OverTheWire Bandit Level 12 → 13 tutorial!!
Login
Log in as bandit12 using the password you just obtained from Level 11 → 12.
ssh bandit12@bandit.labs.overthewire.org -p 2220
# password: 7x16WNeHIi5YkIhWsfFIqoognUTyj9Q4
Why? Each Bandit level is a different UNIX user. To solve 12 → 13 you must be logged in as
bandit12.
Task
The password for the next level is in data.txt, which is a hexdump of a file that has been compressed multiple times. Recreate the original binary and keep unpacking until you reach readable text.
A little bit of Theory
- Hexdump ↔ binary
xxd -rconverts a hexdump back to raw bytes. - Use
fileto choose the right toolfilewill tell you if the data isgzip,bzip2, atararchive, or already plain text. - Common unpackers
gunzip(gzip),bunzip2(bzip2),tar xf(tar archives). - Work in
/tmpYou’ll rename and create lots of files;/tmpis writable and disposable.
Further reading:
- Hex dump (Wikipedia)
xxdmanual (Debian manpages)filemanual (Debian manpages)gzip/gunzip(Debian manpages)bzip2/bunzip2(Debian manpages)tar(Debian manpages)
Solution
Way A — Step-by-step (transparent)
-
Create a temp workspace & copy the data
WORKDIR=$(mktemp -d) cp ~/data.txt "$WORKDIR"/ cd "$WORKDIR" ls -lWhy? We’ll create/rename intermediate files. Working in
/tmpavoids cluttering your home and guarantees write permissions.
-
Rebuild the first binary from the hexdump
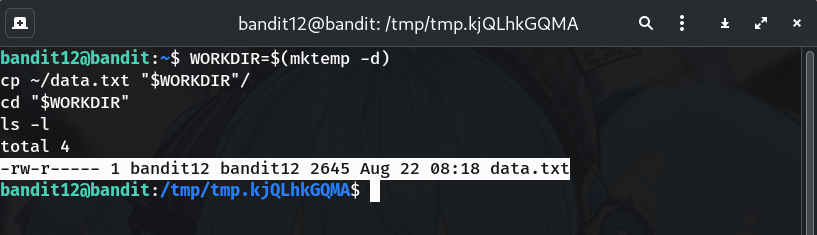
xxd -r data.txt data file dataWhy?
xxd -rturns the hex back into raw bytes. Thenfiletells you what format the bytes are in (gzip/bzip2/tar/text), so you know the next command to run.
-
Peel layers, guided by
fileRun
file data, apply the correct tool, rename the output back todata, and repeat:# If it's gzip-compressed: mv data data.gz && gunzip -f data.gz # If it's bzip2-compressed: mv data data.bz2 && bzip2 -df data.bz2 # If it's a tar archive (containing one file): mkdir t && tar xf data -C t && rm -f data && set -- t/* && mv "$1" data && rmdir t # Check again: file dataWhy? The file has multiple compression layers.
fileis the compass: it prevents guesswork and errors like “not in gzip format”. -
Read the plaintext
cat dataWhy? When
filesaysASCII text(or similar), you’ve reached the final content—the next level’s password. -
Copy the password (no extra spaces/newlines).
-
Log into the next level (bandit13)
exit ssh bandit13@bandit.labs.overthewire.org -p 2220 # paste the password you just found when prompted
Way B — Quick one-liner loop (“instant noodles”)
Paste this; it auto-detects and unwraps each layer until text appears:
WORKDIR=$(mktemp -d) && cp ~/data.txt "$WORKDIR"/ && cd "$WORKDIR"
xxd -r data.txt data
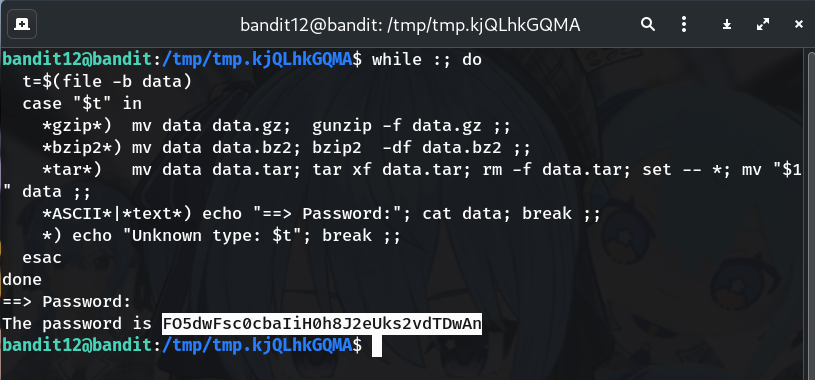
while :; do
t=$(file -b data)
case "$t" in
*gzip*) mv data data.gz; gunzip -f data.gz ;;
*bzip2*) mv data data.bz2; bzip2 -df data.bz2 ;;
*tar*) mv data data.tar; tar xf data.tar; rm -f data.tar; set -- *; mv "$1" data ;;
*ASCII*|*text*) echo "==> Password:"; cat data; break ;;
*) echo "Unknown type: $t"; break ;;
esac
done
Why? A tiny loop keeps the workflow consistent (the working file is always named data) and avoids manual mistakes across many layers.
Password
This is the password I got in my run; if yours is different, copy the one shown in your terminal.
FO5dwFsc0cbaIiH0h8J2eUks2vdTDwAn
Troubleshooting
gzip: not in gzip format/bzip2: data integrity errorYou used the wrong tool for this layer. Alwaysfile datafirst to identify the format.tar: This does not look like a tar archiveSame story—wrong tool or wrong step. Re-check withfile.- Multiple files after
tar xfUsels -ltto spot the newest file, thenmv <that-file> dataand continue the loop. - Lost track of filenames
Keep renaming the current working file back to
dataafter each step. It makes the loop (and your brain) much happier.
Congrats 🎉 You reconstructed a binary from a hexdump and peeled off multiple compression layers—on to bandit13!
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


