OverTheWire Bandit Level 15 → 16 tutorial!!
Login
Log in as bandit15 using the password you just obtained from Level 14 → 15.
ssh bandit15@bandit.labs.overthewire.org -p 2220
# password: 8xCjnmgoKbGLhHFAZlGE5Tmu4M2tKJQo
Why? Each Bandit level is a different UNIX user. To solve 15 → 16 you must be logged in as
bandit15.
Task
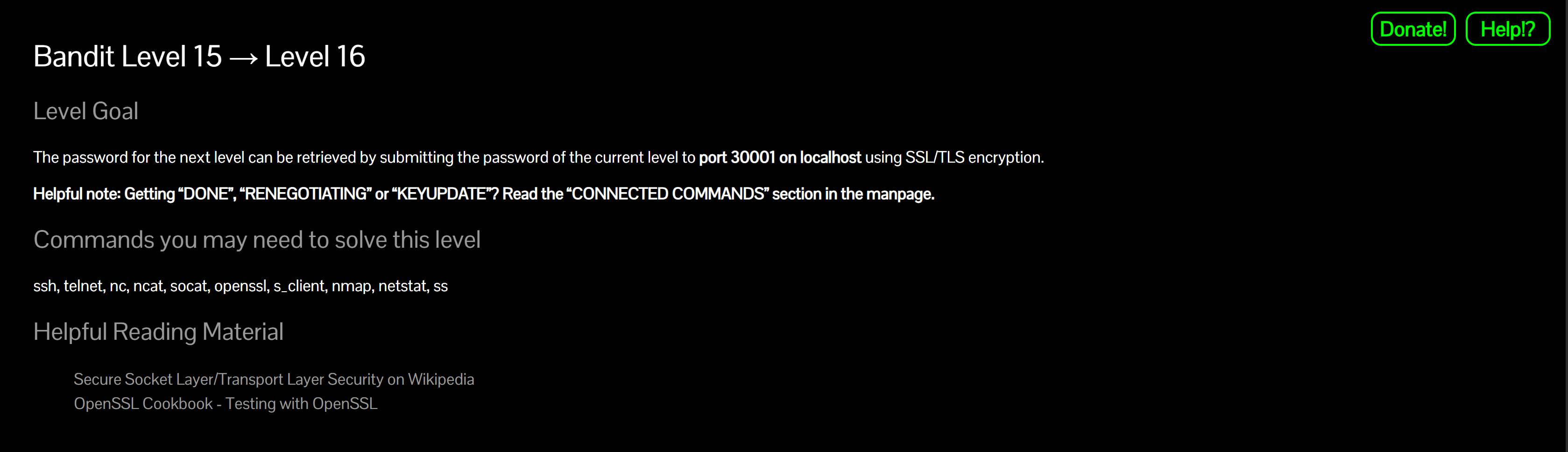
Send the current level password over a TLS/SSL connection to localhost port 30001. The service will reply with the password for bandit16.
A little bit of Theory
- Plain TCP vs TLS. Level 14 used plain TCP (
nc). This level is the same idea but wrapped in TLS (encrypted socket + certificate exchange). openssl s_client. A tiny TLS client. It connects, prints the handshake/cert info, then lets you type/send data to the service.- Newline matters. These services usually read a line; end your input with
\n. Useprintf '%s\n' ....
Further reading:
- OpenSSL:
openssl s_client(official manual) - OpenSSL Cookbook — Testing with OpenSSL
- Transport Layer Security (TLS)
nc(netcat) manual — OpenBSD · Debian mirror- Localhost (Wikipedia)
Solution
Way A — Interactive with openssl s_client
-
Open a TLS connection to the local service
openssl s_client -connect localhost:30001Why? This performs the TLS handshake and drops you into an interactive session bound to localhost:30001. A self-signed certificate warning is expected on the Bandit test service.
-
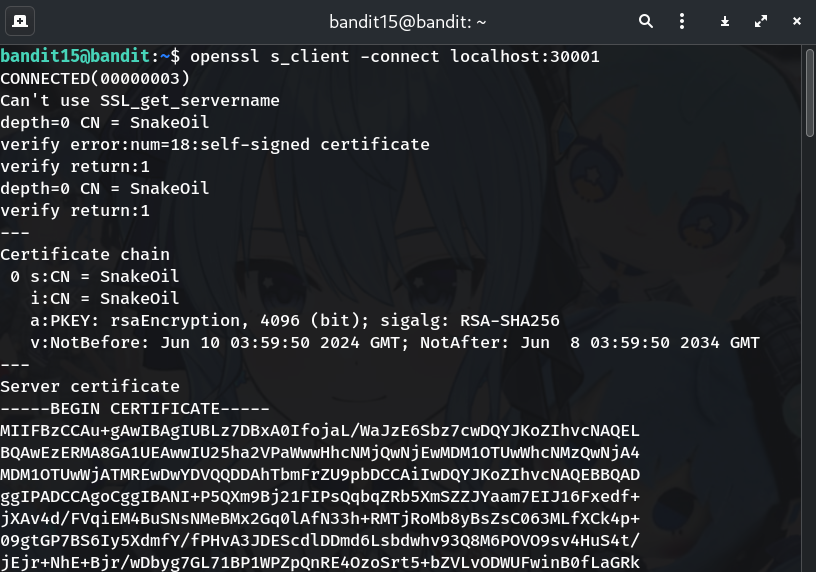
Type/paste the current password, then press Enter
8xCjnmgoKbGLhHFAZlGE5Tmu4M2tKJQoWhy? The service verifies your input and, if correct, prints bandit16’s password.
