OverTheWire Bandit Level 13 → 14 tutorial!!
Login
Log in as bandit13 using the password you just obtained from Level 12 → 13.
ssh bandit13@bandit.labs.overthewire.org -p 2220
# password: FO5dwFsc0cbaIiH0h8J2eUks2vdTDwAn
Why? Each Bandit level is a different UNIX user. To solve 13 → 14 you must be logged in as
bandit13.
Task
The password for the next level is stored in /etc/bandit_pass/bandit14 and can only be read by user bandit14.
You’re given a private SSH key in your home directory to log into bandit14@localhost.
A little bit of Theory
- SSH key login (
-i) –ssh -i <private_key> user@hosttells SSH to use that private key to authenticate. localhost– hostname that always points to the machine you’re already on (the Bandit box). You’re SSH-ing frombandit13intobandit14on the same host.- First-time connect prompt – SSH will ask to trust the server fingerprint; answering
yesstores it in~/.ssh/known_hosts. - Permissions – private keys are usually restricted (e.g.,
chmod 600 key). If SSH complains about “unprotected private key file”, tighten the permissions.
Further reading:
- SSH/OpenSSH/Keys
sshmanual (Debian manpages)- SSH keys explained (ssh.com)
ssh_configoptions (Debian manpages)
Solution
-
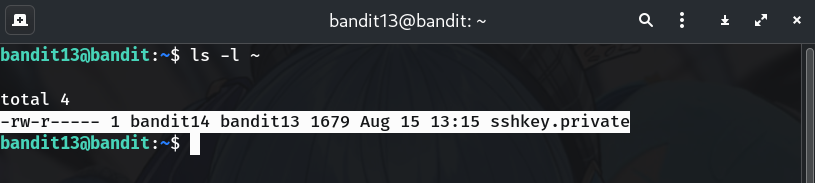
Verify the private key is present
ls -l ~Why? Confirms the provided key (usually
sshkey.private) exists and is readable.
-
(If needed) Restrict the key’s permissions
chmod 600 sshkey.privateWhy? Some SSH versions refuse to use keys that are group/world-readable.
-
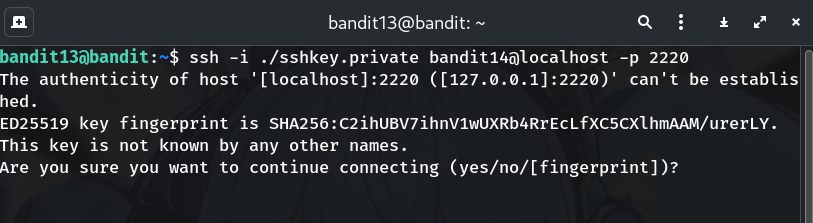
SSH into
bandit14on the same host using the keyssh -i ./sshkey.private bandit14@localhost -p 2220When asked about authenticity/fingerprint, type
yes.Why? You must become
bandit14to read the protected password file.
-
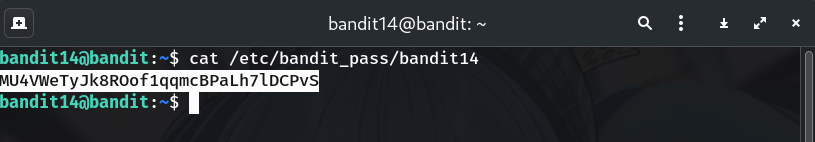
Read the password file as
bandit14cat /etc/bandit_pass/bandit14Why? Only
bandit14has permission to read it.
-
Copy the password (no trailing spaces/newlines).
-
Log into the next level (bandit14)
exit ssh bandit14@bandit.labs.overthewire.org -p 2220 # paste the password you just found when prompted
Password
This is the password I got in my run; if yours is different, copy the one shown in your terminal.
MU4VWeTyJk8ROof1qqmcBPaLh7lDCPvS
Troubleshooting
Permission denied (publickey)→ Make sure you used-i ./sshkey.private, the path is correct, and the key has strict perms (chmod 600 sshkey.private). Also keep-p 2220.- Host key prompt appears every time → That’s fine in Bandit’s ephemeral environment; just answer
yes. cat: /etc/bandit_pass/bandit14: Permission denied→ You’re notbandit14. Re-run the SSH command to switch users first.ssh: connect to host localhost port 2220: Connection refused→ Double-check the port (must be 2220) and that you’re on the Bandit host already.
Congrats 🎉 You used a private key to hop to the next user and grabbed the Level 14 password. See you in Level 14 → 15!
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


