OverTheWire Bandit Level 17 → 18 tutorial!!
Login
Log in as bandit17 using the private key you obtained from Level 16 → 17.
ssh -i ./bandit17.key bandit17@bandit.labs.overthewire.org -p 2220
# auth: use the RSA private key from the previous level
Why? Each Bandit level is a separate UNIX user. To solve 17 → 18, you must be the
bandit17user.
Task
There are two files in your home directory: passwords.old and passwords.new.
The password for the next level is the only line that exists in passwords.new but not in passwords.old.
A little bit of Theory
diffshows line-by-line differences between two files. With unified format (-u), new lines are prefixed with+.-
grep -Fxv -f A Bprints lines in B that do not appear in A:-Ffixed strings,-xwhole line match,-vinvert match,-f Aread patterns from file A.
commcompares sorted files:comm -13 <(sort A) <(sort B)= lines unique to B.
Further reading:
Solution
-
List files to confirm they exist
ls -lWhy? Sanity check: both
passwords.oldandpasswords.newshould be here.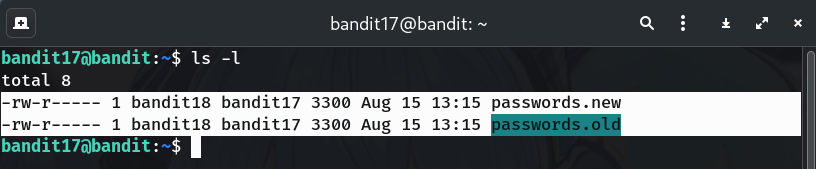
-
(Option A) Use
grepto print the new unique linegrep -Fxv -f passwords.old passwords.newWhy? Prints exactly the line that appears only in
passwords.new— that line is the password.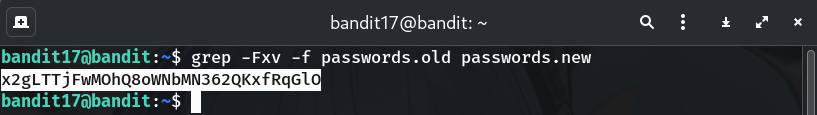
-
(Option B) Use
diff -uand filter the+linediff -u passwords.old passwords.new | grep '^+' | grep -v '+++ ' | cut -c2-Why? Unified diff shows additions with
+. We drop the header (+++) and the leading+.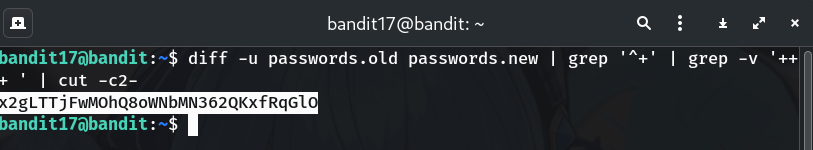
-
(Option C) Use
comm(requires sorted input)comm -13 <(sort passwords.old) <(sort passwords.new)Why? Column 3 (
-13) = lines unique to the second file.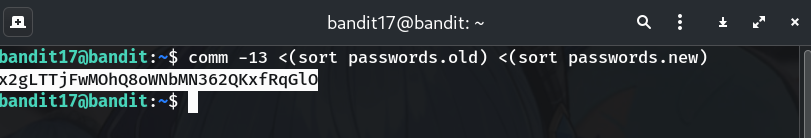
-
Copy the password (no trailing spaces/newlines).
-
Log into the next level (bandit18)
exit # go back to your local shell ssh bandit18@bandit.labs.overthewire.org -p 2220 # paste the password you just found when prompted
Password
This is the password from my run; if yours differs, use the one your terminal printed.
x2gLTTjFwMOhQ8oWNbMN362QKxfRqGlO
Troubleshooting
- Nothing prints? → Make sure you didn’t swap file order. It must be
-f passwords.old passwords.new. -
Multiple lines printed? → Your files might contain duplicates or trailing spaces. Normalize first:
sed -e 's/[[:space:]]\+$//' passwords.old > old.norm sed -e 's/[[:space:]]\+$//' passwords.new > new.norm grep -Fxv -f old.norm new.norm commreturns unexpected output → Remember both inputs must be sorted.- Clipboard issues → Use the mouse to select and copy only the password line; avoid extra spaces.
- Note from Bandit site: If you already solved this level and see
Byebye!when trying to log into bandit18 later, that’s tied to the next level’s twist (bandit19). Keep going.
Copy-paste quick run (one shot)
# Print the password (the line present in passwords.new but not in passwords.old)
grep -Fxv -f passwords.old passwords.new
# Then, from your local shell:
# ssh bandit18@bandit.labs.overthewire.org -p 2220
# (paste the line as the password when prompted)
Congrats 🎉 You diffed the files and extracted the next password — welcome to bandit18!
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


