OverTheWire Bandit Level 14 → 15 tutorial!!
Login
Log in as bandit14 using the password you just obtained from Level 13 → 14.
ssh bandit14@bandit.labs.overthewire.org -p 2220
# password: MU4VWeTyJk8ROof1qqmcBPaLh7lDCPvS
Why? Each Bandit level is a different UNIX user. To solve 14 → 15 you must be logged in as
bandit14.
Task
The password for the next level can be retrieved by sending the current password to port 30000 on localhost.
A little bit of Theory
localhostis the same machine you’re on (loopback). You’re talking to a local service, not the internet.nc(netcat) opens simple TCP (or UDP) connections and lets you send/receive bytes via your terminal or pipes.- Newline matters. Most simple services expect your input to end with
\n.echo/printfadd it for you.
Further reading:
nc(netcat) manual- Localhost (Wikipedia)
- IP address (Wikipedia)
- Port (computer networking)
- What is a port? (short explainer)
- How Web Servers Work: Ports
- How Web Servers Work: TCP/IP basics
Solution
Way A — Interactive
-
Connect to the service
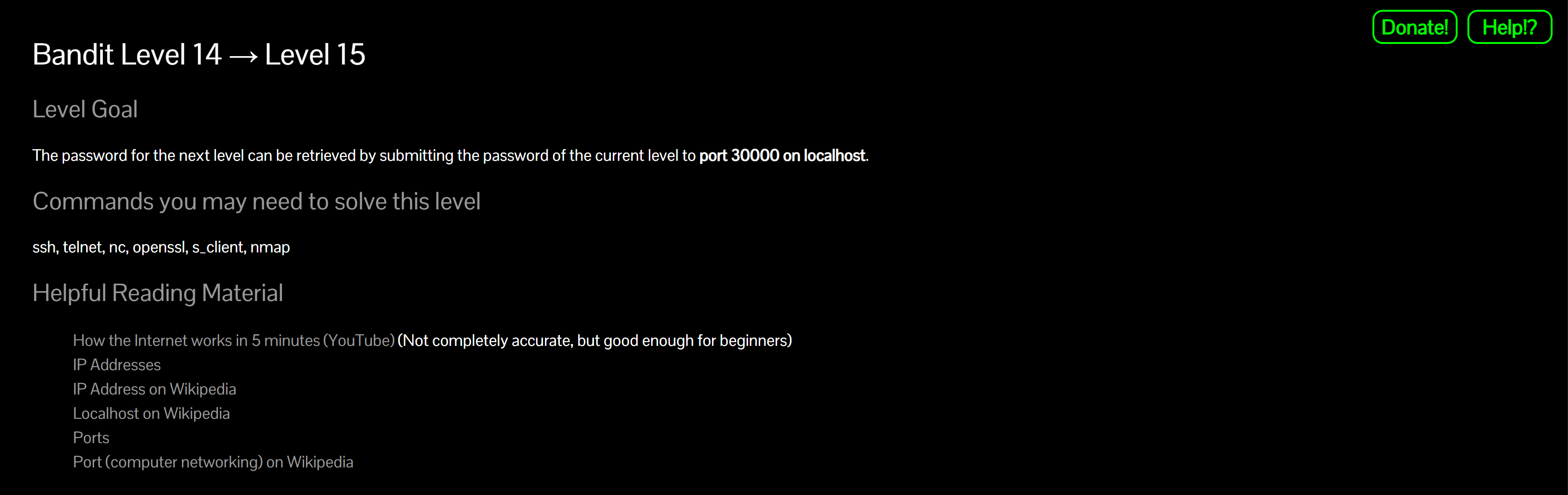
nc localhost 30000Why? Opens a TCP connection to the local service listening on 30000.
-
Paste the current level’s password and press Enter:
MU4VWeTyJk8ROof1qqmcBPaLh7lDCPvSWhy? The service validates your input and replies with the next password.
- Copy the returned password (no extra spaces/newlines).
-
Log into the next level (bandit15)
exit ssh bandit15@bandit.labs.overthewire.org -p 2220 # paste the password you just found when prompted
Way B — One-liner (copy-paste friendly)
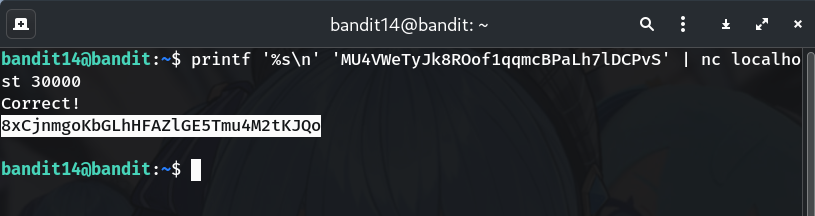
printf '%s\n' 'MU4VWeTyJk8ROof1qqmcBPaLh7lDCPvS' | nc localhost 30000
Why? Pipes the password with a newline into the TCP connection—fast and repeatable.
Password
This is the password I got in my run; if yours is different, copy the one shown in your terminal.
8xCjnmgoKbGLhHFAZlGE5Tmu4M2tKJQo
Troubleshooting
Connection refused→ You’re not on the Bandit box or the port is wrong. Ensure you’re SSH’d intobandit14and using 30000.- No response / times out → Make sure you sent a newline. Prefer
printf '%s\n' '...' | nc localhost 30000. - Garbled/SSL-looking output → This level uses plain TCP. (The SSL/TLS service shows up in the next level.)
Congrats 🎉 You used netcat to talk to a local TCP service and grabbed the Level 15 password. See you in Level 15 → 16!
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


