OverTheWire Bandit Level 19 → 20 tutorial!!
Login
Log in as bandit19 using the password you obtained from Level 18 → 19.
ssh bandit19@bandit.labs.overthewire.org -p 2220
# password: cGWpMaKXVwDUNgPAVJbWYuGHVn9zl3j8
Why? Each Bandit level is a separate UNIX user. To solve 19 → 20, you must be the
bandit19user.
Task
There is a setuid helper binary in your home directory: bandit20-do.
It runs a command as user bandit20.
The password for the next level is stored in /etc/bandit_pass/bandit20. Use the helper to read it.
A little bit of Theory
- setuid: if an executable has the s bit on user perms (e.g.,
-rwsr-x---), it runs with the file owner’s EUID. Here,bandit20-dois owned bybandit20, so commands it executes run asbandit20. -
The helper likely takes a command line such as:
./bandit20-do <command> [args...]so we can have it run
/bin/cat /etc/bandit_pass/bandit20.
Further reading:
Solution
-
Inspect the helper binary
ls -lWhy? You should see
bandit20-dowith the s bit set (rws).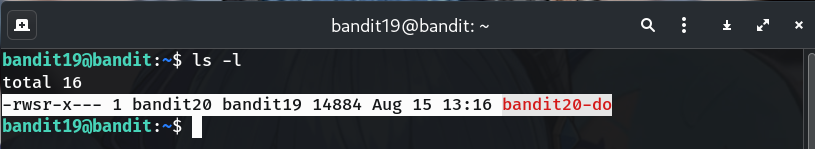
-
Read the built-in usage (optional)
./bandit20-do # or try a harmless command: ./bandit20-do idWhy? Confirms it runs as
bandit20(look foruid=11020(bandit20)in output).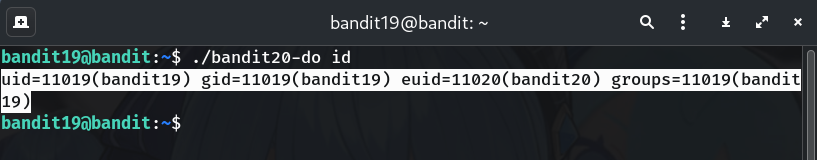
-
Use the helper to print the password file
./bandit20-do /bin/cat /etc/bandit_pass/bandit20Why? We ask it to execute
catas bandit20, so it can read that file.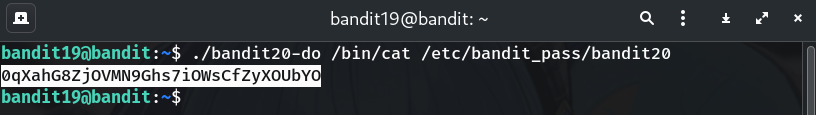
-
Copy the password (no trailing spaces/newlines).
-
Log into the next level (bandit20)
exit ssh bandit20@bandit.labs.overthewire.org -p 2220 # paste the password you just printed
Password
This is the password from my run; if yours differs, use the one your terminal printed.
0qXahG8ZjOVMN9Ghs7iOWsCfZyXOUbYO
Troubleshooting
-
“Permission denied” when reading the file → You forgot to use the helper or used plain
cat. Must be:./bandit20-do /bin/cat /etc/bandit_pass/bandit20 - “No such file or directory” → Double-check the exact path
/etc/bandit_pass/bandit20and that you ran./bandit20-dofrom~. - Helper says “Run a command as another user” and exits → You didn’t pass a command; try
./bandit20-do idfirst. - Command not found → Use absolute path
/bin/catto avoid PATH issues.
Congrats 🎉 You used a setuid helper to execute a command as another user — welcome to bandit20!
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


