Got the wrong password? → Double-check you ran the helper on
/etc/bandit_pass/bandit27(notbandit26).
Congrats 🎉 You leveraged the bandit27-do helper to execute as bandit27 and retrieved the next credentials!
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


