OverTheWire Bandit Level 16 → 17 tutorial!!
Login
Log in as bandit16 using the password you just obtained from Level 15 → 16.
ssh bandit16@bandit.labs.overthewire.org -p 2220
# password: kSkvUpMQ7lBYyCM4GBPvCvT1BfWRy0Dx
Why? Each Bandit level is a separate UNIX user. To solve 16 → 17, you must be the
bandit16user.
Task
The credentials for the next level can be retrieved by submitting the current password to one port in the range 31000–32000 on localhost.
A little bit of Theory
- Use
nmap -sVto scan the range and detect services; look for entries that talk SSL/TLS (they appear asssl/*). - Use
openssl s_clientto open a minimal TLS session and send a single line (your current password). - The server returns an RSA private key for
bandit17— not a plaintext password. Save it, restrict permissions, thenssh -i. - You cannot write in
/home/bandit16; create files in/tmpinstead. Also,bandit16cannot create~/.ssh/known_hosts, so we pass SSH options to skip it.
Further reading:
Solution
-
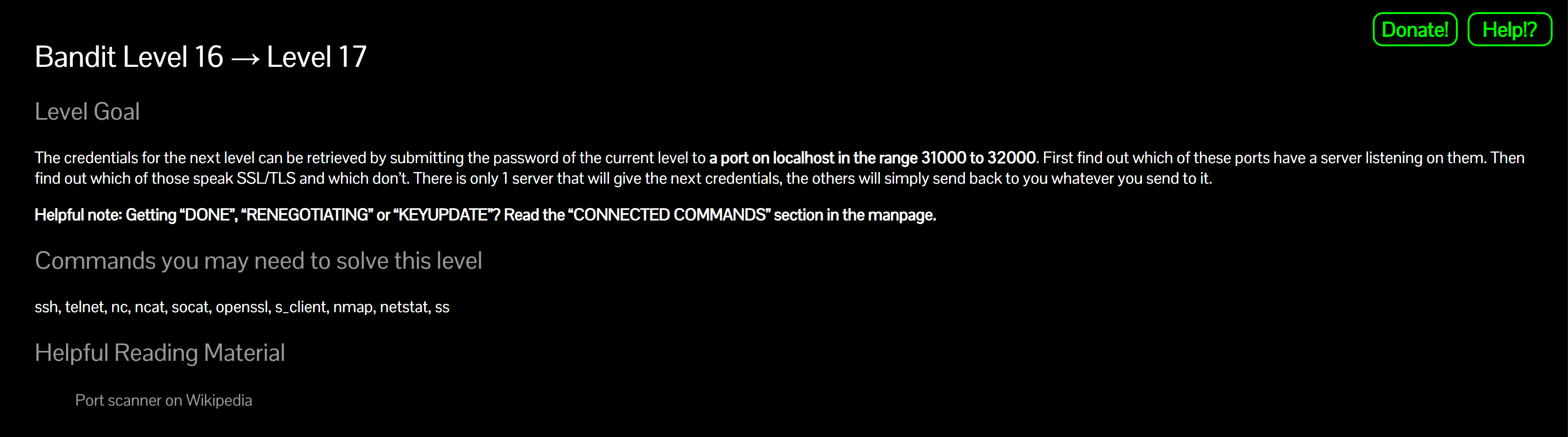
Scan the target range with version detection
nmap -p31000-32000 -sV localhostWhy? We need open ports and which ones speak TLS.
Typical output:
PORT STATE SERVICE VERSION 31046/tcp open echo 31518/tcp open ssl/echo 31691/tcp open echo 31790/tcp open ssl/unknown 31960/tcp open echo→ Candidates are 31518 and 31790 (both SSL/TLS).
-
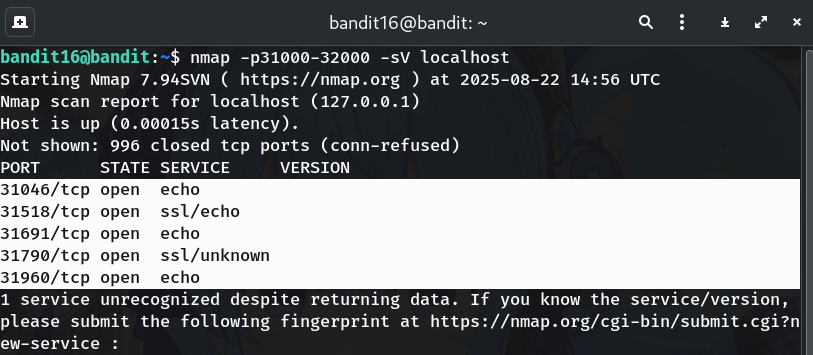
Connect to the likely TLS port and keep it quiet
Try 31790 first:
openssl s_client -connect localhost:31790 -quietWhy?
-quiethides certificate noise; a self-signed warning is expected. -
Send the current password
Paste the password for
bandit16and press Enter:kSkvUpMQ7lBYyCM4GBPvCvT1BfWRy0DxIf the port is correct, the service prints an RSA private key block. If it answers Wrong! try the other TLS port (31518).
