OverTheWire Bandit Level 20 → 21 tutorial!!
Login
Log in as bandit20 using the password you obtained from Level 19 → 20.
ssh bandit20@bandit.labs.overthewire.org -p 2220
# password: 0qXahG8ZjOVMN9Ghs7iOWsCfZyXOUbYO
Why? Each Bandit level is a separate UNIX user. To solve 20 → 21, you must be the
bandit20user.
Task
There is a setuid helper called suconnect in your home.
suconnect will connect to a TCP port on localhost and expects you to send the current password (for bandit20).
If the password is correct, it returns the password for bandit21 over the same connection.
A little bit of Theory
- setuid binaries run with the effective UID of the file owner. Here,
suconnectis owned bybandit21, so the connection it makes and the check it performs happen asbandit21. -
Plan:
- Start a Netcat listener on
localhost:<PORT>. - Run
./suconnect <PORT>so it dials your listener. - Type the bandit20 password into the listener → it replies with the bandit21 password.
- Start a Netcat listener on
-
Netcat flavors:
- OpenBSD:
nc -l 12345 - Traditional:
nc -l -p 12345
- OpenBSD:
Further reading:
Solution
-
Inspect the helper
ls -l file suconnect strings suconnect | headWhy? Confirms setuid (
-rwsr-x---) and usagesuconnect <port>.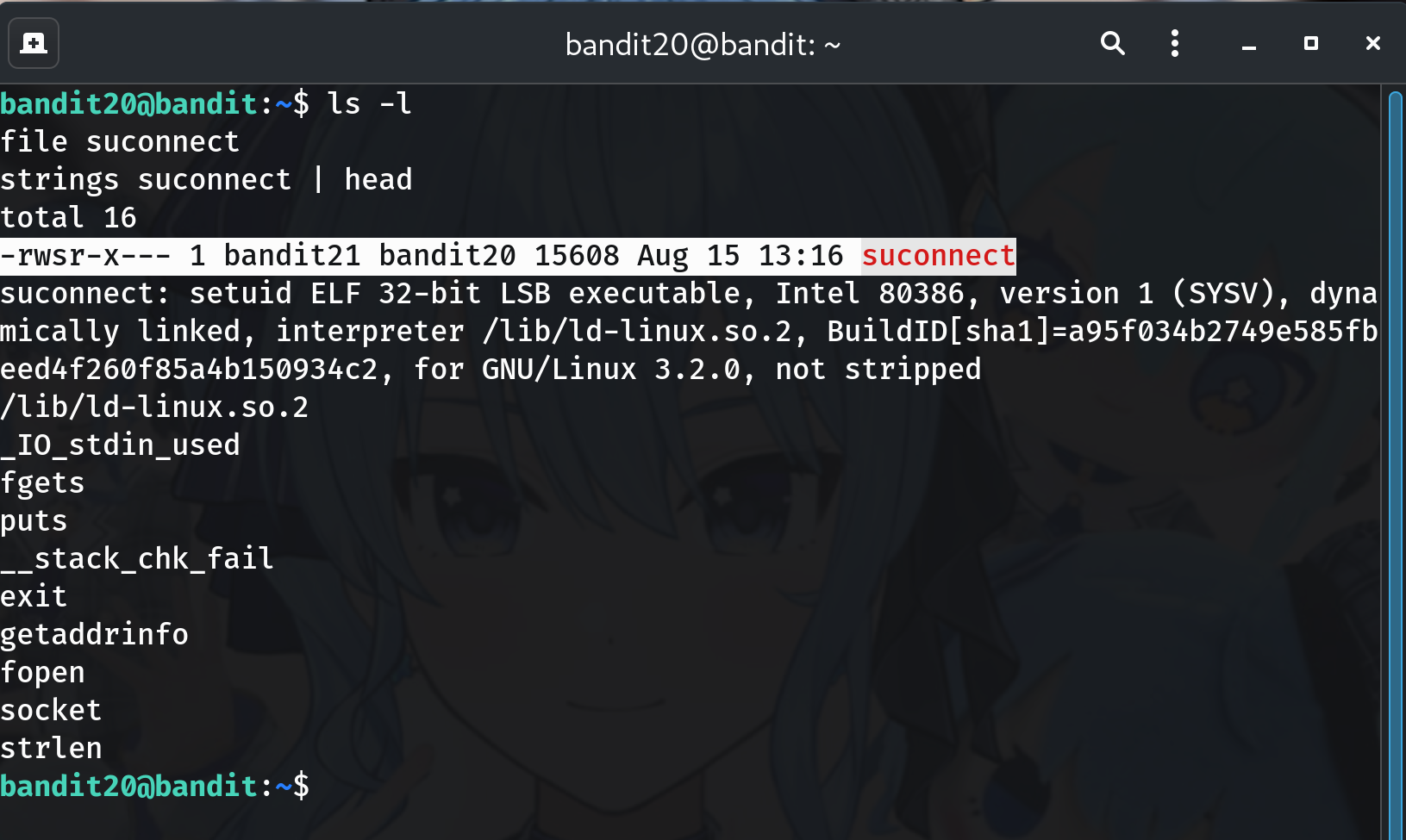
-
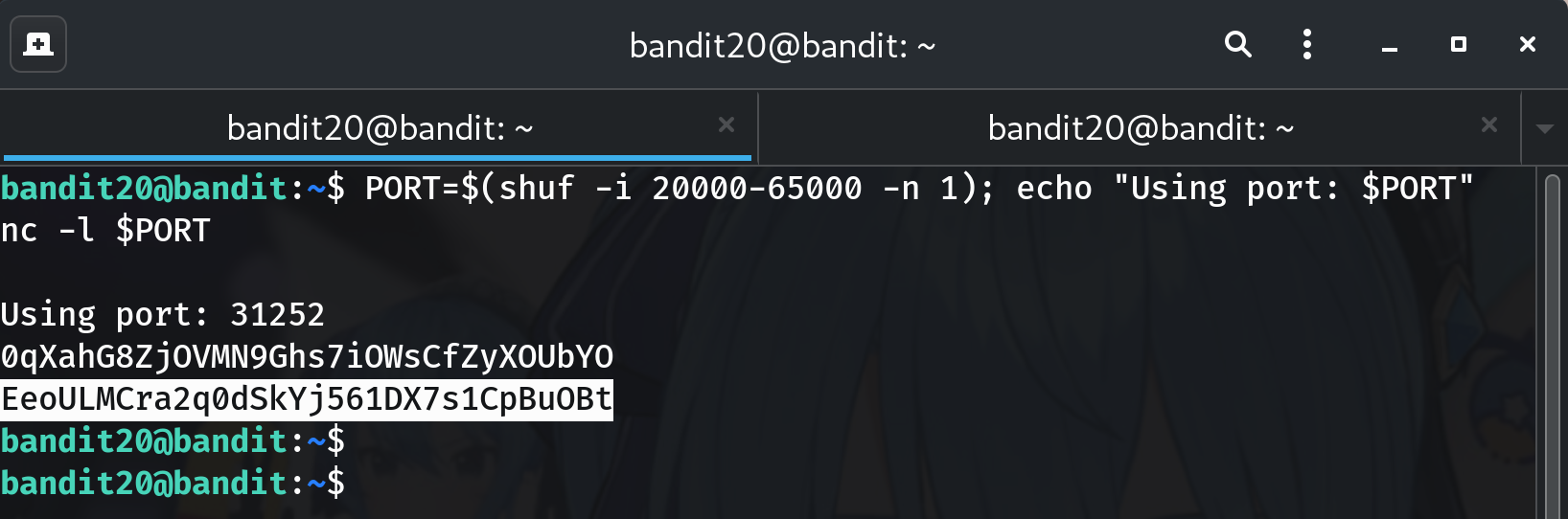
Start a listener on a random high port (Terminal A)
PORT=$(shuf -i 20000-65000 -n 1); echo "Using port: $PORT" nc -l $PORT # or: nc -l -p $PORTWhy? Avoid port collisions on the shared host.
