OverTheWire Bandit Level 18 → 19 tutorial!!
Login
Log in as bandit18 using the password you obtained from Level 17 → 18.
ssh bandit18@bandit.labs.overthewire.org -p 2220
# password: x2gLTTjFwMOhQ8oWNbMN362QKxfRqGlO
Why? Each Bandit level is a separate UNIX user. To solve 18 → 19, you must be the
bandit18user.
Task
The password for the next level is stored in a file called readme in the home directory.
Problem: Someone modified .bashrc to log you out immediately on SSH login.
A little bit of Theory
- Interactive shells read
~/.bashrcand can be scripted toexitright away (you’ll seeByebye!). - You can bypass interactive login by asking SSH to run a command directly (non-interactive), e.g.
cat readme. - Alternatives:
scp/sftpto pull the file without opening an interactive shell.
Further reading:
Solution
-
Observe the trap (optional)
ssh bandit18@bandit.labs.overthewire.org -p 2220Why? You’ll be kicked out immediately due to
.bashrc. That’s the point of the level.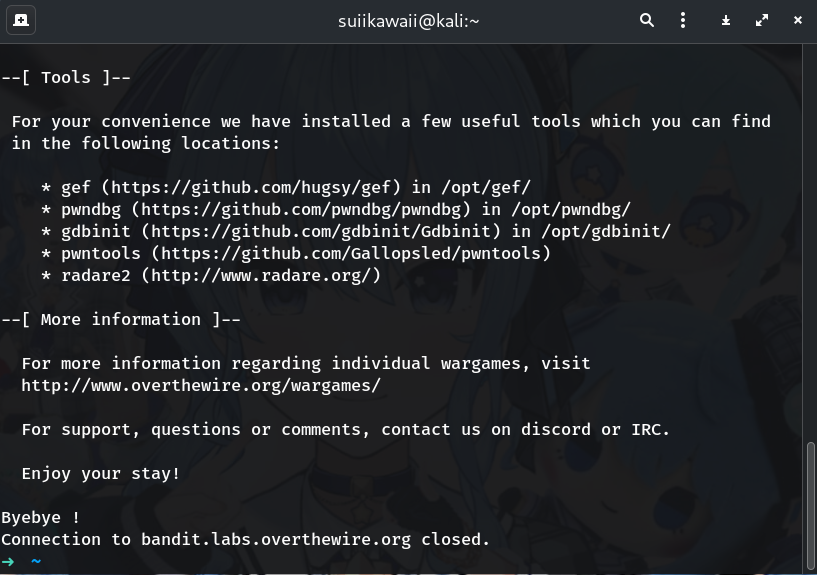
-
(Option A) Run a remote command with SSH (recommended)
ssh -p 2220 bandit18@bandit.labs.overthewire.org 'cat readme'Why? This executes
cat readmewithout launching an interactive shell, so.bashrcdoesn’t log you out. If you prefer absolute paths:ssh -p 2220 bandit18@bandit.labs.overthewire.org 'cat /home/bandit18/readme'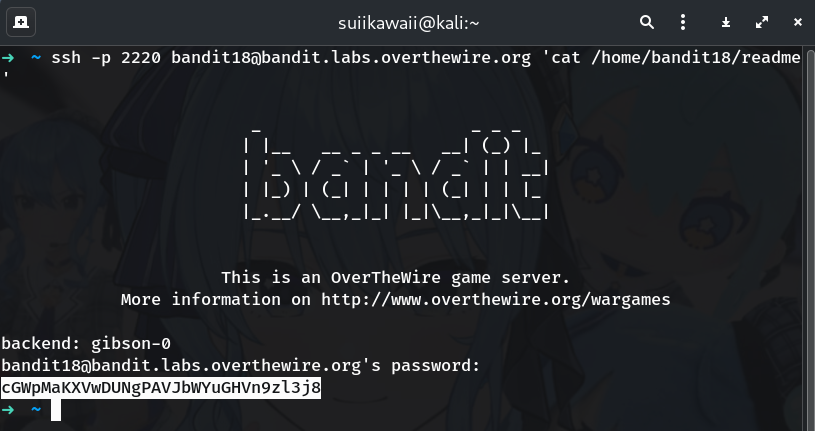
-
(Option B) Copy the file out with
scpTo stdout:
scp -P 2220 bandit18@bandit.labs.overthewire.org:readme -To a local file:
scp -P 2220 bandit18@bandit.labs.overthewire.org:readme ./bandit19.pass cat ./bandit19.pass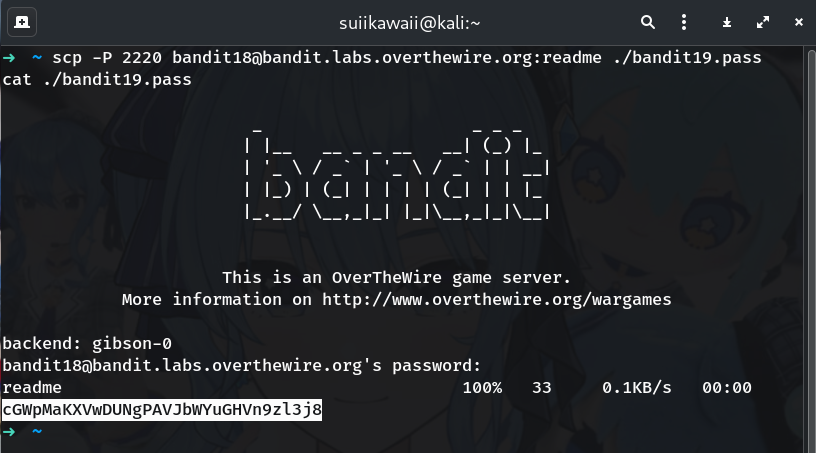
-
(Option C) Use
sftpsftp -P 2220 bandit18@bandit.labs.overthewire.org sftp> get readme - sftp> bye
-
Copy the password printed from the file (no trailing spaces/newlines).
-
Log into the next level (bandit19)
ssh bandit19@bandit.labs.overthewire.org -p 2220 # paste the password you just extracted
Password
This is the password from my run; if yours differs, use the one your terminal printed.
cGWpMaKXVwDUNgPAVJbWYuGHVn9zl3j8
Troubleshooting
- Still seeing
Byebye!? → Ensure you used the remote command form (quotes matter):ssh -p 2220 bandit18@bandit.labs.overthewire.org 'cat readme' - Permission denied (publickey)? → You accidentally tried logging with a key instead of a password. Use the password from 17 → 18.
- Weird characters/newlines → Re-run and copy only the line printed by
cat readme. - Command not found → Use absolute path:
'/bin/cat /home/bandit18/readme'.
Copy-paste quick run (one shot)
# Print the password without opening an interactive shell
ssh -p 2220 bandit18@bandit.labs.overthewire.org 'cat /home/bandit18/readme'
# Then log into the next level:
# ssh bandit19@bandit.labs.overthewire.org -p 2220
# (paste the printed line as the password)
Congrats 🎉 You bypassed the interactive shell trap and extracted the next password — welcome to bandit19!
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