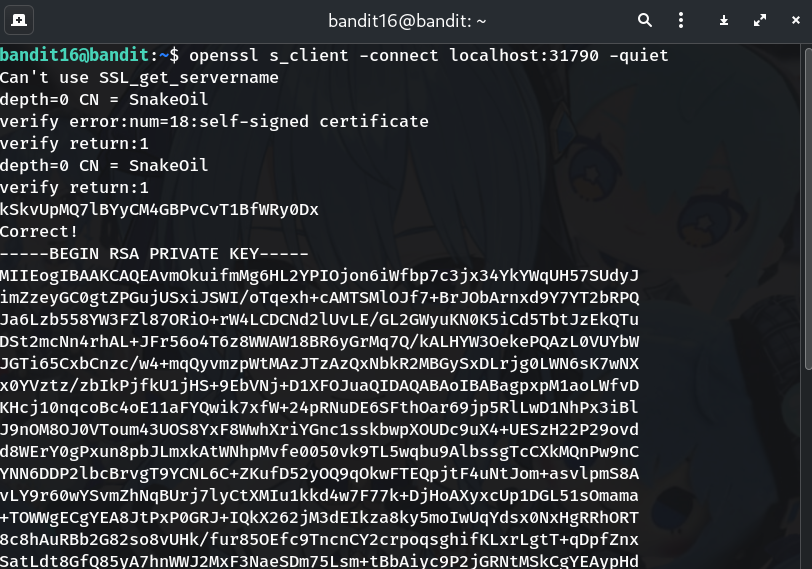
-
Create a writable workspace and save the key (exactly)
WORKDIR=$(mktemp -d /tmp/b16.XXXXXX) cd "$WORKDIR" cat > bandit17.key # paste the whole block: # -----BEGIN RSA PRIVATE KEY----- # ... # -----END RSA PRIVATE KEY----- # then press Ctrl+DWhy?
~is not writable forbandit16;/tmpis.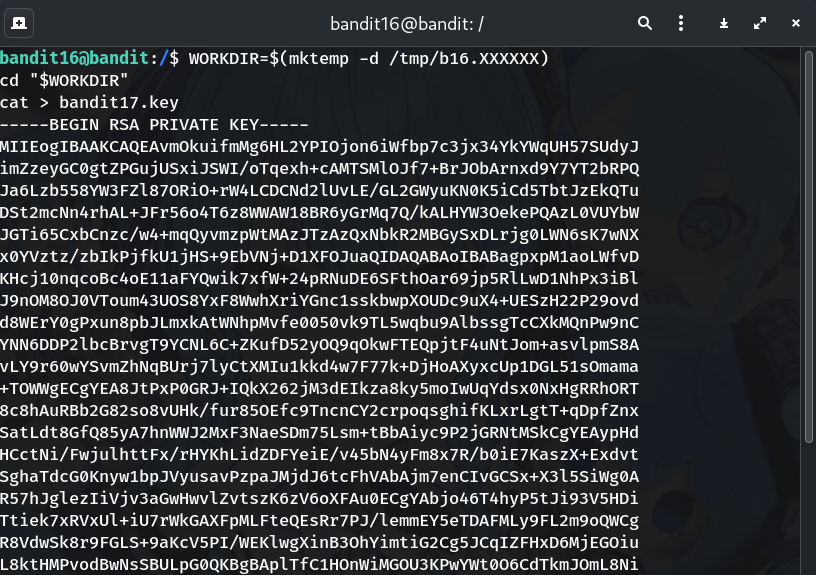
-
Fix permissions (required by SSH)
chmod 600 bandit17.key -
Log in to bandit17 with the key
ssh -o IdentitiesOnly=yes \ -o UserKnownHostsFile=/dev/null -o StrictHostKeyChecking=no \ -i ./bandit17.key bandit17@bandit.labs.overthewire.org -p 2220Why? We force SSH to use only this key and skip writing
~/.ssh/known_hosts(not writable here).

Password
This level returns an RSA private key (not a plaintext string). Save the entire block and use it with
ssh -i.
-----BEGIN RSA PRIVATE KEY-----
(…many lines…)
-----END RSA PRIVATE KEY-----
Troubleshooting
- “Permission denied (publickey)” → The key was mangled or permissions are too open. Re-grab the key and
chmod 600 bandit17.key. Ensure you used-o IdentitiesOnly=yes -i ./bandit17.key. - Can’t save the key in home → Use
/tmp(home is not writable forbandit16). - Only “Wrong!” appears → You pasted the wrong password or used the wrong TLS port. Try the other one (31518 vs 31790).
- Session stuck after printing the key → Press Ctrl+D to send EOF and return to your shell.
-
Still failing? → Inspect with verbose SSH:
ssh -vvv -o IdentitiesOnly=yes \ -o UserKnownHostsFile=/dev/null -o StrictHostKeyChecking=no \ -i ./bandit17.key bandit17@bandit.labs.overthewire.org -p 2220
Copy-paste quick run (one shot)
# Create a writable temp dir and go there
WORKDIR=$(mktemp -d /tmp/b16.XXXXXX) && cd "$WORKDIR"
# Try both TLS ports, extract the key block automatically
PW='kSkvUpMQ7lBYyCM4GBPvCvT1BfWRy0Dx'
for p in 31790 31518; do
echo "$PW" | openssl s_client -connect localhost:$p -quiet 2>/dev/null \
| awk '/BEGIN RSA PRIVATE KEY/,/END RSA PRIVATE KEY/' > bandit17.key
if [ -s bandit17.key ]; then
echo "[+] Got key from port $p"
break
fi
done
chmod 600 bandit17.key
# Login with the key (skip known_hosts writes)
ssh -o IdentitiesOnly=yes \
-o UserKnownHostsFile=/dev/null -o StrictHostKeyChecking=no \
-i ./bandit17.key bandit17@bandit.labs.overthewire.org -p 2220
Congrats 🎉 You scanned, spoke TLS, and authenticated with a private key — welcome to bandit17!
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


