OverTheWire Bandit Level 21 → 22 tutorial!!
Login
Log in as bandit21 using the password you obtained from Level 20 → 21.
ssh bandit21@bandit.labs.overthewire.org -p 2220
# password: EeoULMCra2q0dSkYj561DX7s1CpBuOBt
Why? Each Bandit level is a separate UNIX user. To solve 21 → 22, you must be the
bandit21user.
Task
A cron job is set up for the next user. Find what it does and use it to obtain the password for bandit22.
A little bit of Theory
- Cron runs commands on a schedule. Per-level jobs in Bandit are defined in
/etc/cron.d/and typically call a script. - The script often copies the next user’s password from
/etc/bandit_pass/<user>to a file in/tmp(world-readable). - Don’t guess the filename in
/tmp: read the script and use exactly the path it writes to.
Further reading:
Solution
-
List cron definitions
ls -l /etc/cron.dWhy? Identify the job file for this level, e.g.
cronjob_bandit22.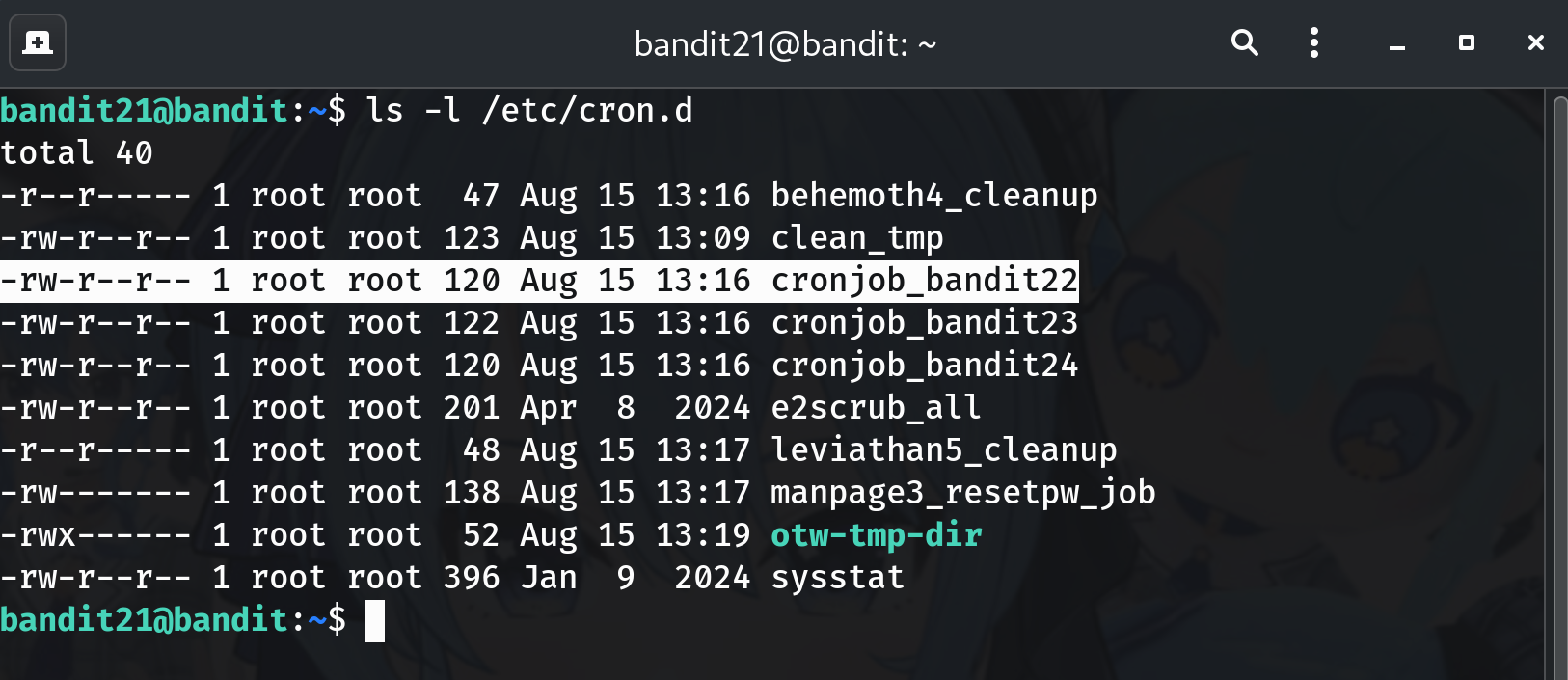
-
Read the cron entry
cat /etc/cron.d/cronjob_bandit22Example (from my run):
@reboot bandit22 /usr/bin/cronjob_bandit22.sh &> /dev/null * * * * * bandit22 /usr/bin/cronjob_bandit22.sh &> /dev/nullWhy? It runs