-
Run the connector (Terminal B)
./suconnect $PORTWhy?
suconnect(running asbandit21) connects to your listener and waits for a line.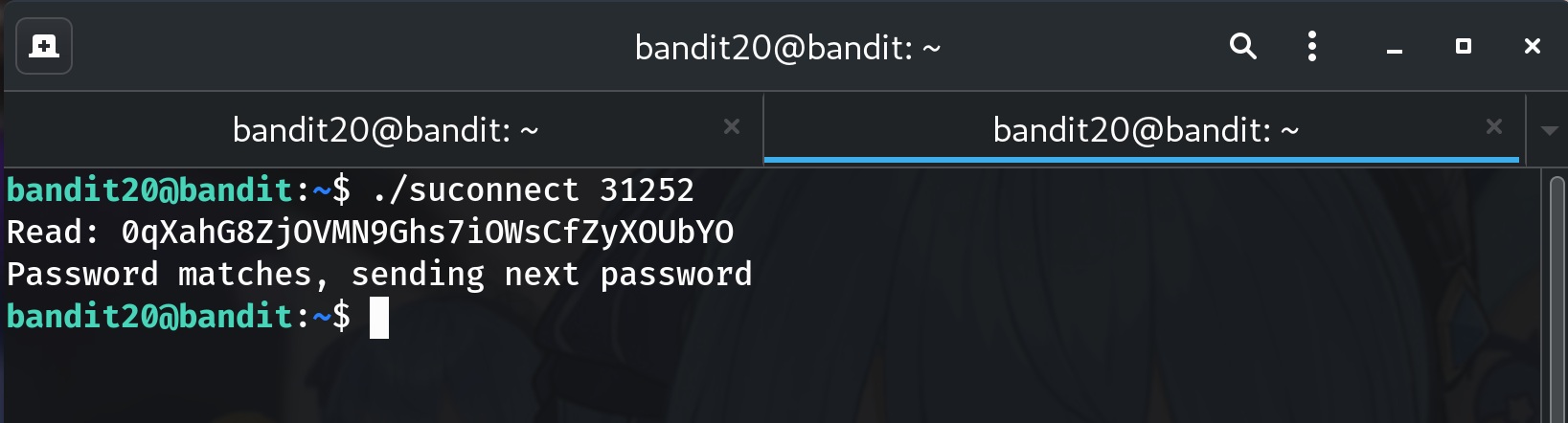
-
Send the current password (Terminal A)
Paste the bandit20 password and press Enter:
0qXahG8ZjOVMN9Ghs7iOWsCfZyXOUbYOYou should receive the bandit21 password back.
-
Copy the printed password (no trailing spaces/newlines).
-
Log into the next level (bandit21)
exit ssh bandit21@bandit.labs.overthewire.org -p 2220 # paste the password you just obtained
Password
This is the password from my run; if yours differs, use the one that your terminal printed.
EeoULMCra2q0dSkYj561DX7s1CpBuOBt
Troubleshooting
nc: Address already in use→ Pick another port, e.g.PORT=$(shuf -i 30000-65000 -n 1).- No response after typing → Press Enter to send a newline.
Connection refused→ Start the listener first, then run./suconnect.- Only one terminal? → Use
tmux(tmux; Ctrl+B ") or a second SSH session. - Garbage/extra spaces → Type the password carefully; only the exact line plus newline.
Copy-paste quick run (two terminals)
# Terminal A (listener)
PORT=$(shuf -i 20000-65000 -n 1); echo "Using port: $PORT"
nc -l $PORT # or: nc -l -p $PORT
# Terminal B (connector)
./suconnect $PORT
# Back to Terminal A: paste bandit20 password, press Enter → it prints bandit21 password.
Congrats 🎉 You used a setuid connector and a local listener to exfiltrate the next password — welcome to bandit21!
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