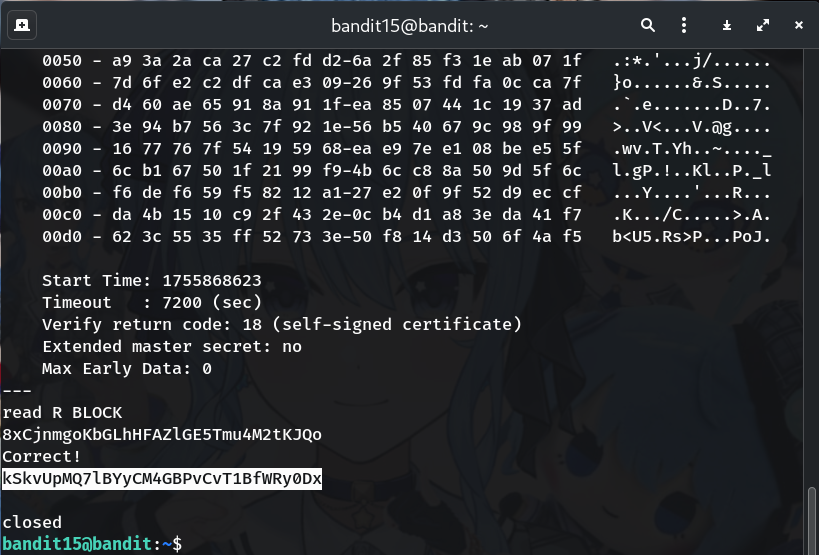
- Copy the returned password (avoid extra whitespace).
-
Log into the next level (bandit16)
exit ssh bandit16@bandit.labs.overthewire.org -p 2220 # paste the password you just found when prompted
Too chatty? Add
-quietto hide the certificate dump:
openssl s_client -connect localhost:30001 -quiet
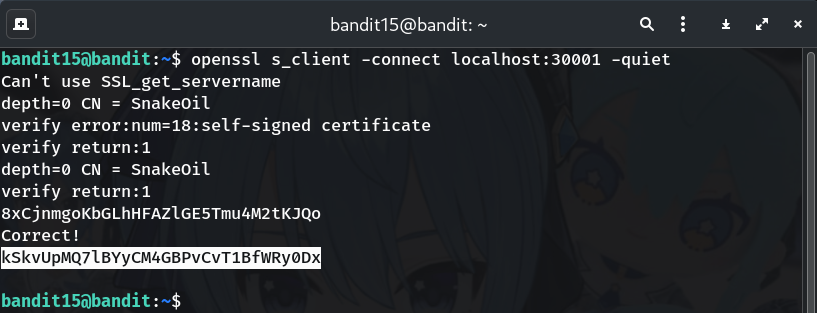
This makes the output shorter and easier to read.
Way B — Clean one-liner (recommended)
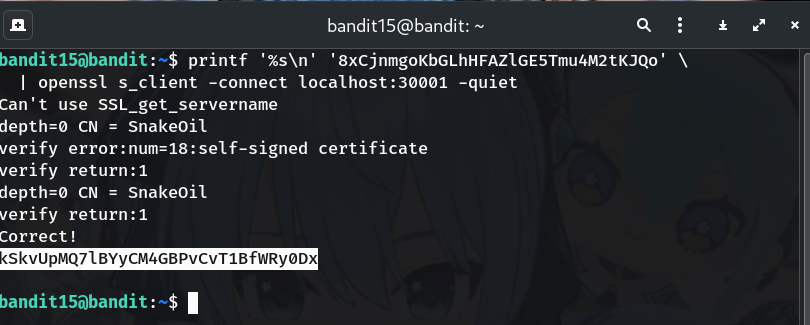
printf '%s\n' '8xCjnmgoKbGLhHFAZlGE5Tmu4M2tKJQo' \
| openssl s_client -connect localhost:30001 -quiet
Why? printf guarantees the trailing newline; -quiet suppresses handshake noise so you only see the result.
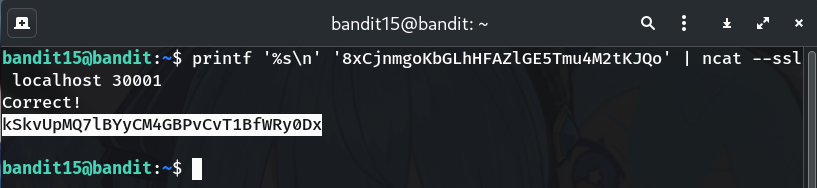
Way C — Using ncat (TLS-capable netcat)
printf '%s\n' '8xCjnmgoKbGLhHFAZlGE5Tmu4M2tKJQo' | ncat --ssl localhost 30001
Why? ncat (from Nmap) supports TLS via --ssl, giving you a netcat-style alternative.
Password
This is the password I got in my run; if yours differs, copy the one shown in your terminal.
kSkvUpMQ7lBYyCM4GBPvCvT1BfWRy0Dx
Troubleshooting
- Self-signed certificate warnings? Normal on Bandit. They don’t block the exchange. Use
-quietif the output is too noisy. - No output / “hangs”. You probably didn’t send a newline. Prefer the one-liner with
printf '%s\n' ... | openssl s_client -quiet. connect: Connection refused. Make sure you’re on the Bandit host asbandit15, and the port is 30001.- Echoed input but no “Correct!”. Double-check you pasted the correct bandit15 password and sent the newline.
Congrats 🎉 You spoke TLS with openssl s_client and grabbed the Level 16 password. See you in Level 16 → 17!
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