/usr/bin/cronjob_bandit22.shasbandit22every minute.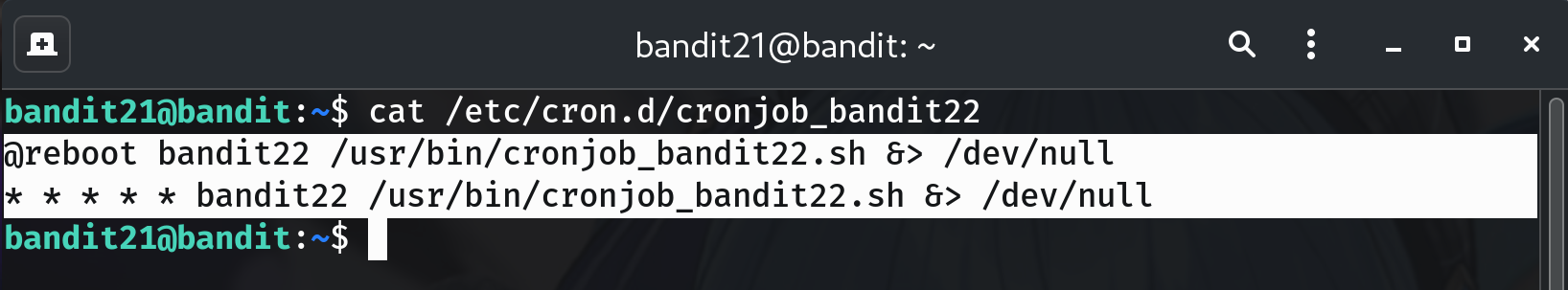
-
Open the referenced script and extract the output path
cat /usr/bin/cronjob_bandit22.sh # Quick way to capture the exact /tmp path: P=$(grep -o '/tmp/[^ >]*' /usr/bin/cronjob_bandit22.sh | head -n1) echo "Output path: $P"In my run the script is:
#!/bin/bash chmod 644 /tmp/t706lds9S0RqQh9aMcz6ShpAoZKF7fgv cat /etc/bandit_pass/bandit22 > /tmp/t706lds9S0RqQh9aMcz6ShpAoZKF7fgvWhy? We now know exactly which file in
/tmpto read.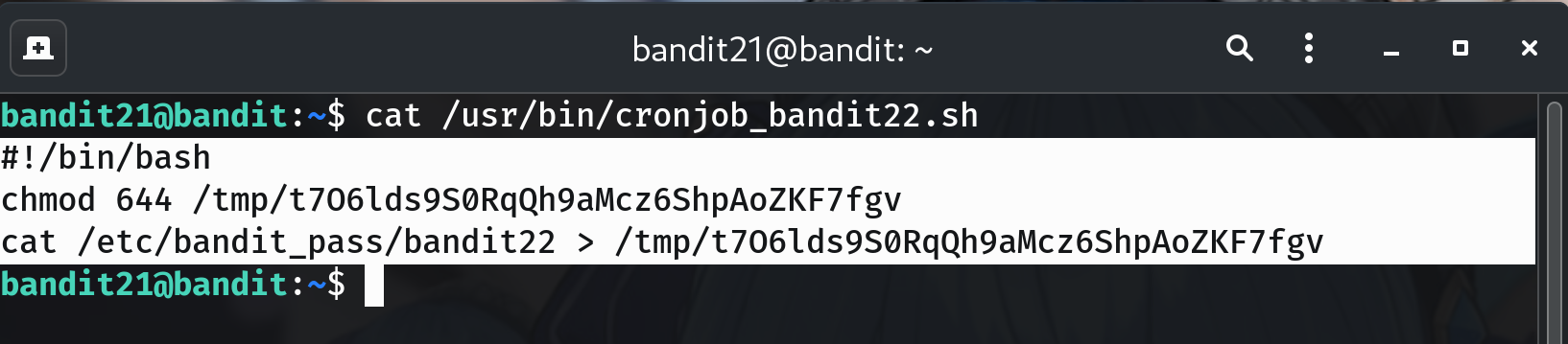
-
Read the file produced by the cron job
cat "$P" # or, using the concrete path from my run: # cat /tmp/t706lds9S0RqQh9aMcz6ShpAoZKF7fgvWhy? That file contains the password for
bandit22. If it’s missing, wait up to a minute for cron to run again.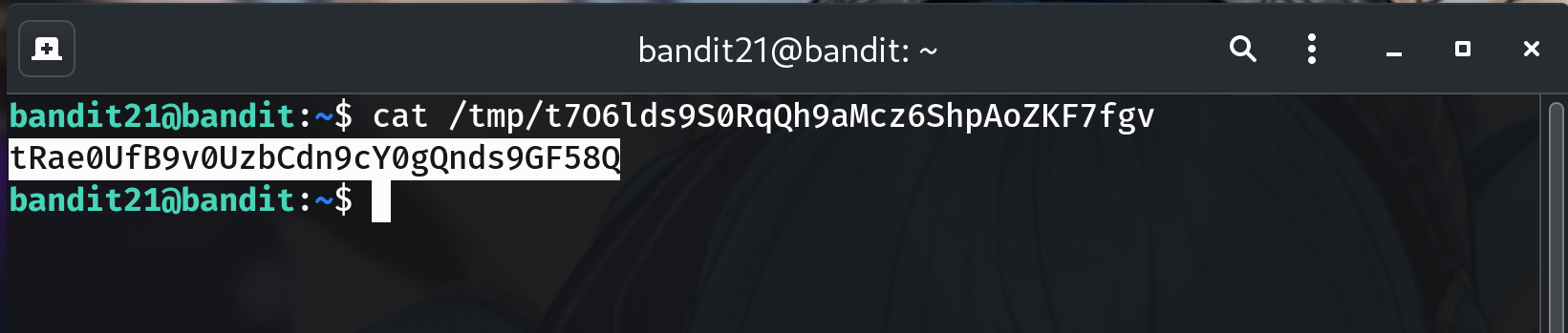
-
Copy the password (no trailing spaces/newlines).
-
Log into the next level (bandit22)
exit ssh bandit22@bandit.labs.overthewire.org -p 2220 # paste the password you just retrieved
Password
This is the password from my run; if yours differs, use the one your terminal printed.
tRae0UfB9v0UzbCdn9cY0gQnds9GF58Q
Troubleshooting
- Got “Please use “cd $(mktemp -d)”” → You looked at an old placeholder file (
/tmp/bandit22). Always read the actual path from the script. - File not found / empty → Cron runs every minute. Wait up to 60 seconds and retry.
-
Different path → Trust your
/usr/bin/cronjob_bandit22.sh. Extract the path via:grep -o '/tmp/[^ >]*' /usr/bin/cronjob_bandit22.sh | head -n1 - Permission denied → The output is world-readable (
chmod 644), but if perms differ on your run, just wait for the next cron run to re-apply.
Copy-paste quick run (one shot)
# Find the script and its /tmp output path, then read the password
cat /etc/cron.d/cronjob_bandit22
P=$(grep -o '/tmp/[^ >]*' /usr/bin/cronjob_bandit22.sh | head -n1)
echo "Output path: $P"
cat "$P"
# Then log in:
# ssh bandit22@bandit.labs.overthewire.org -p 2220
# (paste the line above)
Congrats 🎉 You traced a cron job and used it to retrieve the next password — welcome to bandit22!
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


