OverTheWire Bandit Level 1 → 2 tutorial!!
Login
Log in as bandit1 using the password you found in the previous level.
ssh bandit1@bandit.labs.overthewire.org -p 2220
# password: ZjLjTmM6FvvyRnrb2rfNWOZOTa6ip5If
Why? Each Bandit level is a different UNIX user. To solve 1 → 2, you must be logged in as
bandit1.
Task
The password for the next level is stored in a file named - (a single hyphen) located in the home directory of bandit1.
A little bit of Theory
- In many UNIX tools, a lone
-means “use standard input” (stdin) instead of a file path. Example:cat -waits for you to type, then echoes what you type. -
To read a file literally named
-, you must prevent the command from treating it as stdin or an option. Common ways:- Prefix with a path:
cat ./-orcat /home/bandit1/- - Use option terminator:
cat -- -(everything after--is a filename, not an option)
- Prefix with a path:
-
Quick reminders:
ls -lalists all files, including hidden ones, and shows ownership/permissions.- Absolute path
/home/bandit1/-always works regardless of your current directory.
Further reading:
Solution
-
Verify where you are
pwdWhy? Confirms you start in
/home/bandit1(the home directory). -
List files to see the target
ls -laWhy? Ensures the file named
-really exists and shows its permissions. -
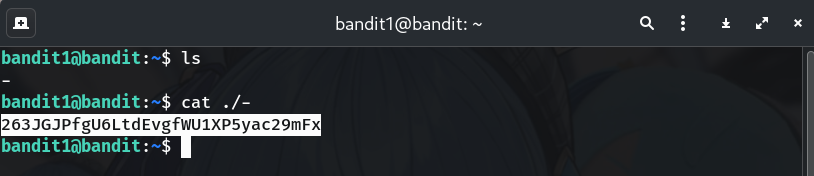
Read the file named
-safelycat ./-Why? Using
./-treats-as a literal filename in the current directory, avoiding the stdin special meaning.Alternatives (both valid):
cat -- - cat /home/bandit1/-
-
Copy the password (avoid trailing spaces/newlines).
-
Log into the next level (bandit2)
exit ssh bandit2@bandit.labs.overthewire.org -p 2220 # paste the password you just found when prompted
Password
This is the password shown in my run; if yours differs, copy the one from your own terminal output.
263JGJPfgU6LtdEvgfWU1XP5yac29mFx
Troubleshooting
cat: invalid option -- '-'→ Usecat ./-orcat -- -instead ofcat -.No such file or directory→ Confirm you’re in/home/bandit1or use the absolute path/home/bandit1/-.Permission denied→ Double-check you’re logged in asbandit1.
Congrats 🎉 You’ve extracted the password from the tricky - file and can now play as bandit2.
Thanks for reading!
Until next time — Otsumachi!! 💖☄️✨


